Security News

Security researchers investigating a bug that crashed the Wifi service on iPhones found that it could be exploited for remote code execution without user interaction. When initially disclosed, the bug could disable an iPhone's WiFi connection after trying to connect to a network with a name that included a special character.

Schou set up a Wi-Fi access point with a network name of %p%s%s%s%s%n, and then deliberately connected his iPhone to it in order to check for what are known as format string vulnerabilities. The name format string vulnerability comes from a standard, widely-used system function, found in almost every operating system, known as printf(), shorthand for format and print data.

NETGEAR announced the availability of the fourth member in its Insight Managed WiFi 6 Access Points, the Insight Managed WiFi 6 AX6000 Tri-band Multi-gig Access Point, designed to provide the ultimate WiFi performance for small and medium businesses. This new tri-band access point brings next-generation premium WiFi 6 performance to small and medium businesses, delivering up to 40% higher1 speeds to each connected device as compared to WiFi 5.

Joining a Wi-Fi network with a specific sequence of characters in its SSID name will break wireless connectivity for iOS devices. On Friday, Carl Schou, a security researcher in Denmark, reported that his iPhone lost its Wi-Fi capability after attempting to connect to a Wi-Fi network named "%p%s%s%s%s%n".

FUD is spreading about a weirdly named personal network that a reverse engineer stumbled across and which he said "Permanently" wrecked his iPhone's Wi-Fi. TL;DR version: The twitching inflicted on his iPhone, which he demonstrated in the 4-second Tweet below, wasn't permanent. As replies to the initial post pointed out, an iPhone's Wi-Fi can be restored by resetting network settings.
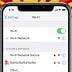
A wireless network naming bug has been discovered in Apple's iOS operating system that effectively disables an iPhone's ability to connect to a Wi-Fi network. The issue was spotted by security researcher Carl Schou, who found that the phone's Wi-Fi functionality gets permanently disabled after joining a Wi-Fi network with the unusual name "%p%s%s%s%s%n" even after rebooting the phone or changing the network's name.

A new iPhone bug has come to light that breaks your iPhone's wireless functionality by merely connecting to a specific WiFi hotspot. Once triggered, the bug would render your iPhone unable to establish a WiFi connection, even if it is rebooted or the WiFi hotspot is renamed.

A new iPhone bug has come to light that breaks your iPhone's wireless functionality by merely connecting to a specific WiFi hotspot. Once triggered, the bug would render your iPhone unable to establish a WiFi connection, even if it is rebooted or the WiFi hotspot is renamed.

Organizations can only deploy today's Wi-Fi 6 access points and 5G small cell access nodes where AC power is available or if their switch can deliver both power and data to them as required. Microchip Technology has created a more flexible and cost-effective alternative with the first multiport Power over Ethernet power sourcing equipment injector, also known as a midspan, that enables any multigigabit switch to support these devices' high powering needs and data rates, with no network configuration or downtime necessary.

Zyxel Communications announced the upcoming launch of a new WiFi 6 series, the DX3300, DX3301, EX3300, EX3301 and WX3100. This new offering will be one of Zyxel's most cost-competitive product series for migration to WiFi 6 Mesh and is a great choice for service providers who want to offer these capabilities under an existing copper or fiber infrastructure.