Vulnerabilities > CVE-2017-2416 - Improper Restriction of Operations within the Bounds of a Memory Buffer vulnerability in Apple products
Attack vector
NETWORK Attack complexity
MEDIUM Privileges required
NONE Confidentiality impact
PARTIAL Integrity impact
PARTIAL Availability impact
PARTIAL Summary
An issue was discovered in certain Apple products. iOS before 10.3 is affected. macOS before 10.12.4 is affected. tvOS before 10.2 is affected. watchOS before 3.2 is affected. The issue involves the "ImageIO" component. It allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption and application crash) via a crafted image file.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Buffer Overflow via Environment Variables This attack pattern involves causing a buffer overflow through manipulation of environment variables. Once the attacker finds that they can modify an environment variable, they may try to overflow associated buffers. This attack leverages implicit trust often placed in environment variables.
- Overflow Buffers Buffer Overflow attacks target improper or missing bounds checking on buffer operations, typically triggered by input injected by an attacker. As a consequence, an attacker is able to write past the boundaries of allocated buffer regions in memory, causing a program crash or potentially redirection of execution as per the attackers' choice.
- Client-side Injection-induced Buffer Overflow This type of attack exploits a buffer overflow vulnerability in targeted client software through injection of malicious content from a custom-built hostile service.
- Filter Failure through Buffer Overflow In this attack, the idea is to cause an active filter to fail by causing an oversized transaction. An attacker may try to feed overly long input strings to the program in an attempt to overwhelm the filter (by causing a buffer overflow) and hoping that the filter does not fail securely (i.e. the user input is let into the system unfiltered).
- MIME Conversion An attacker exploits a weakness in the MIME conversion routine to cause a buffer overflow and gain control over the mail server machine. The MIME system is designed to allow various different information formats to be interpreted and sent via e-mail. Attack points exist when data are converted to MIME compatible format and back.
Nessus
NASL family MacOS X Local Security Checks NASL id MACOS_10_12_4.NASL description The remote host is running a version of macOS that is 10.12.x prior to 10.12.4. It is, therefore, affected by multiple vulnerabilities in multiple components, some of which are remote code execution vulnerabilities. An unauthenticated, remote attacker can exploit these remote code execution vulnerabilities by convincing a user to visit a specially crafted website, resulting in the execution of arbitrary code in the context of the current user. The affected components are as follows : - apache - apache_mod_php - AppleGraphicsPowerManagement - AppleRAID - Audio - Bluetooth - Carbon - CoreGraphics - CoreMedia - CoreText - curl - EFI - FinderKit - FontParser - HTTPProtocol - Hypervisor - iBooks - ImageIO - Intel Graphics Driver - IOATAFamily - IOFireWireAVC - IOFireWireFamily - Kernel - Keyboards - libarchive - libc++abi - LibreSSL - MCX Client - Menus - Multi-Touch - OpenSSH - OpenSSL - Printing - python - QuickTime - Security - SecurityFoundation - sudo - System Integrity Protection - tcpdump - tiffutil - WebKit last seen 2020-06-01 modified 2020-06-02 plugin id 99134 published 2017-03-31 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/99134 title macOS 10.12.x < 10.12.4 Multiple Vulnerabilities (httpoxy) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(99134); script_version("1.9"); script_cvs_date("Date: 2019/11/13"); script_cve_id( "CVE-2016-0736", "CVE-2016-2161", "CVE-2016-3619", "CVE-2016-4688", "CVE-2016-5387", "CVE-2016-5636", "CVE-2016-7056", "CVE-2016-7585", "CVE-2016-7922", "CVE-2016-7923", "CVE-2016-7924", "CVE-2016-7925", "CVE-2016-7926", "CVE-2016-7927", "CVE-2016-7928", "CVE-2016-7929", "CVE-2016-7930", "CVE-2016-7931", "CVE-2016-7932", "CVE-2016-7933", "CVE-2016-7934", "CVE-2016-7935", "CVE-2016-7936", "CVE-2016-7937", "CVE-2016-7938", "CVE-2016-7939", "CVE-2016-7940", "CVE-2016-7973", "CVE-2016-7974", "CVE-2016-7975", "CVE-2016-7983", "CVE-2016-7984", "CVE-2016-7985", "CVE-2016-7986", "CVE-2016-7992", "CVE-2016-7993", "CVE-2016-8574", "CVE-2016-8575", "CVE-2016-8740", "CVE-2016-8743", "CVE-2016-9533", "CVE-2016-9535", "CVE-2016-9536", "CVE-2016-9537", "CVE-2016-9538", "CVE-2016-9539", "CVE-2016-9540", "CVE-2016-9586", "CVE-2016-9935", "CVE-2016-10009", "CVE-2016-10010", "CVE-2016-10011", "CVE-2016-10012", "CVE-2016-10158", "CVE-2016-10159", "CVE-2016-10160", "CVE-2016-10161", "CVE-2017-2379", "CVE-2017-2381", "CVE-2017-2388", "CVE-2017-2390", "CVE-2017-2398", "CVE-2017-2401", "CVE-2017-2402", "CVE-2017-2403", "CVE-2