Security News > 2023 > February > Iranian OilRig Hackers Using New Backdoor to Exfiltrate Data from Govt. Organizations
The Iranian nation-state hacking group known as OilRig has continued to target government organizations in the Middle East as part of a cyber espionage campaign that leverages a new backdoor to exfiltrate data.
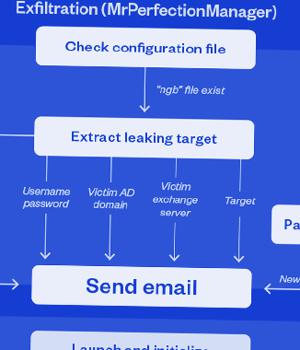
"The campaign abuses legitimate but compromised email accounts to send stolen data to external mail accounts controlled by the attackers," Trend Micro researchers Mohamed Fahmy, Sherif Magdy, and Mahmoud Zohdy said.
NET backdoor is its exfiltration routine, which involves using the stolen credentials to send electronic missives to actor-controlled email Gmail and Proton Mail addresses.
"The threat actors relay these emails via government Exchange Servers using vaild accounts with stolen passwords," the researchers said.
The growing number of malicious tools associated with OilRig indicates the threat actor's "Flexibility" to come up with new malware based on the targeted environments and the privileges possessed at a given stage of the attack.
"Despite the routine's simplicity, the novelty of the second and last stages also indicate that this entire routine can just be a small part of a bigger campaign targeting governments," the researchers said.
News URL
https://thehackernews.com/2023/02/iranian-oilrig-hackers-using-new.html
Related news
- Iranian Hackers Maintain 2-Year Access to Middle East CNI via VPN Flaws and Malware (source)
- Türkiye Hackers Exploited Output Messenger Zero-Day to Drop Golang Backdoors on Kurdish Servers (source)
- Chinese Hackers Deploy MarsSnake Backdoor in Multi-Year Attack on Saudi Organization (source)
- Iranian Hacker Pleads Guilty in $19 Million Robbinhood Ransomware Attack on Baltimore (source)