Security News

The first flaw concerns leak of names of private npm packages on the npmjs.com's 'replica' server-feeds from which are consumed by third-party services. ' The leak exposed a list of names of private npm packages, but not the content of these packages during the maintenance window.
In what's yet another instance of supply chain attack targeting open-source software repositories, two popular NPM packages with cumulative weekly downloads of nearly 22 million were found to be compromised with malicious code by gaining unauthorized access to the respective developer's accounts. The two libraries in question are "Coa," a parser for command-line options, and "Rc," a configuration loader, both of which were tampered by an unidentified threat actor to include "Identical" password-stealing malware.
In what's yet another instance of supply chain attack targeting open-source software repositories, two popular NPM packages with cumulative weekly downloads of nearly 22 million were found to be compromised with malicious code by gaining unauthorized access to the respective developer's accounts. The two libraries in question are "Coa," a parser for command-line options, and "Rc," a configuration loader, both of which were tampered by an unidentified threat actor to include "Identical" password-stealing malware.

Popular npm library 'coa' was hijacked today with malicious code injected into it, ephemerally impacting React pipelines around the world. Today, developers around the world were left surprised to notice new releases for npm library 'coa'-a project that hasn't been touched for years, unexpectedly appear on npm.

Popular npm library 'coa' was hijacked today with malicious code injected into it, ephemerally impacting React pipelines around the world. Today, developers around the world were left surprised to notice new releases for npm library 'coa'-a project that hasn't been touched for years, unexpectedly appear on npm.

Apple fixes security feature bypass in macOSApple has delivered a barrage of security updates for most of its devices this week, and among the vulnerabilities fixed are CVE-2021-30892, a System Integrity Protection bypass in macOS, and CVE-2021-30883, an iOS flaw that's actively exploited by attackers. Good security habits: Leveraging the science behind how humans develop habitsIn this interview with Help Net Security, George Finney, CSO at Southern Methodist University, explains what good security habits are, how to successfully implement them and why are they important.
Malicious actors have yet again published two more typosquatted libraries to the official NPM repository that mimic a legitimate package from Roblox, the game company, with the goal of...

Security firm Sonatype on Wednesday said it had spotted two related malicious NPM libraries that were named so they might be mistaken for a popular legitimate module that serves as a Roblox API wrapper. Js, a Roblox game API wrapper available on NPM and as a standalone download. Roblox is a gaming platform with more than 40 million daily active users.

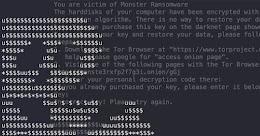
Malicious NPM packages pretending to be Roblox libraries are delivering ransomware and password-stealing trojans on unsuspecting users. In a new report by open source security firm Sonatype with further analysis by BleepingComputer, these malicious NPMs are infecting victims with an MBRLocker ransomware that impersonates the notorious GoldenEye ransomware, trollware, and a password stealing trojan.

The US government's Cybersecurity and Infrastructure Security Agency has warned developers that a version of the ua-parser-js JavaScript library, available via NPM, was infected with data-stealing and cryptocurrency-mining malware. The NPM account hosting it was seemingly compromised by miscreants, who modified the package so that when installed, it would bring in various bits of malware on whatever system was running the code.