Security News
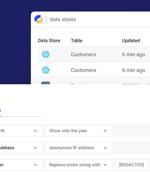
This is not the case when it comes to sensitive data sitting in production or analytic databases, data warehouses or data lakes. This article examines how Satori, a data security platform, gives control of the sensitive data in databases, data warehouses and data lakes to the security teams.

It had an Ethernet connection to the ship LAN but was also connected to a Windows console on the bridge which was so bright at night the crew had covered it up. The assumption had been that it was...

Matt Peters of Expel Describes Hybrid Approaches to Security OperationsFor a managed security service provider to deliver maximum value for customers, it needs to provide a hybrid approach that...

Jackpotting Attacks Cost Banks Nearly $2 MillionFraudsters are now gingerly testing the waters in central and Western Europe with attacks that drain cash machines of their funds, according to a...


The efforts of a number of EU Member States and Norway, supported by Europol’s European Cybercrime Centre (EC3) and the Joint Cybercrime Action Taskforce (J-CAT), culminated in the arrest of 27...



Upon discovery of a cyberattack, forensic experts look inside the compromised network’s various logs to locate and analyze tracks left by the attacker. Logs are the baseline information required...

Waterfall Security Solutions announced the launch of the Waterfall BlackBox, developed to maintain the integrity of log repositories in the event of a cyber attack. Based on Waterfall’s patented...