Security News > 2021 > November > Hackers Targeting Myanmar Use Domain Fronting to Hide Malicious Activities
A malicious campaign has been found leveraging a technique called domain fronting to hide command-and-control traffic by leveraging a legitimate domain owned by the Myanmar government to route communications to an attacker-controlled server with the goal of evading detection.
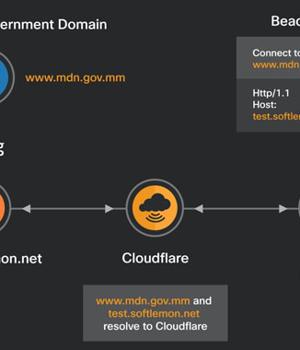
The threat, which was observed in September 2021, deployed Cobalt Strike payloads as a stepping stone for launching further attacks, with the adversary using a domain associated with the Myanmar Digital News network, a state-owned digital newspaper, as a front for their Beacons.
"While the default C2 domain was specified as www[.]mdn[.]gov[.]mm, the beacon's traffic was redirected to the de-facto C2 test[.]softlemon[.]net via HTTP Get and POST metadata specified in the beacon's configuration," the researchers said.
"The DNS request for the initial host resolves to a Cloudflare-owned IP address that allows the attacker to employ domain fronting and send the traffic to the actual C2 host test[.]softlemon[.]net, also proxied by Cloudflare."
"Domain fronting can be achieved with a redirect between the malicious server and the target. Malicious actors may misuse various content delivery networks to set up redirects of serving content to the content served by attacker-controlled C2 hosts," the researchers said.
"Defenders should monitor their network traffic even to high reputation domains in order to identify the potential domain fronting attacks with Cobalt Strike and other offensive tools."
News URL
https://thehackernews.com/2021/11/hackers-targeting-myanmar-use-domain.html