Security News > 2022 > December > Iranian Hackers Strike Diamond Industry with Data-Wiping Malware in Supply-Chain Attack
An Iranian advanced persistent threat actor known as Agrius has been attributed as behind a set of data wiper attacks aimed at diamond industries in South Africa, Israel, and Hong Kong.
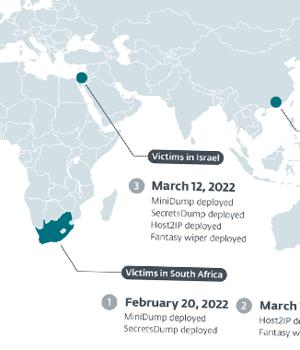
The wiper, codenamed Fantasy by ESET, is believed to have been delivered via a supply chain attack targeting an Israeli software suite developer as part of a campaign that began in February 2022.
"The Fantasy wiper is built on the foundations of the previously reported Apostle wiper but does not attempt to masquerade as ransomware, as Apostle originally did, ESET researcher Adam Burgher disclosed in a Thursday analysis."Instead, it goes right to work wiping data.
Agrius subsequently initiated the wiping attack via Fantasy on March 12, 2022, before striking other companies in Israel and Hong Kong on the same date.
The name of the Israeli company that fell victim to the supply chain attack was not disclosed by ESET, but evidence points to it being Rubinstein Software, which markets an enterprise resource planning solution called Fantasy that's used for jewelry stock management.
The APT33 hacking group, which is suspected of operating at the behest of the Iranian government, is said to have been behind multiple attacks that used the Shamoon wiper against targets located in the Middle East.
News URL
https://thehackernews.com/2022/12/iranian-hackers-strike-diamond-industry.html
Related news
- Bybit Hack Traced to Safe{Wallet} Supply Chain Attack Exploited by North Korean Hackers (source)
- ⚡ THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- North Korean Hackers Target Freelance Developers in Job Scam to Deploy Malware (source)
- Chinese hackers use custom malware to spy on US telecom networks (source)
- New Linux Malware ‘Auto-Color’ Grants Hackers Full Remote Access to Compromised Systems (source)
- Silver Fox APT Uses Winos 4.0 Malware in Cyber Attacks Against Taiwanese Organizations (source)
- Hackers Exploit Paragon Partition Manager Driver Vulnerability in Ransomware Attacks (source)
- Hackers Exploit AWS Misconfigurations to Launch Phishing Attacks via SES and WorkMail (source)
- Suspected Iranian Hackers Used Compromised Indian Firm's Email to Target U.A.E. Aviation Sector (source)