Security News > 2024 > August > Sonos Speaker Flaws Could Have Let Remote Hackers Eavesdrop on Users
Cybersecurity researchers have uncovered weaknesses in Sonos smart speakers that could be exploited by malicious actors to clandestinely eavesdrop on users.
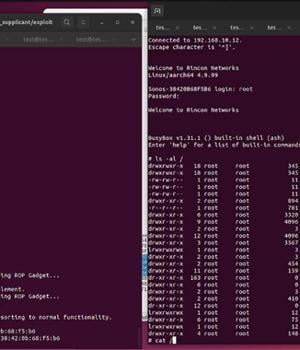
Successful exploitation of one of these flaws could allow a remote attacker to obtain covert audio capture from Sonos devices by means of an over-the-air attack.
NCC Group, which reverse-engineered the boot process to achieve remote code execution on Sonos Era-100 and the Sonos One devices, said CVE-2023-50809 is the result of a memory corruption vulnerability in the Sonos One's wireless driver, which is a third-party chipset manufactured by MediaTek.
The other flaw, CVE-2023-50810, relates to a chain of vulnerabilities identified in the secure boot process to breach Era-100 devices, effectively making it possible to circumvent security controls to allow for unsigned code execution in the context of the kernel.
"In the case of the secure boot weaknesses, then it is important to validate and perform testing of the boot chain to ensure that these weaknesses are not introduced. Both hardware and software-based attack vectors should be considered."
As a result, PKfail permits bad actors to run arbitrary code during the boot process, even with Secure Boot enabled, allowing them to sign malicious code and deliver a UEFI bootkit, such as BlackLotus.
News URL
https://thehackernews.com/2024/08/new-flaws-in-sonos-smart-speakers-allow.html