017-2406", "CVE-2017-2407", "CVE-2017-2408", "CVE-2017-2409", "CVE-2017-2410", "CVE-2017-2413", "CVE-2017-2416", "CVE-2017-2417", "CVE-2017-2418", "CVE-2017-2420", "CVE-2017-2421", "CVE-2017-2422", "CVE-2017-2423", "CVE-2017-2425", "CVE-2017-2426", "CVE-2017-2427", "CVE-2017-2428", "CVE-2017-2429", "CVE-2017-2430", "CVE-2017-2431", "CVE-2017-2432", "CVE-2017-2435", "CVE-2017-2436", "CVE-2017-2437", "CVE-2017-2438", "CVE-2017-2439", "CVE-2017-2440", "CVE-2017-2441", "CVE-2017-2443", "CVE-2017-2448", "CVE-2017-2449", "CVE-2017-2450", "CVE-2017-2451", "CVE-2017-2456", "CVE-2017-2458", "CVE-2017-2461", "CVE-2017-2462", "CVE-2017-2467", "CVE-2017-2472", "CVE-2017-2473", "CVE-2017-2474", "CVE-2017-2477", "CVE-2017-2478", "CVE-2017-2482", "CVE-2017-2483", "CVE-2017-2485", "CVE-2017-2487", "CVE-2017-2489", "CVE-2017-2490", "CVE-2017-5029", "CVE-2017-5202", "CVE-2017-5203", "CVE-2017-5204", "CVE-2017-5205", "CVE-2017-5341", "CVE-2017-5342", "CVE-2017-5482", "CVE-2017-5483", "CVE-2017-5484", "CVE-2017-5485", "CVE-2017-5486", "CVE-2017-6974", "CVE-2017-7070" ); script_bugtraq_id( 85919, 91247, 91816, 94572, 94650, 94742, 94744, 94745, 94746, 94747, 94753, 94754, 94846, 94968, 94972, 94975, 94977, 95019, 95076, 95077, 95078, 95375, 95764, 95768, 95774, 95783, 95852, 96767, 97132, 97134, 97137, 97140, 97146, 97147, 97300, 97301, 97303 ); script_xref(name:"APPLE-SA", value:"APPLE-SA-2017-03-27-3"); script_xref(name:"CERT", value:"797896"); script_xref(name:"EDB-ID", value:"40961"); script_xref(name:"EDB-ID", value:"40962"); script_name(english:"macOS 10.12.x < 10.12.4 Multiple Vulnerabilities (httpoxy)"); script_summary(english:"Checks the version of macOS."); script_set_attribute(attribute:"synopsis", value: "The remote host is missing a macOS update that fixes multiple security vulnerabilities."); script_set_attribute(attribute:"description", value: "The remote host is running a version of macOS that is 10.12.x prior to 10.12.4. It is, therefore, affected by multiple vulnerabilities in multiple components, some of which are remote code execution vulnerabilities. An unauthenticated, remote attacker can exploit these remote code execution vulnerabilities by convincing a user to visit a specially crafted website, resulting in the execution of arbitrary code in the context of the current user. The affected components are as follows : - apache - apache_mod_php - AppleGraphicsPowerManagement - AppleRAID - Audio - Bluetooth - Carbon - CoreGraphics - CoreMedia - CoreText - curl - EFI - FinderKit - FontParser - HTTPProtocol - Hypervisor - iBooks - ImageIO - Intel Graphics Driver - IOATAFamily - IOFireWireAVC - IOFireWireFamily - Kernel - Keyboards - libarchive - libc++abi - LibreSSL - MCX Client - Menus - Multi-Touch - OpenSSH - OpenSSL - Printing - python - QuickTime - Security - SecurityFoundation - sudo - System Integrity Protection - tcpdump - tiffutil - WebKit"); script_set_attribute(attribute:"see_also", value:"https://support.apple.com/en-us/HT207615"); # https://lists.apple.com/archives/security-announce/2017/Mar/msg00004.html script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?ddb4db4a"); script_set_attribute(attribute:"see_also", value:"https://httpoxy.org"); script_set_attribute(attribute:"solution", value: "Upgrade to macOS version 10.12.4 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2016-5636"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"in_the_news", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/01/21"); script_set_attribute(attribute:"patch_publication_date", value:"2017/03/27"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/03/31"); script_set_attribute(attribute:"plugin_type", value:"combined"); script_set_attribute(attribute:"cpe", value:"cpe:/o:apple:macos"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"MacOS X Local Security Checks"); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("ssh_get_info.nasl", "os_fingerprint.nasl"); script_require_ports("Host/MacOSX/Version", "Host/OS"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("misc_func.inc"); os = get_kb_item("Host/MacOSX/Version"); if (!os) { os = get_kb_item_or_exit("Host/OS"); if ("Mac OS X" >!< os) audit(AUDIT_OS_NOT, "macOS / Mac OS X"); c = get_kb_item("Host/OS/Confidence"); if (c <= 70) exit(1, "Can't determine the host's OS with sufficient confidence."); } if (!os) audit(AUDIT_OS_NOT, "macOS / Mac OS X"); matches = eregmatch(pattern:"Mac OS X ([0-9]+(\.[0-9]+)+)", string:os); if (isnull(matches)) exit(1, "Failed to parse the macOS / Mac OS X version ('" + os + "')."); version = matches[1]; if (version !