Security News > 2021 > August > Microsoft Warns of Widespread Phishing Attacks Using Open Redirects
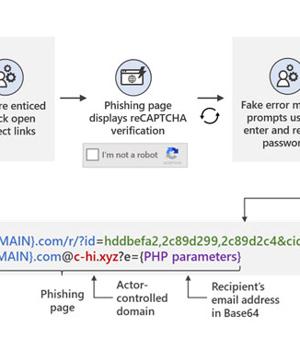
Microsoft is warning of a widespread credential phishing campaign that leverages open redirector links in email communications as a vector to trick users into visiting malicious websites while effectively bypassing security software.
"Attackers combine these links with social engineering baits that impersonate well-known productivity tools and services to lure users into clicking," Microsoft 365 Defender Threat Intelligence Team said in a report published this week.
Although redirect links in email messages serve a vital tool to take recipients to third-party websites or track click rates and measure the success of sales and marketing campaigns, the same technique can be abused by adversaries to redirect such links to their own infrastructure, at the same time keeping the trusted domain in the full URL intact to evade analysis by anti-malware engines, even when users attempt to hover on links to check for any signs of suspicious content.
The redirect URLs embedded in the message are set up using a legitimate service in an attempt to lead potential victims to phishing sites, while the final actor-controlled domains contained in the link leverage the top-level domains.
Microsoft said it observed at least 350 unique phishing domains as part of the campaign - an attempt to obscure detection - underscoring the campaign's effective use of convincing social engineering lures that purport to be notification messages from apps like Office 365 and Zoom, well-crafted detection evasion technique, and a durable infrastructure to carry out the attacks.
To give the attack a veneer of authenticity, clicking the specially-crafted links redirects the users to a malicious landing page that employs Google reCAPTCHA to block any dynamic scanning attempts.
News URL
Related news
- Microsoft Warns of ClickFix Phishing Campaign Targeting Hospitality Sector via Fake Booking[.]com Emails (source)
- Ukrainian military targeted in new Signal spear-phishing attacks (source)
- Hidden Threats: How Microsoft 365 Backups Store Risks for Future Attacks (source)
- Microsoft’s new AI agents take on phishing, patching, alert fatigue (source)
- After Detecting 30B Phishing Attempts, Microsoft Adds Even More AI to Its Security Copilot (source)
- Phishing platform 'Lucid' behind wave of iOS, Android SMS attacks (source)
- Microsoft Warns of Tax-Themed Email Attacks Using PDFs and QR Codes to Deliver Malware (source)
- iOS devices face twice the phishing attacks of Android (source)
- Microsoft Defender will isolate undiscovered endpoints to block attacks (source)
- Tycoon2FA phishing kit targets Microsoft 365 with new tricks (source)