Security News > 2023 > March > NAPLISTENER: New Malware in REF2924 Group's Arsenal for Bypassing Detection
The threat group tracked as REF2924 has been observed deploying previously unseen malware in its attacks aimed at entities in South and Southeast Asia.
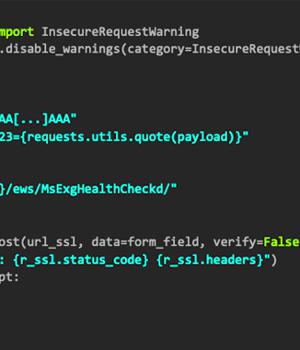
The malware, dubbed NAPLISTENER by Elastic Security Labs, is an HTTP listener programmed in C# and is designed to evade "Network-based forms of detection."
The threat actor's modus operandi suggests overlaps with another hacking group dubbed ChamelGang, which was documented by Russian cybersecurity company Positive Technologies in October 2021.
Attacks orchestrated by the group are said to have exploited internet-exposed Microsoft Exchange servers to deploy backdoors such as DOORME, SIESTAGRAPH, and ShadowPad. DOORME, an Internet Information Services backdoor module, provides remote access to a contested network and executes additional malware and tools.
The use of ShadowPad is noteworthy as it indicates a potential link to China-based hacking groups, which are known to utilize the malware in various campaigns over the years.
To this list of expanding malware arsenal used by REF2924 joins NAPLISTENER, which masquerades as a legitimate service Microsoft Distributed Transaction Coordinator in an attempt to fly under the radar and establish persistent access.
News URL
https://thehackernews.com/2023/03/new-naplistener-malware-used-by-ref2924.html