~ "^10\.12($|[^0-9])") audit(AUDIT_OS_NOT, "Mac OS 10.12.x"); fixed_version = "10.12.4"; if (ver_compare(ver:version, fix:fixed_version, strict:FALSE) == -1) { security_report_v4( port:0, severity:SECURITY_HOLE, xss:TRUE, extra: '\n Installed version : ' + version + '\n Fixed version : ' + fixed_version + '\n' ); } else audit(AUDIT_INST_VER_NOT_VULN, "macOS / Mac OS X", version);NASL family Misc. NASL id APPLETV_10_2.NASL description According to its banner, the version of Apple TV on the remote device is prior to 10.2. It is, therefore, affected by multiple vulnerabilities : - An out-of-bounds read error exists in LibTIFF in the DumpModeEncode() function within file tif_dumpmode.c. An unauthenticated, remote attacker can exploit this to crash a process linked against the library or disclose memory contents. (CVE-2016-3619) - An out-of-bounds read error exists in WebKit when handling certain JavaScript code. An unauthenticated, remote attacker can exploit this to cause a denial of service condition or the disclosure of memory contents. (CVE-2016-9642) - A denial of service vulnerability exists in WebKit when handling certain regular expressions. An unauthenticated, remote attacker can exploit this, via a specially crafted web page, to exhaust available memory resources. (CVE-2016-9643) - An information disclosure vulnerability exists in WebKit when handling page loading due to improper validation of certain input. An unauthenticated, remote attacker can exploit this to disclose data cross-origin. (CVE-2017-2367) - A buffer overflow condition exists in the Carbon component when handling specially crafted DFONT files due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2379) - An information disclosure vulnerability exists in WebKit when handling unspecified exceptions. An unauthenticated, remote attacker can exploit this, via specially crafted web content, to disclose data cross-origin. (CVE-2017-2386) - A flaw exists in the libarchive component due to the insecure creation of temporary files. A local attacker can exploit this, by using a symlink attack against an unspecified file, to cause unexpected changes to be made to file system permissions. (CVE-2017-2390) - Multiple memory corruption issues exist in WebKit that allow an unauthenticated, remote attacker to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2394, CVE-2017-2395, CVE-2017-2396, CVE-2017-2454, CVE-2017-2455, CVE-2017-2459, CVE-2017-2460, CVE-2017-2464, CVE-2017-2465, CVE-2017-2466, CVE-2017-2468, CVE-2017-2469, CVE-2017-2470, CVE-2017-2476) - A memory corruption issue exists in the Kernel component due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, by convincing a user to run a specially crafted application, to cause a denial of service condition or the execution or arbitrary code. (CVE-2017-2401) - Multiple memory corruption issues exist in the FontParser component when handling font files due to improper validation of certain input. An unauthenticated, remote attacker can exploit these to cause a denial condition or the execution of arbitrary code. (CVE-2017-2406, CVE-2017-2407, CVE-2017-2487) - An unspecified type confusion error exists in WebKit that allows an unauthenticated, remote attacker to execute arbitrary code by using specially crafted web content. (CVE-2017-2415) - A memory corruption issue exists in the ImageIO component, specifically in the GIFReadPlugin::init() function, when handling image files due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via a specially crafted image file, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2416) - An infinite recursion condition exists in the CoreGraphics component when handling image files. An unauthenticated, remote can exploit this, via a specially crafted image file, to cause a denial of service condition. (CVE-2017-2417) - An unspecified flaw exists related to nghttp2 and LibreSSL. An unauthenticated, remote attacker can exploit this, by convincing a user to access a malicious HTTP/2 server, to have an unspecified impact on confidentiality, integrity, and availability. (CVE-2017-2428) - A type confusion error exists in the Audio component when parsing specially crafted M4A audio files due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2430) - An integer overflow condition exists in the ImageIO component when handling JPEG files due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2432) - A memory corruption issue exists in the CoreText component when handling font files due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2435) - An out-of-bounds read error exists in the FontParser component when handling font files. