Security News > 2022 > May > Hackers Using PrivateLoader PPI Service to Distribute New NetDooka Malware
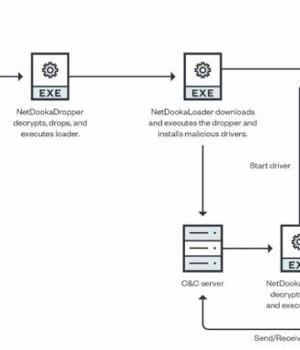
A pay-per-install malware service known as PrivateLoader has been spotted distributing a "Fairly sophisticated" framework called NetDooka, granting attackers complete control over the infected devices.
PrivateLoader, as documented by Intel 471 in February 2022, functions as a downloader responsible for downloading and installing additional malware onto the infected system, including SmokeLoader, RedLine Stealer, Vidar, Raccoon, GCleaner, and Anubis.
Featuring anti-analysis techniques, PrivateLoader is written in the C++ programming language and is said to be in active development, with the downloader malware family gaining traction among multiple threat actors.
"The loader will likely continue to be updated with new features and functionality to evade detection and effectively deliver second-stage malware payloads."
The newly observed set of infections involving the NetDooka framework commences with PrivateLoader acting as a conduit to deploy a dropper component, which then decrypts and executes a loader that, in turn, retrieves another dropper from a remote server to install a full-featured trojan as well as a kernel driver.
"PPI malware services allow malware creators to easily deploy their payloads," Zahravi and Froes concluded.
News URL
https://thehackernews.com/2022/05/hackers-using-privateloader-ppi-service.html
Related news
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- State-Sponsored Hackers Weaponize ClickFix Tactic in Targeted Malware Campaigns (source)
- Chinese hackers target Russian govt with upgraded RAT malware (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Iran-Linked Hackers Target Israel with MURKYTOUR Malware via Fake Job Campaign (source)
- North Korean Hackers Spread Malware via Fake Crypto Firms and Job Interview Lures (source)
- Iranian Hackers Maintain 2-Year Access to Middle East CNI via VPN Flaws and Malware (source)
- Russian Hackers Using ClickFix Fake CAPTCHA to Deploy New LOSTKEYS Malware (source)
- Hackers Use TikTok Videos to Distribute Vidar and StealC Malware via ClickFix Technique (source)
- Hackers Use Fake VPN and Browser NSIS Installers to Deliver Winos 4.0 Malware (source)