Security News > 2022 > May > AvosLocker Ransomware Variant Using New Trick to Disable Antivirus Protection
Cybersecurity researchers have disclosed a new variant of the AvosLocker ransomware that disables antivirus solutions to evade detection after breaching target networks by taking advantage of unpatched security flaws.
"This is the first sample we observed from the U.S. with the capability to disable a defense solution using a legitimate Avast Anti-Rootkit Driver file," Trend Micro researchers, Christoper Ordonez and Alvin Nieto, said in a Monday analysis.
The ransomware is also capable of scanning multiple endpoints for the Log4j vulnerability using Nmap NSE script."
AvosLocker, one of the newer ransomware families to fill the vacuum left by REvil, has been linked to a number of attacks that targeted critical infrastructure in the U.S., including financial services and government facilities.
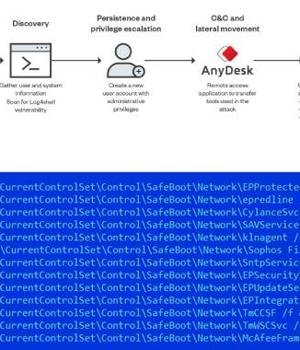
This includes retrieving an ASPX web shell from the server as well as an installer for the AnyDesk remote desktop software, the latter of which is used to deploy additional tools to scan the local network, terminate security software, and drop the ransomware payload. Some of the components copied to the infected endpoint are a Nmap script to scan the network for the Log4Shell remote code execution flaw and a mass deployment tool called PDQ to deliver a malicious batch script to multiple endpoints.
The batch script, for its part, is equipped with a wide range of capabilities that allows it to disable Windows Update, Windows Defender, and Windows Error Recovery, in addition to preventing safe boot execution of security products, creating a new admin account, and launching the ransomware binary.
News URL
https://thehackernews.com/2022/05/avoslocker-ransomware-variant-using-new.html