Security News > 2022 > February > Researchers Uncover New Iranian Hacking Campaign Targeting Turkish Users
Details have emerged about a previously undocumented malware campaign undertaken by the Iranian MuddyWater advanced persistent threat group targeting Turkish private organizations and governmental institutions.
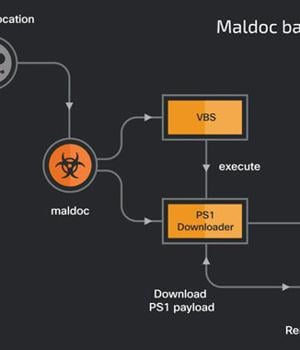
"This campaign utilizes malicious PDFs, XLS files and Windows executables to deploy malicious PowerShell-based downloaders acting as initial footholds into the target's enterprise," Cisco Talos researchers Asheer Malhotra and Vitor Ventura said in a newly published report.
These maldocs masqueraded as legitimate documents from the Turkish Health and Interior Ministries, with the attacks starting by executing malicious macros embedded in them to propagate the infection chain and drop PowerShell scripts to the compromised system.
A new addition to the group's arsenal of tactics, techniques and procedures is the use of canary tokens in the macro code, a mechanism the researchers suspect is being used to track successful infection of targets, thwart analysis, and detect if the payload servers are being blocked at the other end.
What's more, the researchers said they found at least two different versions of the executable delivered by the adversary targeting the telecommunications sector in Armenia in June 2021 and Pakistani entities in August 2021, raising the possibility that MuddyWater may have engaged in multiple attacks as part of one long continuous campaign.
"With new techniques such as canary tokens used to track successful infection of targets, MuddyWater has proven their adaptability and unwillingness to refrain themselves from attacking other nations."
News URL
https://thehackernews.com/2022/01/researchers-uncover-new-iranian-hacking.html