Security News

The cryptojacking group known as TeamTNT is suspected to be behind a previously undiscovered strain of malware used to mine Monero cryptocurrency on compromised systems. Specifically, the early phase of the attack chain involved the use of a cryptocurrency miner, which the cloud security firm suspected was deployed as a decoy to conceal the detection of data exfiltration.

Cybersecurity researchers have discovered the first-ever illicit cryptocurrency mining campaign used to mint Dero since the start of February 2023. "The novel Dero cryptojacking operation concentrates on locating Kubernetes clusters with anonymous access enabled on a Kubernetes API and listening on non-standard ports accessible from the internet," CrowdStrike said in a new report shared with The Hacker News.

The first known cryptojacking operation mining the Dero coin has been found targeting vulnerable Kubernetes container orchestrator infrastructure with exposed APIs. The researchers say the attacks start with the threat actors scanning exposed, vulnerable Kubernetes clusters with authentication set to -anonymous-auth=true, allowing anyone anonymous access to the Kubernetes API. After gaining access to the API, the threat actors will deploy a DaemonSet named "Proxy-api" that allows the attackers to engage the resources of all nodes in the cluster simultaneously and mine Dero using the available resources.

The infamous cryptocurrency miner group called 8220 Gang has been observed using a new crypter called ScrubCrypt to carry out cryptojacking operations. According to Fortinet FortiGuard Labs, the attack chain commences with successful exploitation of susceptible Oracle WebLogic servers to download a PowerShell script that contains ScrubCrypt.
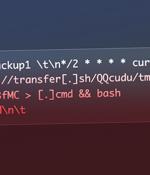
Misconfigured Redis database servers are the target of a novel cryptojacking campaign that leverages a legitimate and open source command-line file transfer service to implement its attack. The attack chain commences with targeting insecure Redis deployments, followed by registering a cron job that leads to arbitrary code execution when parsed by the scheduler.
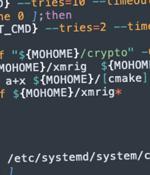
A new cryptojacking campaign has been uncovered targeting vulnerable Docker and Kubernetes infrastructures as part of opportunistic attacks designed to illicitly mine cryptocurrency. Cybersecurity company CrowdStrike dubbed the activity Kiss-a-dog, with its command-and-control infrastructure overlapping with those associated with other groups like TeamTNT, which are known to strike misconfigured Docker and Kubernetes instances.

The developer of the AstraLocker ransomware code is reportedly ceasing operations and turning attention to the far simpler art and crime of cryptojacking. The developer of AstraLocker posted a ZIP folder containing decryptors for the AstraLocker ransomware via VirusTotal, which Bleeping Computer said are legit.

The WatchDog hacking group is conducting a new cryptojacking campaign with advanced techniques for intrusion, worm-like propagation, and evasion of security software. The hacking group targets exposed Docker Engine API endpoints and Redis servers and can quickly pivot from one compromised machine to the entire network.

A man found guilty of using the Coinhive cryptojacking script to mine Monero on users' PCs while they browsed the web has been cleared by Japan's Supreme Court on the grounds that crypto mining software is not malware. Tokyo High Court ruled against the defendant, 34-year-old Seiya Moroi, on charges of keeping electromagnetic records of an unjust program.

TrapX Security launched TrapX DeceptionGrid 7.2 featuring a new capability to protect containerized environments such as Kubernetes. TrapX DeceptionGrid secures container environments across on-premises and cloud infrastructures, independent of attack vectors.