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to disclose process memory. (CVE-2017-2439) - An integer overflow condition exists in the Kernel component due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, by convincing a user to run a specially crafted application, to execute arbitrary code with kernel-level privileges. (CVE-2017-2440) - A use-after-free error exists in libc++abi when demangling C++ applications. An unauthenticated, remote attacker can exploit this, by convincing a user to run a specially crafted application, to execute arbitrary code. (CVE-2017-2441) - A memory corruption issue exists in WebKit within the CoreGraphics component due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via specially crafted web content, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2444) - A universal cross-site scripting (XSS) vulnerability exists in WebKit when handling frame objects due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via specially crafted web content, to execute arbitrary script code in a user last seen 2020-06-01 modified 2020-06-02 plugin id 99264 published 2017-04-10 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/99264 title Apple TV < 10.2 Multiple Vulnerabilities code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(99264); script_version("1.9"); script_cvs_date("Date: 2019/11/13"); script_cve_id( "CVE-2016-3619", "CVE-2016-9642", "CVE-2016-9643", "CVE-2017-2367", "CVE-2017-2379", "CVE-2017-2386", "CVE-2017-2390", "CVE-2017-2394", "CVE-2017-2395", "CVE-2017-2396", "CVE-2017-2401", "CVE-2017-2406", "CVE-2017-2407", "CVE-2017-2415", "CVE-2017-2416", "CVE-2017-2417", "CVE-2017-2428", "CVE-2017-2430", "CVE-2017-2432", "CVE-2017-2435", "CVE-2017-2439", "CVE-2017-2440", "CVE-2017-2441", "CVE-2017-2444", "CVE-2017-2445", "CVE-2017-2446", "CVE-2017-2447", "CVE-2017-2448", "CVE-2017-2450", "CVE-2017-2451", "CVE-2017-2454", "CVE-2017-2455", "CVE-2017-2456", "CVE-2017-2458", "CVE-2017-2459", "CVE-2017-2460", "CVE-2017-2461", "CVE-2017-2462", "CVE-2017-2464", "CVE-2017-2465", "CVE-2017-2466", "CVE-2017-2467", "CVE-2017-2468", "CVE-2017-2469", "CVE-2017-2470", "CVE-2017-2472", "CVE-2017-2473", "CVE-2017-2474", "CVE-2017-2475", "CVE-2017-2476", "CVE-2017-2478", "CVE-2017-2481", "CVE-2017-2482", "CVE-2017-2483", "CVE-2017-2485", "CVE-2017-2487", "CVE-2017-2490", "CVE-2017-2491", "CVE-2017-2492" ); script_bugtraq_id( 85919, 94554, 94559, 97130, 97131, 97132, 97134, 97137, 97143, 97146, 97301, 98316 ); script_xref(name:"APPLE-SA", value:"APPLE-SA-2017-03-27-6"); script_name(english:"Apple TV < 10.2 Multiple Vulnerabilities"); script_summary(english:"Checks the build number."); script_set_attribute(attribute:"synopsis", value: "The remote Apple TV device is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "According to its banner, the version of Apple TV on the remote device is prior to 10.2. It is, therefore, affected by multiple vulnerabilities : - An out-of-bounds read error exists in LibTIFF in the DumpModeEncode() function within file tif_dumpmode.c. An unauthenticated, remote attacker can exploit this to crash a process linked against the library or disclose memory contents. (CVE-2016-3619) - An out-of-bounds read error exists in WebKit when handling certain JavaScript code. An unauthenticated, remote attacker can exploit this to cause a denial of service condition or the disclosure of memory contents. (CVE-2016-9642) - A denial of service vulnerability exists in WebKit when handling certain regular expressions. An unauthenticated, remote attacker can exploit this, via a specially crafted web page, to exhaust available memory resources. (CVE-2016-9643) - An information disclosure vulnerability exists in WebKit when handling page loading due to improper validation of certain input. An unauthenticated, remote attacker can exploit this to disclose data cross-origin. (CVE-2017-2367) - A buffer overflow condition exists in the Carbon component when handling specially crafted DFONT files due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2379) - An information disclosure vulnerability exists in WebKit when handling unspecified exceptions. An unauthenticated, remote attacker can exploit this, via specially crafted web content, to disclose data cross-origin. (CVE-2017-2386) - A flaw exists in the libarchive component due to the insecure creation of temporary files. A local attacker can exploit this, by using a symlink attack against an unspecified file, to cause unexpected changes to be made to file system permissions. (CVE-2017-2390) - Multiple memory corruption issues exist in WebKit that allow an unauthenticated, remote attacker to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2394, CVE-2017-2395, CVE-2017-2396, CVE-2017-2454, CVE-2017-2455, CVE-2017-2459, CVE-2017-2460, CVE-2017-2464, CVE-2017-2465, CVE-2017-2466, CVE-2017-2468, CVE-2017-2469, CVE-2017-2470, CVE-2017-2476) - A memory corruption issue exists in the Kernel component due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, by convincing a user to run a specially crafted application, to cause a denial of service condition or the execution or arbitrary code. (CVE-2017-2401) - Multiple memory corruption issues exist in the FontParser component when handling font files due to improper validation of certain input. An unauthenticated, remote attacker can exploit these to cause a denial condition or the execution of arbitrary