Security News > 2022 > August > Okta Hackers Behind Twilio and Cloudflare Attacks Hit Over 130 Organizations
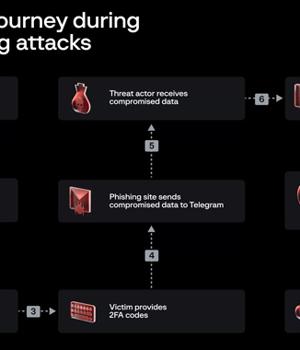
The threat actor behind the attacks on Twilio and Cloudflare earlier this month has been linked to a broader phishing campaign aimed at 136 organizations that resulted in a cumulative compromise of 9,931 accounts.
The activity has been condemned 0ktapus by Group-IB because the initial goal of the attacks was to "Obtain Okta identity credentials and two-factor authentication codes from users of the targeted organizations."
Calling the attacks well designed and executed, the Singapore-headquartered company said the adversary singled out employees of companies that are customers of identity services provider Okta.
"Furthermore, once the attackers compromised an organization they were quickly able to pivot and launch subsequent supply chain attacks, indicating that the attack was planned carefully in advance."
What's notable about the attacks is the use of an actor-controlled Telegram channel to drop the compromised information, which included user credentials, email addresses, and multi-factor authentication codes.
"While the threat actor may have been lucky in their attacks it is far more likely that they carefully planned their phishing campaign to launch sophisticated supply chain attacks," Group-IB analyst Roberto Martinez said.
News URL
https://thehackernews.com/2022/08/okta-hackers-behind-twilio-and.html
Related news
- New ‘Rules File Backdoor’ Attack Lets Hackers Inject Malicious Code via AI Code Editors (source)
- TechRepublic EXCLUSIVE: New Ransomware Attacks are Getting More Personal as Hackers ‘Apply Psychological Pressure” (source)
- Hackers Repurpose RansomHub's EDRKillShifter in Medusa, BianLian, and Play Attacks (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- North Korean hackers adopt ClickFix attacks to target crypto firms (source)
- Russian hackers attack Western military mission using malicious drive (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Hackers abuse Zoom remote control feature for crypto-theft attacks (source)
- DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack (source)
- Lazarus hackers breach six companies in watering hole attacks (source)