Security News > 2023 > March > Hackers Exploit Containerized Environments to Steal Proprietary Data and Software
A sophisticated attack campaign dubbed SCARLETEEL is targeting containerized environments to perpetrate theft of proprietary data and software.
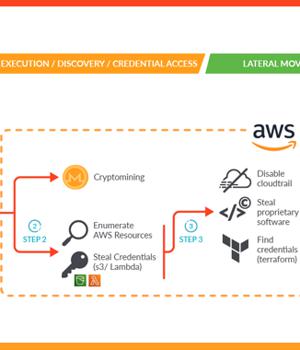
"The attacker exploited a containerized workload and then leveraged it to perform privilege escalation into an AWS account in order to steal proprietary software and credentials," Sysdig said in a new report.
The advanced cloud attack also entailed the deployment of crypto miner software, which the cybersecurity company said is either an attempt to generate illicit profits or a ploy to distract defenders and throw them off the trail.
Upon gaining a successful foothold, an XMRig crypto miner was launched and a bash script was used to obtain credentials that could be used to further burrow into the AWS cloud infrastructure and exfiltrate sensitive data.
"Either crypto mining was the attacker's initial goal and the goal changed once they accessed the victim's environment, or crypto mining was used as a decoy to evade the detection of data exfiltration," the company said.
The intrusion notably also disabled CloudTrail logs to minimize the digital footprint, preventing Sysdig from accessing additional evidence.
News URL
https://thehackernews.com/2023/03/hackers-exploit-containerized.html
Related news
- Hackers Exploit Severe PHP Flaw to Deploy Quasar RAT and XMRig Miners (source)
- Top 3 MS Office Exploits Hackers Use in 2025 – Stay Alert! (source)
- Hackers Exploit WordPress mu-Plugins to Inject Spam and Hijack Site Images (source)
- Russian Hackers Exploit CVE-2025-26633 via MSC EvilTwin to Deploy SilentPrism and DarkWisp (source)
- Hackers exploit WordPress plugin auth bypass hours after disclosure (source)
- Hackers exploit old FortiGate vulnerabilities, use symlink trick to retain limited access to patched devices (source)
- Russian Hackers Exploit Microsoft OAuth to Target Ukraine Allies via Signal and WhatsApp (source)
- Hackers Exploit Critical Craft CMS Flaws; Hundreds of Servers Likely Compromised (source)
- Hackers Exploit Samsung MagicINFO, GeoVision IoT Flaws to Deploy Mirai Botnet (source)
- Hackers exploit OttoKit WordPress plugin flaw to add admin accounts (source)