Security News

Boffins based in Germany and Austria have found a flaw in AMD's SEV trusted execution environment that makes it less than trustworthy. A successful attack - which assumes an attacker is running a malicious hypervisor protected by AMD SEV - could allow arbitrary code execution within a guest VM, the exposure of sensitive data, or privilege escalation.
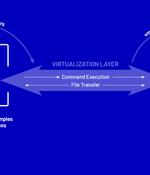
Threat actors have been found deploying never-before-seen post-compromise implants in VMware's virtualization software to seize control of infected systems and evade detection. Google's Mandiant threat intelligence division referred to it as a "Novel malware ecosystem" that impacts VMware ESXi, Linux vCenter servers, and Windows virtual machines, allowing attackers to maintain persistent access to the hypervisor as well as execute arbitrary commands.

Unknown attackers wielding novel specialized malware have managed to compromise VMware ESXi hypervisors and guest Linux and Windows virtual machines, Mandiant threat analysts have discovered. VirtualGATE is a utility program that incorporates a memory-only dropper and a payload that can run commands from a hypervisor host on a guest virtual machine, or between guest virtual machines on the same hypervisor host.

The developers of several major operating systems and hypervisors misinterpreted documentation from Intel and introduced a potentially serious vulnerability to their products. read more