Security News > 2022 > May > Chinese Hackers Caught Stealing Intellectual Property from Multinational Companies
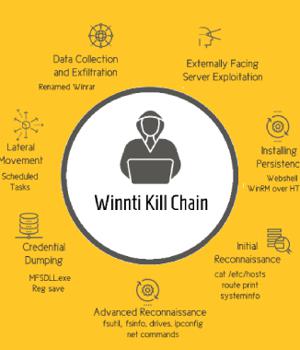
Dubbed "Operation CuckooBees" by Israeli cybersecurity company Cybereason, the massive intellectual property theft operation enabled the threat actor to exfiltrate hundreds of gigabytes of information.
"The attackers targeted intellectual property developed by the victims, including sensitive documents, blueprints, diagrams, formulas, and manufacturing-related proprietary data," the researchers said.
"The group's intent is towards theft of intellectual property from organizations in developed economies, and with moderate confidence that this is on behalf of China to support decision making in a range of Chinese economic sectors," Secureworks notes in a threat profile of the actor.
The data harvesting is facilitated by means of a modular loader called Spyder, which is used to decrypt and load additional payloads.
Crucial to the stealthiness of the campaign is the use of "Rarely seen" techniques such as the abuse of Windows Common Log File System mechanism to stash the payloads, enabling the hacking group to conceal their payloads and evade detection by traditional security products.
"Winnti is one of the most industrious groups operating on behalf of Chinese state-aligned interests," Cybereason said.
News URL
https://thehackernews.com/2022/05/chinese-hackers-caught-stealing.html
Related news
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- Chinese hackers target Russian govt with upgraded RAT malware (source)
- Chinese Hackers Abuse IPv6 SLAAC for AitM Attacks via Spellbinder Lateral Movement Tool (source)
- Chinese Hackers Exploit SAP RCE Flaw CVE-2025-31324, Deploy Golang-Based SuperShell (source)
- Chinese hackers behind attacks targeting SAP NetWeaver servers (source)
- Chinese Hackers Deploy MarsSnake Backdoor in Multi-Year Attack on Saudi Organization (source)
- Chinese Hackers Exploit Ivanti EPMM Bugs in Global Enterprise Network Attacks (source)
- Chinese hackers breach US local governments using Cityworks zero-day (source)
- Ivanti EPMM flaw exploited by Chinese hackers to breach govt agencies (source)
- Chinese Hackers Exploit Trimble Cityworks Flaw to Infiltrate U.S. Government Networks (source)