Security News > 2023 > April > Lazarus Subgroup Targeting Apple Devices with New RustBucket macOS Malware
A financially-motivated North Korean threat actor is suspected to be behind a new Apple macOS malware strain called RustBucket.
The Apple device management company attributed it to a threat actor known as BlueNoroff, a subgroup within the infamous Lazarus cluster that's also tracked under the monikers APT28, Nickel Gladstone, Sapphire Sleet, Stardust Chollima, and TA444.
BlueNoroff, unlike other constituent entities of the Lazarus Group, is known for its sophisticated cyber-enabled heists targeting the SWIFT system as well as cryptocurrency exchanges as part of an intrusion set tracked as CryptoCore.
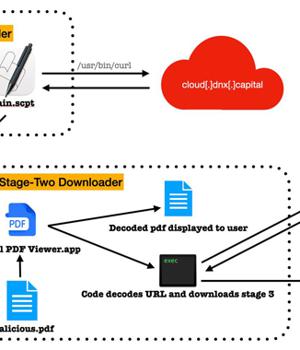
The macOS malware identified by Jamf masquerades as an "Internal PDF Viewer" application to activate the infection, although it bears noting that the success of the attack banks on the victim manually overriding Gatekeeper protections.
Lazarus Group is less a distinct outfit and more of an umbrella term for a mixture of state-sponsored and criminal hacking groups that sit within the Reconnaissance General Bureau, North Korea's primary foreign intelligence apparatus.
Around the same time, ESET detailed Lazarus Group's use of a Linux malware dubbed SimplexTea against the backdrop of a recurring social engineering campaign referred to as Operation Dream Job.
News URL
https://thehackernews.com/2023/04/lazarus-subgroup-targeting-apple.html
Related news
- XCSSET macOS malware returns with first new version since 2022 (source)
- Microsoft spots XCSSET macOS malware variant used for crypto theft (source)
- Microsoft Uncovers New XCSSET macOS Malware Variant with Advanced Obfuscation Tactics (source)
- The XCSSET info-stealing malware is back, targeting macOS users and devs (source)
- New FrigidStealer Malware Targets macOS Users via Fake Browser Updates (source)
- Seven Malicious Go Packages Found Deploying Malware on Linux and macOS Systems (source)
- Apple Backports Critical Fixes for 3 Recent 0-Days Impacting Older iOS and macOS Devices (source)