Security News > 2022 > March > New Linux Kernel cgroups Vulnerability Could Let Attackers Escape Container
Details have emerged about a now-patched high-severity vulnerability in the Linux kernel that could potentially be abused to escape a container in order to execute arbitrary commands on the container host.
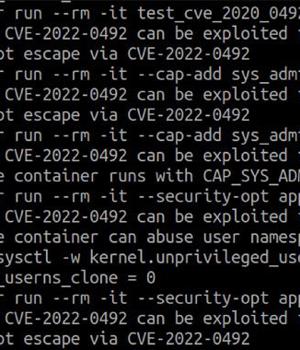
The shortcoming resides in a Linux kernel feature called control groups, also referred to as cgroups version 1, which allows processes to be organized into hierarchical groups, effectively making it possible to limit and monitor the usage of resources such as CPU, memory, disk I/O, and network.
"The issue stands out as one of the simplest Linux privilege escalations discovered in recent times: The Linux kernel mistakenly exposed a privileged operation to unprivileged users," Unit 42 researcher Yuval Avrahami said in a report published this week.
It's worth noting that only processes with "Root" privileges can write to the file, meaning that the vulnerability solely permits root processes to escalate privileges.
Then in November 2021, cloud security firm Aqua disclosed details of a cryptocurrency mining campaign that used the exact same container escape technique to drop the XMRig coin miner on infected hosts, making it the first recorded instance of real-world exploitation.
"CVE-2022-0492 marks another Linux vulnerability that can be exploited for container escape," Avrahami concluded.
News URL
https://thehackernews.com/2022/03/new-linux-kernel-cgroups-vulnerability.html
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2022-03-03 | CVE-2022-0492 | Missing Authorization vulnerability in multiple products A vulnerability was found in the Linux kernel’s cgroup_release_agent_write in the kernel/cgroup/cgroup-v1.c function. | 7.8 |