code. (CVE-2017-2406, CVE-2017-2407, CVE-2017-2487) - An unspecified type confusion error exists in WebKit that allows an unauthenticated, remote attacker to execute arbitrary code by using specially crafted web content. (CVE-2017-2415) - A memory corruption issue exists in the ImageIO component, specifically in the GIFReadPlugin::init() function, when handling image files due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via a specially crafted image file, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2416) - An infinite recursion condition exists in the CoreGraphics component when handling image files. An unauthenticated, remote can exploit this, via a specially crafted image file, to cause a denial of service condition. (CVE-2017-2417) - An unspecified flaw exists related to nghttp2 and LibreSSL. An unauthenticated, remote attacker can exploit this, by convincing a user to access a malicious HTTP/2 server, to have an unspecified impact on confidentiality, integrity, and availability. (CVE-2017-2428) - A type confusion error exists in the Audio component when parsing specially crafted M4A audio files due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2430) - An integer overflow condition exists in the ImageIO component when handling JPEG files due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2432) - A memory corruption issue exists in the CoreText component when handling font files due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2435) - An out-of-bounds read error exists in the FontParser component when handling font files. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to disclose process memory. (CVE-2017-2439) - An integer overflow condition exists in the Kernel component due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, by convincing a user to run a specially crafted application, to execute arbitrary code with kernel-level privileges. (CVE-2017-2440) - A use-after-free error exists in libc++abi when demangling C++ applications. An unauthenticated, remote attacker can exploit this, by convincing a user to run a specially crafted application, to execute arbitrary code. (CVE-2017-2441) - A memory corruption issue exists in WebKit within the CoreGraphics component due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via specially crafted web content, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2444) - A universal cross-site scripting (XSS) vulnerability exists in WebKit when handling frame objects due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via specially crafted web content, to execute arbitrary script code in a user's browser session. (CVE-2017-2445) - A flaw exists in WebKit due to non-strict mode functions that are called from built-in strict mode scripts not being properly restricted from calling sensitive native functions. An unauthenticated, remote attacker can exploit this, via specially crafted web content, to execute arbitrary code. (CVE-2017-2446) - An out-of-bounds read error exists in WebKit when handling the bound arguments array of a bound function. An unauthenticated, remote attacker can exploit this, via specially crafted web content, to disclose memory contents. (CVE-2017-2447) - An unspecified flaw exists in the Security component due to improper validation of OTR packets under certain conditions. A man-in-the-middle attacker can exploit this to disclose and optionally manipulate transmitted data by spoofing the TLS/SSL server via a packet that appears to be valid. (CVE-2017-2448) - An out-of-bounds read error exists in CoreText component when handling font files. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to disclose process memory. (CVE-2017-2450) - A buffer overflow condition exists in the Security component due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, by convincing a user to run a specially crafted application, to execute arbitrary code with root root privileges. (CVE-2017-2451) - A race condition exists in the Kernel component when handling memory using the 'mach_msg' system call. An unauthenticated, remote attacker can exploit this, by convincing a user to run a specially crafted application, to cause a heap-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code with root privileges. CVE-2017-2456) - An buffer overflow condition exists in the Keyboards component due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, by convincing a user to run a specially crafted application, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2458) - A denial of service vulnerability exists in the CoreText component when handling specially crafted text messages due to improper validation of certain input. An unauthenticated, remote attacker can exploit this to exhaust available resources on the system. (CVE-2017-2461) - A heap buffer overflow condition exists in the Audio component when parsing specially crafted M4A audio