Security News > 2023 > February > Hackers Using Trojanized macOS Apps to Deploy Evasive Cryptocurrency Mining Malware
Trojanized versions of legitimate applications are being used to deploy evasive cryptocurrency mining malware on macOS systems.
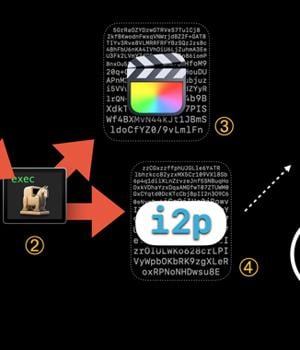
"This malware makes use of the Invisible Internet Project to download malicious components and send mined currency to the attacker's wallet," Jamf researchers Matt Benyo, Ferdous Saljooki, and Jaron Bradley said in a report shared with The Hacker News.
The malicious mining process banks on the user launching the pirated application, upon which the code embedded in the executable connects to an actor-controlled server over i2p to download the XMRig component.
Apple has taken steps to combat such abuse by subjecting notarized apps to more stringent Gatekeeper checks in macOS Ventura, thereby preventing tampered apps from being launched.
"On the other hand, macOS Ventura did not prevent the miner from executing," Jamf researchers noted.
"By the time the user receives the error message, that malware has already been installed."
News URL
https://thehackernews.com/2023/02/hackers-using-trojanized-macos-apps-to.html
Related news
- Cryptocurrency Miner and Clipper Malware Spread via SourceForge Cracked Software Listings (source)
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- State-Sponsored Hackers Weaponize ClickFix Tactic in Targeted Malware Campaigns (source)
- Chinese hackers target Russian govt with upgraded RAT malware (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Iran-Linked Hackers Target Israel with MURKYTOUR Malware via Fake Job Campaign (source)
- North Korean Hackers Spread Malware via Fake Crypto Firms and Job Interview Lures (source)
- Iranian Hackers Maintain 2-Year Access to Middle East CNI via VPN Flaws and Malware (source)
- Russian Hackers Using ClickFix Fake CAPTCHA to Deploy New LOSTKEYS Malware (source)
- Hacker steals $223 million in Cetus Protocol cryptocurrency heist (source)