Security News

Threat actors affiliated with the Democratic People's Republic of Korea (also known as North Korea) have plundered at least $600 million in cryptocurrency in 2023. The DPRK "was responsible for...

Updated The offensive cyber unit linked to Russia's Foreign Intelligence Service is exploiting the critical vulnerability affecting the JetBrains TeamCity CI/CD server at scale, and has been since September, authorities warn. The exploit in TeamCity could give attackers enough access to manipulate a software's source code, sign certificates, and compile and deploy processes, the advisory says.

North Korean-backed state hackers have stolen an estimated $3 billion in a long string of hacks targeting the cryptocurrency industry over the last six years since January 2017. "Since 2017, North Korea has significantly increased its focus on the cryptocurrency industry, stealing an estimated $3 billion worth of cryptocurrency," Recorded Future analysts said.

The Treasury Department's Office of Foreign Assets Control has sanctioned the North Korean-backed Kimsuky hacking group for stealing intelligence in support of the country's strategic goals. OFAC has also sanctioned eight North Korean agents for facilitating sanctions evasion and supporting their country's weapons of mass destruction programs.

Threat actors from the Democratic People's Republic of Korea (DPRK) are increasingly targeting the cryptocurrency sector as a major revenue generation mechanism since at least 2017 to get around...

Kim’s cyber cronies becoming more active, sophisticated in attempts to pwn global orgs The national cybersecurity organizations of the UK and the Republic of Korea (ROK) have issued a joint...

That GitHub repo an interviewer wants you to work on could be malware Palo Alto Networks' Unit 42 has detailed a pair of job market hacking schemes linked to state-sponsored actors in North Korea:...

Months of work reveals how this tricky malware family targets... the financial services sector A brand-new macOS malware strain from North Korean state-sponsored hackers has been spotted in the wild.…

As much as $7 billion in cryptocurrency has been illicitly laundered through cross-chain crime, with the North Korea-linked Lazarus Group linked to the theft of roughly $900 million of those...
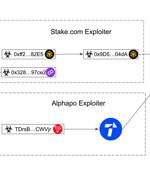
The North Korea-affiliated Lazarus Group has stolen nearly $240 million in cryptocurrency since June 2023, marking a significant escalation of its hacks. According to multiple reports from Certik, Elliptic, and ZachXBT, the infamous hacking group is said to be suspected behind the theft of $31 million in digital assets from the CoinEx exchange on September 12, 2023.