Security News

A former IT security analyst at Oxford Biomedica has admitted, five years after the fact, to turning to the dark side - by hijacking a cyber attack against his own company in an attempt to divert any ransom payments to himself. Ashley Liles, of Letchworth Garden City, Hertfordshire, pleaded guilty at Reading Crown Court to blackmail and unauthorized access to a computer with intent to commit other offences on May 17 following an investigation by the South East Regional Organised Crime Unit.

Standardization Forum in the Netherlands, a research and advising organization that serves the public sector on the use open standards, announced that all communication devices managed by the Dutch government must use the RPKI standard by 2024. RPKI certificates are stored centrally and kept public, allowing network providers from anywhere in the world to validate internet traffic routes.

Google has stepped in to remove a bogus Chrome browser extension from the official Web Store that masqueraded as OpenAI's ChatGPT service to harvest Facebook session cookies and hijack the accounts. The "ChatGPT For Google" extension, a trojanized version of a legitimate open source browser add-on, attracted over 9,000 installations since March 14, 2023, prior to its removal.
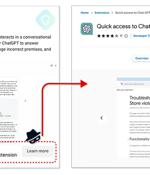
A fake ChatGPT-branded Chrome browser extension has been found to come with capabilities to hijack Facebook accounts and create rogue admin accounts, highlighting one of the different methods cyber criminals are using to distribute malware. "By hijacking high-profile Facebook business accounts, the threat actor creates an elite army of Facebook bots and a malicious paid media apparatus," Guardio Labs researcher Nati Tal said in a technical report.

An active malware campaign has set its sights on Facebook and YouTube users by leveraging a new information stealer to hijack the accounts and abuse the systems' resources to mine cryptocurrency. Bitdefender is calling the malware S1deload Stealer for its use of DLL side-loading techniques to get past security defenses and execute its malicious components.

More than 4,000 public-facing Sophos firewalls remain vulnerable to a critical remote code execution bug disclosed last year and patched months later, according to security researchers. The flaw, CVE-2022-3236, had already been exploited as a zero-day when Sophos published a security advisory about the vulnerability in September 2022.

Meta Platforms is said to have fired or disciplined over two dozen employees and contractors over the past year for allegedly compromising and taking over user accounts, The Wall Street Journal reported Thursday. Included among those fired were contractors who worked as security guards at the social media firm's facilities and were given access to an internal tool that allowed employees to help "Users they know" gain access to accounts after forgetting their passwords, or had their accounts locked out.

The holidays are just around the corner, and the competition for consumer attention and dollars promises to be fierce. According to Akamai research, up to 20% of potential online retail customers have their shopping experience disrupted - or worse, diverted to malicious websites - through audience hijacking.
A newly discovered evasive malware leverages the Secure Shell cryptographic protocol to gain entry into targeted systems with the goal of mining cryptocurrency and carrying out distributed denial-of-service attacks. Dubbed KmsdBot by the Akamai Security Intelligence Response Team, the Golang-based malware has been found targeting a variety of companies ranging from gaming to luxury car brands to security firms.
A PHP version of an information-stealing malware called Ducktail has been discovered in the wild being distributed in the form of cracked installers for legitimate apps and games, according to the latest findings from Zscaler. "Like older versions, the latest version also aims to exfiltrate sensitive information related to saved browser credentials, Facebook account information, etc.," Zscaler ThreatLabz researchers Tarun Dewan and Stuti Chaturvedi said.