Security News > 2023 > February > ESXiArgs Ransomware Hits Over 500 New Targets in European Countries
More than 500 hosts have been newly compromised en masse by the ESXiArgs ransomware strain, most of which are located in France, Germany, the Netherlands, the U.K., and Ukraine.
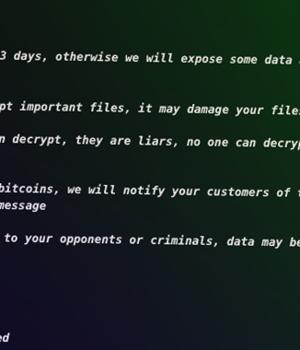
Some of the crucial differences between the two ransom notes include the use of an onion URL instead of a Tox chat ID, a Proton Mail address at the bottom of the note, and a lower ransom demand.
"Each variant of the ransom notes from October 2022 through February 2023 are strikingly similar in wording to the note of an earlier ransomware variant, Cheerscrypt, which gained notoriety in early 2022," researchers Mark Ellzey and Emily Austin said.
It's worth noting that ESXiArgs is suspected to be based on the leaked Babuk ransomware code, which also spawned other variants such as Cheerscrypt and PrideLocker last year.
The development comes less than a week after the threat actors returned with a new variant that tweaks the encryption method and the ransom note following the release of a decryptor to help recover infected systems.
The spike also coincides with an 87% year-over-year increase in ransomware attacks targeting industrial organizations in 2022, with 437 out of 605 attacks striking the manufacturing sector, per a new report from Dragos, in part fueled by continued evolution in ransomware-as-a-service models.
News URL
https://thehackernews.com/2023/02/esxiargs-ransomware-hits-over-500-new.html