files due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to execute arbitrary code. (CVE-2017-2462) - An memory corruption issue exists in the ImageIO component when handling specially crafted files due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via a specially crafted file, to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2467) - A use-after-free error exists in the Kernel component in the XNU port actions extension due to improper handling of port references in error cases. An local attacker can exploit this to deference already freed memory, resulting in the execution of arbitrary code with kernel-level privileges. (CVE-2017-2472) - A signedness error exists in the Kernel component in the SIOCSIFORDER IOCTL due to improper validation of certain input. A local attacker can exploit this to cause an out-of-bounds read and memory corruption, resulting in a denial of service condition or the execution of arbitrary code with kernel-level privileges. (CVE-2017-2473) - A off-by-one overflow condition exists in the Kernel component in the SIOCSIFORDER IOCTL due to improper validation of certain input. A local attacker can exploit this to cause a heap-based buffer overflow, resulting in the execution of arbitrary code with kernel-level privileges. (CVE-2017-2474) - A universal cross-site scripting (XSS) vulnerability exists in WebKit when handling frames due to improper validation of certain input. An unauthenticated, remote attacker can exploit this, via specially crafted web content, to execute arbitrary script code in a user's browser session. (CVE-2017-2475) - A race condition exists in the Kernel component in the necp_open() function when closing files descriptors due to improper handling of proc_fd locks. A local attacker can exploit this to dereference already freed memory, resulting in the execution of arbitrary code with kernel-level privileges. (CVE-2017-2478) - A use-after-free error exists in WebKit when handling ElementData objects. An unauthenticated, remote attacker can exploit this, via specially crafted web content, to dereference already freed memory, resulting in the execution of arbitrary code. (CVE-2017-2481) - A heap buffer overflow condition exists in the Kernel component within the Berkeley Packet Filter (BPF) BIOCSBLEN IOCTL due to improper validation of certain input when reattaching to an interface. A local attacker can exploit this to cause a denial of service condition or the execution of arbitrary code with kernel-level privileges. (CVE-2017-2482) - An off-by-one error exists in the Kernel component, specifically in the audit_pipe_open() function, when handling auditpipe devices due to improper validation of certain input. A local attacker can exploit this to corrupt memory, resulting in a denial of service condition or the execution of arbitrary code with kernel-level privileges. (CVE-2017-2483) - An unspecified memory corruption issue exists in the Security component when parsing X.509 certificates due to improper validation of certain input. An unauthenticated, remote attacker can exploit this to cause a denial of service condition or the execution of arbitrary code. (CVE-2017-2485) - A double-free error exists in the Kernel component due to FSEVENTS_DEVICE_FILTER_64 IOCTL not properly locking devices. A local attacker can exploit this to corrupt memory, resulting in the execution of arbitrary code with elevated privileges. (CVE-2017-2490) - A use-after-free error exists in JavaScriptCore when handling the String.replace() method. An unauthenticated, remote attacker can exploit this to deference already freed memory, resulting in the execution of arbitrary code. (CVE-2017-2491) - A universal cross-site scripting (XSS) vulnerability exists in JavaScriptCore due to an unspecified prototype flaw. An unauthenticated, remote attacker can exploit this, via a specially crafted web page, to execute arbitrary code in a user's browser session. (CVE-2017-2492) Note that only 4th generation models are affected by these vulnerabilities."); script_set_attribute(attribute:"see_also", value:"https://support.apple.com/en-us/HT207601"); # https://lists.apple.com/archives/security-announce/2017/Mar/msg00007.html script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?b1dbb626"); script_set_attribute(attribute:"solution", value: "Upgrade to Apple TV version 10.2 or later. Note that this update is only available for 4th generation models."