Security News

The 'security issue' was caused by a 9.8-rated Magento flaw Adobe patched back in June Bad news for anyone who purchased a Cisco hoodie earlier this month: Suspected Russia-based attackers...
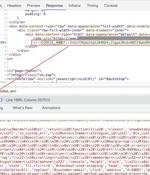
A sophisticated Magecart campaign has been observed manipulating websites' default 404 error page to conceal malicious code in what's been described as the latest evolution of the attacks. The...
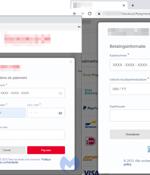
An ongoing Magecart campaign has attracted the attention of cybersecurity researchers for leveraging realistic-looking fake payment screens to capture sensitive data entered by unsuspecting users. "The remarkable thing here is that the skimmer looks more authentic than the original payment page."

In this Help Net Security video, Angel Grant, VP of Security, F5, explains what Magecart attacks are and how they have evolved over the years. Grant illustrates how cybercriminals are leveraging such attacks, and offers defense tips.

Three restaurant ordering platforms MenuDrive, Harbortouch, and InTouchPOS were the target of two Magecart skimming campaigns that resulted in the compromise of at least 311 restaurants. "The online ordering platforms MenuDrive and Harbortouch were targeted by the same Magecart campaign, resulting in e-skimmer infections on 80 restaurants using MenuDrive and 74 using Harbortouch," cybersecurity firm Recorded Future revealed in a report.

Magecart campaigns have been skimming payment-card credentials of unsuspecting customers using three online restaurant-ordering systems, affecting about 300 restaurants that use the services and compromising tens of thousands of cards so far, researchers have found. Two separate ongoing Magecart campaigns have injected e-skimmer scripts into the online ordering portals of restaurants using three separate platforms: MenuDrive, Harbortouch, and InTouchPOS, researchers from Recorded Future revealed in a blog post this week.

A newly discovered Magecart skimming campaign has its roots in a previous attack activity going all the way back to November 2021. To that end, it has come to light that two malware domains identified as hosting credit card skimmer code - "Scanalytic[.]org" and "Js.staticounter[.]net" - are part of a broader infrastructure used to carry out the intrusions, Malwarebytes said in a Tuesday analysis.

Analysts have found the source of a mass breach of over 500 e-commerce stores running the Magento 1 platform and involves a single domain loading a credit card skimmer on all of them. Sansec's subsequent investigation unveiled that the attackers abused a known vulnerability in the Quickview plugin to inject rogue Magento admin users that could then run code with the highest privileges.
Segway, maker of the iconic - and much-spoofed - personal motorized transporter familiar from guided city tours everywhere, has been serving up a nasty credit-card harvesting skimmer via its website - likely linked to Magecart Group 12. Magecart is a loose umbrella term encompassing various affiliated groups of financially motivated cybercriminals who all employ a similar skimming malware to harvest information - in particular payment-card information - that shoppers enter into checkout pages on eCommerce websites.

Some of the world's largest companies across retail, banking, healthcare, energy and many other sectors, including Fortune 500, Global 500 and governments are failing to prevent Magecart attacks, Cyberpion research revealed. Magecart is the common name for a style of cyber attack in which hackers compromise third party code to steal, or scrape, information such as credit card data from web-applications or websites that incorporate the code.