Security News > 2022 > November > Chinese Hackers Using New Stealthy Infection Chain to Deploy LODEINFO Malware
The Chinese state-sponsored threat actor known as Stone Panda has been observed employing a new stealthy infection chain in its attacks aimed at Japanese entities.
The latest set of attacks, observed between March and June 2022, involve the use of a bogus Microsoft Word file and a self-extracting archive file in RAR format propagated via spear-phishing emails, leading to the execution of a backdoor called LODEINFO. While the maldoc requires users to enable macros to activate the killchain, the June 2022 campaign was found to drop this method in favor of an SFX file that, when executed, displays a harmless decoy Word document to conceal the malicious activities.
The abuse of the security application aside, Kaspersky said it also discovered in June 2022 another initial infection method wherein a password-protected Microsoft Word file acted as a conduit to deliver a fileless downloader dubbed DOWNIISSA upon enabling macros.
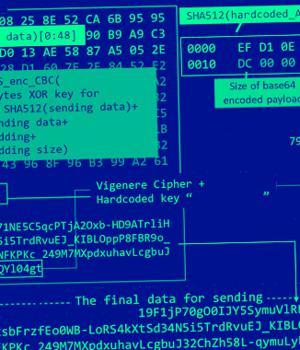
DOWNIISSA is configured to communicate with a hard-coded remote server, using it to retrieve an encrypted BLOB payload of LODEINFO, a backdoor capable of executing arbitrary shellcode, take screenshots, and exfiltrate files back to the server.
"LODEINFO malware is updated very frequently and continues to actively target Japanese organizations," the researchers concluded.
"The updated TTPs and improvements in LODEINFO and related malware indicate that the attacker is particularly focused on making detection, analysis and investigation harder for security researchers."
News URL
https://thehackernews.com/2022/11/chinese-hackers-using-new-stealthy.html
Related news
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- Chinese hackers target Russian govt with upgraded RAT malware (source)
- North Korean Hackers Deploy BeaverTail Malware via 11 Malicious npm Packages (source)
- State-Sponsored Hackers Weaponize ClickFix Tactic in Targeted Malware Campaigns (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Iran-Linked Hackers Target Israel with MURKYTOUR Malware via Fake Job Campaign (source)
- North Korean Hackers Spread Malware via Fake Crypto Firms and Job Interview Lures (source)
- Chinese Hackers Abuse IPv6 SLAAC for AitM Attacks via Spellbinder Lateral Movement Tool (source)
- Iranian Hackers Maintain 2-Year Access to Middle East CNI via VPN Flaws and Malware (source)
- Russian Hackers Using ClickFix Fake CAPTCHA to Deploy New LOSTKEYS Malware (source)