Security News > 2023 > February > Critical Infrastructure at Risk from New Vulnerabilities Found in Wireless IIoT Devices
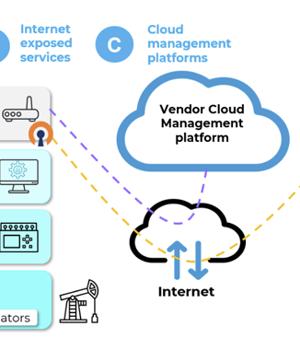
A set of 38 security vulnerabilities has been uncovered in wireless industrial internet of things devices from four different vendors that could pose a significant attack surface for threat actors looking to exploit operational technology environments.
"Threat actors can exploit vulnerabilities in Wireless IIoT devices to gain initial access to internal OT networks," Israeli industrial cybersecurity company Otorio said.
"They can use these vulnerabilities to bypass security layers and infiltrate target networks, putting critical infrastructure at risk or interrupting manufacturing."
The findings underscore how OT networks could be put at risk by making IIoT devices directly accessible on the internet, effectively creating a "Single point of failure" that can bypass all security protections.
As countermeasures, it's recommended to disable insecure encryption schemes, hide Wi-Fi network names, disable unused cloud management services, and take steps to prevent devices from being publicly accessible.
"The low complexity of exploit, combined with the broad potential impact, makes wireless IIoT devices and their cloud-based management platforms an enticing target for attackers looking to breach industrial environments," the company said.
News URL
https://thehackernews.com/2023/02/critical-infrastructure-at-risk-from.html
Related news
- US charges Chinese hackers linked to critical infrastructure breaches (source)
- CISA: Medusa ransomware hit over 300 critical infrastructure orgs (source)
- GitLab patches critical authentication bypass vulnerabilities (source)
- Ongoing Cyber Attacks Exploit Critical Vulnerabilities in Cisco Smart Licensing Utility (source)
- UAT-5918 Targets Taiwan's Critical Infrastructure Using Web Shells and Open-Source Tools (source)
- OpenAI now pays researchers $100,000 for critical vulnerabilities (source)
- Still Using an Older Version of iOS or iPadOS? Update Now to Patch These Critical Security Vulnerabilities (source)
- Adobe Patches 11 Critical ColdFusion Flaws Amid 30 Total Vulnerabilities Discovered (source)