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2017-2490"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/04/07"); script_set_attribute(attribute:"patch_publication_date", value:"2017/03/27"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/04/10"); script_set_attribute(attribute:"plugin_type", value:"remote"); script_set_attribute(attribute:"cpe", value:"cpe:/a:apple:apple_tv"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Misc."); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("appletv_version.nasl"); script_require_keys("AppleTV/Version", "AppleTV/Model", "AppleTV/URL", "AppleTV/Port"); script_require_ports("Services/www", 7000); exit(0); } include("audit.inc"); include("appletv_func.inc"); url = get_kb_item('AppleTV/URL'); if (empty_or_null(url)) exit(0, 'Cannot determine Apple TV URL.'); port = get_kb_item('AppleTV/Port'); if (empty_or_null(port)) exit(0, 'Cannot determine Apple TV port.'); build = get_kb_item('AppleTV/Version'); if (empty_or_null(build)) audit(AUDIT_UNKNOWN_DEVICE_VER, 'Apple TV'); model = get_kb_item('AppleTV/Model'); if (empty_or_null(model)) exit(0, 'Cannot determine Apple TV model.'); fixed_build = "14W265"; tvos_ver = '10.2'; # determine gen from the model gen = APPLETV_MODEL_GEN[model]; appletv_check_version( build : build, fix : fixed_build, affected_gen : 4, fix_tvos_ver : tvos_ver, model : model, gen : gen, port : port, url : url, severity : SECURITY_HOLE, xss : TRUE );
Seebug
| bulletinFamily | exploit |
| description | > ImageIO Available for: iPhone 5 and later, iPad 4th generation and later, iPod touch 6th generation and later > > Impact: Processing a maliciously crafted image may lead to arbitrary code execution > > Description: A memory corruption issue was addressed through improved input validation. > > CVE-2017-2416: flanker_hqd of KeenLab, Tencent ### Abstract Recently I’ve switched my main research focus back from Apple stuff to Android and browsers. While I was auditing a custom image parsing library written by some ppls, I transferred the test case image manipulated by 010editor via a popular IM messenger, and all of a sudden, the app crashed. I investigated the crash and found it is a issue in ImageIO library, and can be automatically triggered in all kinds of iOS/macOS apps that receives GIF images, especially the ones for instant messaging, such as `Signal, Telegram, Slack, iMessage` etc and Email clients such as `Mail, Outlook, Inbox, Gmail`, etc and even financial apps that want to be an IM such as `Alipay`. All these apps will crash on receiving the malicious GIF. I haven’t test Twitter, but should you find a way to post the malformed GIF online (which I think can be done by manipulated the post stream to bypass the frontend filtering, but I was too busy to try that), the client should also crash as well. What make things worse is that many clients will automatically reload and reparse the image on open, triggering the vulnerability again and again, lead to infinite loop and eliminating the need for attacker to persistent – -b ### DEMO video1 The first video demonstrates receiving malformed gif file via iMessage lead to crash https://blog.flanker017.me/wp-content/uploads/2017/04/crash1.mp4 ### DEMO video2 the second video demonstrates persistence (user cannot open iMessage anymore…) https://blog.flanker017.me/wp-content/uploads/2017/04/crash123.m4v ### Crash trace ``` * thread #1: tid = 0x17570, 0x00007fff9557f1ab ImageIO`IIOReadPlugin::IIOReadPlugin(CGImagePlus*, unsigned int, unsigned int, long long, unsigned char) + 67, queue = 'com.apple.main-thread', stop reason = EXC_BAD_ACCESS (code=EXC_I386_GPFLT) frame #0: 0x00007fff9557f1ab ImageIO`IIOReadPlugin::IIOReadPlugin(CGImagePlus*, unsigned int, unsigned int, long long, unsigned char) + 67 ImageIO`IIOReadPlugin::IIOReadPlugin: -> 0x7fff9557f1ab <+67>: mov al, byte ptr [rdi + 0x40] 0x7fff9557f1ae <+70>: mov qword ptr [rbx + 0x20], rdi 0x7fff9557f1b2 <+74>: mov byte ptr [rbx + 0xc8], al 0x7fff9557f1b8 <+80>: xor eax, eax Thread 0 Crashed:: Dispatch queue: com.apple.main-thread 0 com.apple.ImageIO.framework 0x00007fffa144d1ab IIOReadPlugin::IIOReadPlugin(CGImagePlus*, unsigned int, unsigned int, long long, unsigned char) + 67 1 com.apple.ImageIO.framework 0x00007fffa14b8c93 GIFReadPlugin::InitProc(CGImagePlugin*, unsigned long, unsigned long) + 59 2 com.apple.ImageIO.framework 0x00007fffa14177da IIOImageSource::makeImagePlus(unsigned long, __CFDictionary const*) + 252 3 com.apple.ImageIO.framework 0x00007fffa141918b IIOImageSource::getPropertiesAtIndexInternal(unsigned long, __CFDictionary const*) + 57 4 com.apple.ImageIO.framework 0x00007fffa141911c IIOImageSource::copyPropertiesAtIndex(unsigned long, __CFDictionary const*) + 98 5 com.apple.ImageIO.framework 0x00007fffa13f03ca CGImageSourceCopyPropertiesAtIndex + 181 6 com.apple.AppKit 0x00007fff9cfdbcae +[NSBitmapImageRep _imagesWithData:hfsFileType:extension:zone:expandImageContentNow:includeAllReps:] + 543 7 com.apple.AppKit 0x00007fff9cfdba68 +[NSBitmapImageRep _imageRepsWithData:hfsFileType:extension:expandImageContentNow:] + 93 8 com.apple.AppKit 0x00007fff9d4bf08e -[NSImage _initWithData:fileType:hfsType:] + 479 ``` Almost all image related functions on Apple platform calls down to `[NSImage _initWithData:fileType:hfsType:]`, and `IIOImageSource` dispatches image parsing to corresponding plugin based on signature detection (note: not based on file extension). This feature will be useful afterwards. ### Sample file to test if you’re vulnerable Test image sample: [Sample PNG](https://blog.flanker017.me/wp-content/uploads/2017/04/Stykz_Sample2.png) [Sample GIF](https://blog.flanker017.me/wp-content/uploads/2017/04/Stykz_Sample2.gif) Grab an image file and change the width/height field to both negative short whose unsigned form value larger than 0xff00\. 