Security News > 2022 > February > New CapraRAT Android Malware Targets Indian Government and Military Personnel
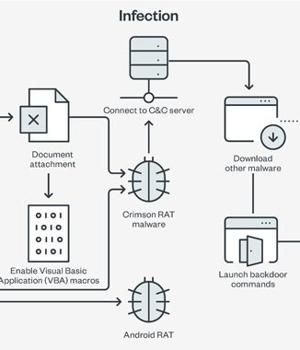
A politically motivated advanced persistent threat group has expanded its malware arsenal to include a new remote access trojan in its espionage attacks aimed at Indian military and diplomatic entities.
Called CapraRAT by Trend Micro, the implant is an Android RAT that exhibits a high "Degree of crossover" with another Windows malware known as CrimsonRAT that's associated with Earth Karkaddan, a threat actor that's also tracked under the monikers APT36, Operation C-Major, PROJECTM, Mythic Leopard, and Transparent Tribe.
The first concrete signs of APT36's existence appeared in 2016 as the group began distributing information-stealing malware through phishing emails with malicious PDF attachments targeting Indian military and government personnel.
The new addition to its toolset is yet another custom Android RAT that's deployed by means of phishing links.
In May 2018, human rights defenders in Pakistan were targeted by Android spyware named StealthAgent to intercept phone calls and messages, siphon photos, and track their whereabouts.
Attack campaigns mounted by Transparent Tribe involved leveraging military-themed lures to drop a modified version of the AhMyth Android RAT that masqueraded as a porn-related app and a fake version of the Aarogya Setu COVID-19 tracking app.
News URL
https://thehackernews.com/2022/02/new-caprarat-android-malware-targets.html
Related news
- North Korea’s ScarCruft Deploys KoSpy Malware, Spying on Android Users via Fake Utility Apps (source)
- New Android malware uses Microsoft’s .NET MAUI to evade detection (source)
- APT36 Spoofs India Post Website to Infect Windows and Android Users with Malware (source)
- Android Malware Exploits a Microsoft-Related Security Blind Spot to Avoid Detection (source)
- New Crocodilus malware steals Android users’ crypto wallet keys (source)
- Counterfeit Android devices found preloaded With Triada malware (source)
- Triada Malware Preloaded on Counterfeit Android Phones Infects 2,600+ Devices (source)
- SpyNote, BadBazaar, MOONSHINE Malware Target Android and iOS Users via Fake Apps (source)
- New Android malware steals your credit cards for NFC relay attacks (source)
- SuperCard X Android Malware Enables Contactless ATM and PoS Fraud via NFC Relay Attacks (source)