Security News > 2022 > October > BazarCall Call Back Phishing Attacks Constantly Evolving Its Social Engineering Tactics
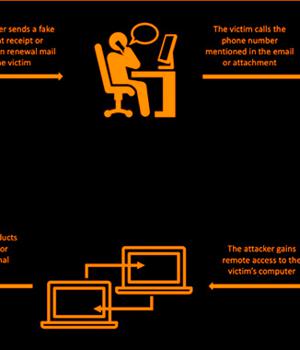
The operators behind the BazaCall call back phishing method have continued to evolve with updated social engineering tactics to deploy malware on targeted networks.
Primary targets of the latest attack waves include the U.S., Canada, China, India, Japan, Taiwan, the Philippines, and the U.K. BazaCall, also called BazarCall, first gained popularity in 2020 for its novel approach of distributing the BazarBackdoor malware by manipulating potential victims into calling a phone number specified in decoy email messages.
The messages also urge them to contact their support desk to cancel the plan, or risk getting automatically charged for the premium version of the software.
The ultimate goal of the attacks is to enable remote access to the endpoint under the guise of terminating the supposed subscription or installing a security solution to rid the machine of malware, effectively paving the way for follow-on activities.
Another tactic embraced by the operators involves masquerading as incident responders in PayPal-themed campaigns to deceive the caller into thinking that their accounts were accessed from eight or more devices spread across random locations across the world.
The development comes as at least three different spinoff groups from the Conti ransomware cartel have embraced the call back phishing technique as an initial intrusion vector to breach enterprise networks.
News URL
https://thehackernews.com/2022/10/bazarcall-callback-phishing-attacks.html
Related news
- Phishing platform 'Lucid' behind wave of iOS, Android SMS attacks (source)
- iOS devices face twice the phishing attacks of Android (source)
- Windows NTLM hash leak flaw exploited in phishing attacks on governments (source)
- Three Reasons Why the Browser is Best for Stopping Phishing Attacks (source)
- Phishing detection is broken: Why most attacks feel like a zero day (source)
- DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack (source)
- Low-tech phishing attacks are gaining ground (source)
- MintsLoader Drops GhostWeaver via Phishing, ClickFix — Uses DGA, TLS for Stealth Attacks (source)
- How cybercriminals exploit psychological triggers in social engineering attacks (source)
- Focused Phishing: Attack Targets Victims With Trusted Sites and Live Validation (source)