Security News > 2024 > August > Industrial Remote Access Tool Ewon Cosy+ Vulnerable to Root Access Attacks
Security vulnerabilities have been disclosed in the industrial remote access solution Ewon Cosy+ that could be abused to gain root privileges to the devices and stage follow-on attacks.
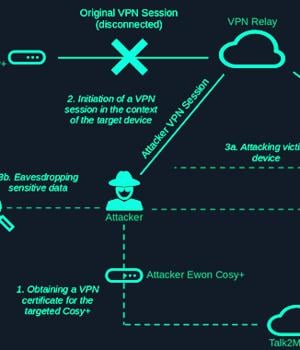
The elevated access could then be weaponized to decrypt encrypted firmware files and encrypted data such as passwords in configuration files, and even get correctly signed X.509 VPN certificates for foreign devices to take over their VPN sessions.
Ewon Cosy+'s architecture involves the use of a VPN connection that's routed to a vendor-managed platform called Talk2m via OpenVPN. Technicians can remotely connect to the industrial gateway by means of a VPN relay that occurs through OpenVPN. The Germany-based pentest company said it was able to uncover an operating system command injection vulnerability and a filter bypass that made it possible to obtain a reverse shell by uploading a specially crafted OpenVPN configuration.
An attacker could have subsequently taken advantage of a persistent cross-site scripting vulnerability and the fact that the device stores the Base64-encoded credentials of the current web session in an unprotected cookie-named credentials to gain administrative access and ultimately root it.
"An unauthenticated attacker can gain root access to the Cosy+ by combining the found vulnerabilities and e.g., waiting for an admin user to log in to the device," Abrell said.
The attack chain could then be extended further to set up persistence, access firmware-specific encryption keys, and decrypt the firmware update file.
News URL
https://thehackernews.com/2024/08/industrial-remote-access-tool-ewon-cosy.html