Security News > 2022 > March > Iranian Hackers Targeting Turkey and Arabian Peninsula in New Malware Campaign
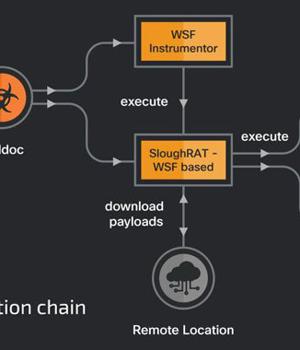
The Iranian state-sponsored threat actor known as MuddyWater has been attributed to a new swarm of attacks targeting Turkey and the Arabian Peninsula with the goal of deploying remote access trojans on compromised systems.
"The MuddyWater supergroup is highly motivated and can use unauthorized access to conduct espionage, intellectual property theft, and deploy ransomware and destructive malware in an enterprise," Cisco Talos researchers Asheer Malhotra, Vitor Ventura, and Arnaud Zobec said in a report published today.
In January 2022, the U.S. Cyber Command attributed the actor to the country's Ministry of Intelligence and Security.
The latest campaigns undertaken by the hacking crew involve the use of malware-laced documents delivered via phishing messages to deploy a remote access trojan called SloughRAT capable of executing arbitrary code and commands received from its command-and-control servers.
The latest set of intrusions marks a continuation of a November 2021 campaign that struck Turkish private organizations and governmental institutions with PowerShell-based backdoors to gather information from its victims, even as it exhibits overlaps with another campaign that took place in March 2021.
The commonalities in tactics and techniques adopted by the operators have raised the possibility that these attacks are "Distinct, yet related, clusters of activity," with the campaigns leveraging a "Broader TTP-sharing paradigm, typical of coordinated operational teams," the researchers noted.
News URL
https://thehackernews.com/2022/03/iranian-hackers-targeting-turkey-and.html
Related news
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- North Korean Hackers Deploy BeaverTail Malware via 11 Malicious npm Packages (source)
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- State-Sponsored Hackers Weaponize ClickFix Tactic in Targeted Malware Campaigns (source)
- Chinese hackers target Russian govt with upgraded RAT malware (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Iran-Linked Hackers Target Israel with MURKYTOUR Malware via Fake Job Campaign (source)
- North Korean Hackers Spread Malware via Fake Crypto Firms and Job Interview Lures (source)