Security News > 2024 > August > China-Linked Hackers Compromise ISP to Deploy Malicious Software Updates
The China-linked threat actor known as Evasive Panda compromised an unnamed internet service provider to push malicious software updates to target companies in mid-2023, highlighting a new level of sophistication associated with the group.
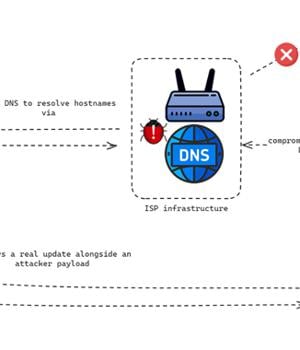
It was also found to have targeted an international non-governmental organization in Mainland China with MgBot delivered via update channels of legitimate applications like Tencent QQ. While it was speculated that the trojanized updates were either the result of a supply chain compromise of Tencent QQ's update servers or a case of an adversary-in-the-middle attack, Volexity's analysis confirms it's the latter stemming from a DNS poisoning attack at the ISP level.
Specifically, the threat actor is said to be altering DNS query responses for specific domains tied to automatic software update mechanisms, going after software that used insecure update mechanisms, such as HTTP, or did not enforce adequate integrity checks of the installers.
"It was discovered that StormBamboo poisoned DNS requests to deploy malware via an HTTP automatic update mechanism and poison responses for legitimate hostnames that were used as second-stage, command-and-control servers," researchers Ankur Saini, Paul Rascagneres, Steven Adair, and Thomas Lancaster said.
The attack chains are fairly straightforward in that the insecure update mechanisms are abused to deliver either MgBot or MACMA depending on the operating system used.
"The attacker can intercept DNS requests and poison them with malicious IP addresses, and then use this technique to abuse automatic update mechanisms that use HTTP rather than HTTPS," the researchers said.
News URL
https://thehackernews.com/2024/08/china-linked-hackers-compromise-isp-to.html