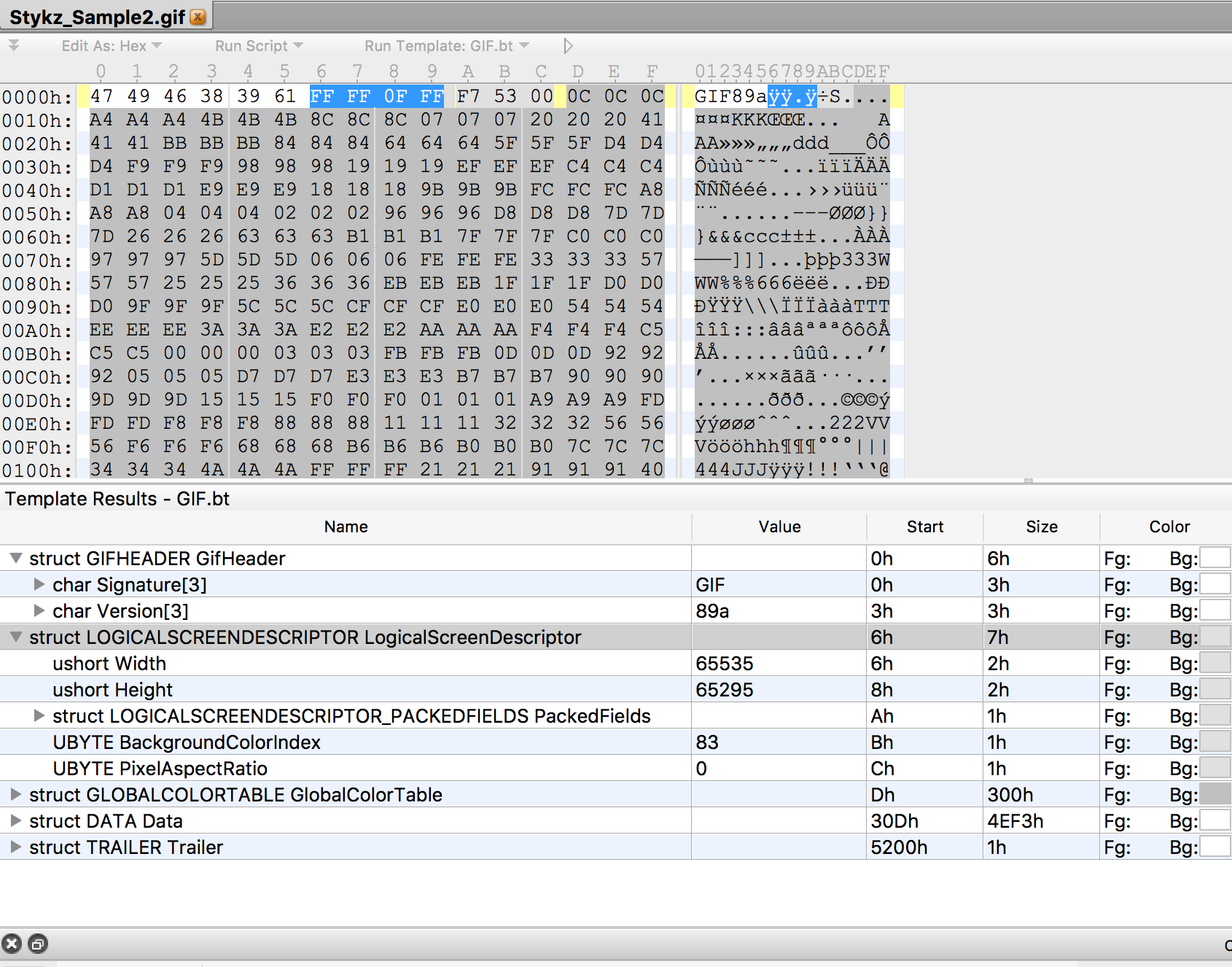 Drag it into /send to any macos/iOS application and if it crashes, you’re vulnerable. ### Analysis The root cause seems to be at GIFReadPlugin::init function, in the following decompiled snippet: ``` v32 = (signed __int16)width * (signed __int64)height; if ( v32 > filesize * 1100 * v29 ) { LOBYTE(aspectbyte) = 0; v15 = 0LL; if ( this->gapC0[8] ) { LOBYTE(aspectbyte) = 0; LogError( "init", 498, "malformed GIF file (%d x %d) - [canvasSize: %ld fileSize: %ld ratio: %d] \n", (unsigned int)(signed __int16)width, (unsigned int)(height), // width >> 16 is height (signed __int16)width * (signed __int64)SHIWORD(width), filesize, v32 / filesize); v15 = 0LL; } goto LABEL_71; } __text:00000000000CC51F movsx rax, r9w __text:00000000000CC523 mov ecx, r9d __text:00000000000CC526 shr ecx, 10h __text:00000000000CC529 movsx rbx, cx __text:00000000000CC52D imul rbx, rax __text:00000000000CC531 imul rdx, r12, 44Ch __text:00000000000CC538 mov rax, rdx __text:00000000000CC53B imul rax, rsi __text:00000000000CC53F cmp rbx, rax ``` An attacker can craft an image of negative height and weight, thus bypassing the check comparing to file size, lead to following out-of-bound. As I have mentioned above, the dispatching is based on file signature rather than file extension. I noticed some applications’ web interfaces have check on the size of GIF images, preventing me from spreading this POC to mobile apps. However they do not have check on PNG extension, allowing me to upload the malformed GIF image in PNG extension, bypassing the check and crashes whoever receives it. While this does make sense, after Apple releases the fix I checked the new ImageIO binary and found the fix actually goes another way. Recall the crash happens in IIOReadPlugin::IIOReadPlugin, in the following pseudo code at 10.11.2/3: ``` bool __fastcall IIOReadPlugin::IIOReadPlugin(IIOReadPlugin *a1, __int64 a2, int a3, int a4, __int64 a5, unsigned __int8 a6) { unsigned __int8 v6; // r14@1 IIOReadPlugin *this; // rbx@1 __int64 v8; // rax@1 __int64 sessionwrap; // rdi@1 IIOImageReadSession *session; // rax@2 IIOImageRead *v11; // rdi@2 __int64 v12; // rax@2 __int64 *v13; // rcx@5 __int64 v14; // rdx@5 bool result; // al@5 v6 = a6; this = a1; a1->vt = (__int64)off_1659D0; a1->field_8 = a2; v8 = *(_QWORD *)(a2 + 24); a1->field_10 = v8; a1->field_38 = a3; a1->field_3c = a4; a1->field_30 = a5; sessionwrap = *(_QWORD *)(v8 + 24); if ( sessionwrap ) { session = (IIOImageReadSession *)CGImageReadSessionGetSession(sessionwrap); //session is invalid this->session = session; v11 = (IIOImageRead *)session->imageread; //oob happens here and lead to crash LOBYTE(session) = v11->field_40; this->field_20 = (__int64)v11; this->field_c8 = (char)session; v12 = 0LL; if ( v11 ) v12 = IIOImageRead::getSize(v11); } else { this->field_20 = 0LL; this->session = 0LL; this->field_c8 = 1; v12 = 0LL; } And now apple changes the if-block in 10.12.4: a1->field_8 = cgimgplus; imageplus = CGImagePlusGetIPlus(cgimgplus); a1->field_10 = imageplus; a1->field_38 = v9; a1->field_3c = v8; a1->field_30 = v7; v12 = *(_QWORD *)(imageplus + 32); a1->field_18 = v12; imageread = *(IIOImageRead **)(v12 + 32); if ( imageread ) { v10->field_c8 = *((_BYTE *)imageread + 64); v10->field_20 = (__int64)imageread; v14 = IIOImageRead::getSize(imageread); } else { v10->field_c8 = 0; v10->field_20 = 0LL; v14 = 0LL; } ``` Removing the usage of IIOImageReadSession in this function. Is it better than fixing the size change? Dunno. ### Custom fix? For app developers who want to mitigate this issue for users staying at old versions, I suggest check for negative width and height before passing to NSImage. I believe this vulnerability is introduced in iOS 10, so iOS 9/OSX 10.11 users are not affected (how many ppls are still using iOS9? Raise your hands). For iOS 10/macOS 10.12 users, please upgrade to 10.3/10.12.4 for the official fix. ### Timeline * 2017.1.10 Initial discovery * 2017.1.16 Report to Apple * 2017.1.24 Apple responds on they are working on a fix * 2017.3.23 CVE-2017-2416 assigned * 2017.3.28 Advisory published at https://support.apple.com/en-us/HT207617 * 2017.4.6 Public disclosure |
| id | SSV:92924 |
| last seen | 2017-11-19 |
| modified | 2017-04-07 |
| published | 2017-04-07 |
| reporter | Root |
| title | iOS/macOS Remote code execution triggered by malformed GIF in ImageIO framework(CVE-2017-2416) |