Security News > 2021 > July > Hackers Spread BIOPASS Malware via Chinese Online Gambling Sites
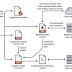
Cybersecurity researchers are warning about a new malware that's striking online gambling companies in China via a watering hole attack to deploy either Cobalt Strike beacons or a previously undocumented Python-based backdoor called BIOPASS RAT that takes advantage of Open Broadcaster Software Studio's live-streaming app to capture the screen of its victims to attackers.
The attack involves deceiving gaming website visitors into downloading a malware loader camouflaged as a legitimate installer for popular-but-deprecated apps such as Adobe Flash Player or Microsoft Silverlight, only for the loader to act as a conduit for fetching next-stage payloads.
Specifically, the websites' online support chat pages are booby-trapped with malicious JavaScript code, which is used to deliver the malware to the victims.
Besides featuring an array of capabilities that run the typical spyware gamut, BIOPASS is equipped to establish live streaming to a cloud service under the attacker's control via Real-Time Messaging Protocol, in addition to communicating with the command-and-control server using the Socket.
It isn't clear exactly as to who is behind this malware strain, but Trend Micro researchers said they found overlaps between BIOPASS and that of TTPs often associated with the Winnti Group, a sophisticated Chinese hacking group specialized in cyber espionage attacks, based on the use of stolen certificates and a Cobalt Strike binary that was previously attributed to the threat actor.
"BIOPASS RAT is a sophisticated type of malware that is implemented as Python scripts," the researchers said.
News URL
http://feedproxy.google.com/~r/TheHackersNews/~3/lUhuWFPTb1Y/hackers-spread-biopass-malware-via.html
Related news
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- Chinese hackers target Russian govt with upgraded RAT malware (source)
- US charges Chinese hackers linked to critical infrastructure breaches (source)
- Chinese Hackers Breach Juniper Networks Routers With Custom Backdoors and Rootkits (source)
- Chinese Weaver Ant hackers spied on telco network for 4 years (source)
- Hackers Use .NET MAUI to Target Indian and Chinese Users with Fake Banking, Social Apps (source)
- Chinese Hackers Breach Asian Telecom, Remain Undetected for Over 4 Years (source)
- North Korean Hackers Deploy BeaverTail Malware via 11 Malicious npm Packages (source)
- State-Sponsored Hackers Weaponize ClickFix Tactic in Targeted Malware Campaigns (source)