Security News > 2022 > October > SideWinder APT Using New WarHawk Backdoor to Target Entities in Pakistan
SideWinder, a prolific nation-state actor mainly known for targeting Pakistan military entities, compromised the official website of the National Electric Power Regulatory Authority to deliver a tailored malware called WarHawk.
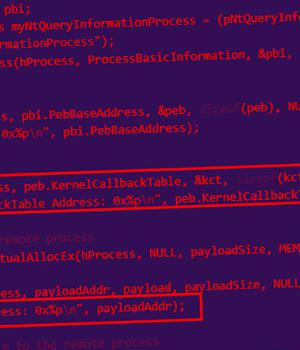
"The newly discovered WarHawk backdoor contains various malicious modules that deliver Cobalt Strike, incorporating new TTPs such as KernelCallBackTable injection and Pakistan Standard Time zone check in order to ensure a victorious campaign," Zscaler ThreatLabz said.
The September campaign spotted by Zscaler entails the use of a weaponized ISO file hosted on NEPRA's website to activate a killchain that leads to the deployment of the WarHawk malware, with the artifact also acting as a decoy to hide the malicious activity by displaying a legitimate advisory issued by the Cabinet Division of Pakistan on July 27, 2022.
Also deployed as a second-stage payload using the aforementioned command execution module is a Cobalt Strike Loader, which validates the host's time zone to confirm it matches the Pakistan Standard Time, failing which the process is terminated.
Per the cybersecurity company, the attack campaign's connections to the SideWinder APT stem from the reuse of network infrastructure that has been identified as used by the group in prior espionage-focused activities against Pakistan.
"The SideWinder APT Group is continuously evolving their tactics and adding new malware to their arsenal in order to carry out successful espionage attack campaigns against their targets," the researchers concluded.
News URL
https://thehackernews.com/2022/10/sidewinder-apt-using-new-warhawk.html