Security News > 2022 > May > New Saitama backdoor Targeted Official from Jordan's Foreign Ministry
A spear-phishing campaign targeting Jordan's foreign ministry has been observed dropping a new stealthy backdoor dubbed Saitama.
The newly observed phishing message contains a weaponized Microsoft Excel document, opening which prompts a potential victim to enable macros, leading to the execution of a malicious Visual Basic Application macro that drops the malware payload. Furthermore, the macro takes care of establishing persistence for the implant by adding a scheduled task that repeats every four hours.
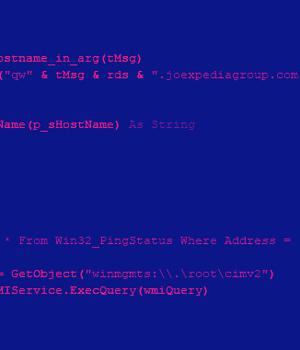
A.NET-based binary, Saitama leverages the DNS protocol for its command-and-control communications as part of an effort to disguise its traffic, while employing a "Finite-state machine" approach to executing commands received from a C2 server.
"In the end, this basically means that this malware is receiving tasks inside a DNS response," Gutierrez explained.
DNS tunneling, as it's called, makes it possible to encode the data of other programs or protocols in DNS queries and responses.
"Perhaps to avoid triggering any behavioral detections, this malware also does not create any persistence methods. Instead, it relies on the Excel macro to create persistence by way of a scheduled task."
News URL
https://thehackernews.com/2022/05/new-saitama-backdoor-targeted-official.html