Security News > 2022 > April > New Octo Banking Trojan Spreading via Fake Apps on Google Play Store
A number of rogue Android apps that have been cumulatively installed from the official Google Play Store more than 50,000 times are being used to target banks and other financial entities.
Like other Android banking trojans, the rogue apps are nothing more than droppers, whose primary function is to deploy the malicious payload embedded within them.
These apps, which pose as Play Store app installer, screen recording, and financial apps, are "Powered by inventive distribution schemes," distributing them through the Google Play store and via fraudulent landing pages that purportedly alert users to download a browser update.
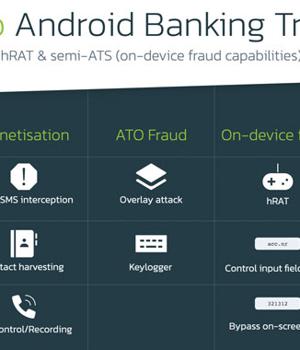
Other notable features of Octo include logging keystrokes, carrying out overlay attacks on banking apps to capture credentials, harvesting contact information, and persistence measures to prevent uninstallation and evade antivirus engines.
The findings come close on the heels of the discovery of a separate Android bankbot named GodFather - sharing overlaps with the Cereberus and Medusa banking trojans - that has been observed targeting banking users in Europe under the guise of the default Settings app to transfer funds and steal SMS messages, among others.
On top of that, a new analysis published by AppCensus found 11 apps with more than 46 million installations that were implanted with a third-party SDK named Coelib that made it possible to capture clipboard content, GPS data, email addresses, phone numbers, and even the user's modem router MAC address and network SSID..
News URL
https://thehackernews.com/2022/04/new-octo-banking-trojan-spreading-via.html