Security News > 2024 > July > VMware ESXi Flaw Exploited by Ransomware Groups for Admin Access
A recently patched security flaw impacting VMware ESXi hypervisors has been actively exploited by "Several" ransomware groups to gain elevated permissions and deploy file-encrypting malware.
"A malicious actor with sufficient Active Directory permissions can gain full access to an ESXi host that was previously configured to use AD for user management by re-creating the configured AD group after it was deleted from AD," Broadcom-owned VMware noted in an advisory released in late June 2024.
In other words, escalating privileges on ESXi to the administrator was as simple as creating a new AD group named "ESX Admins" and adding any user to it, or renaming any group in the domain to "ESX Admins" and adding a user to the group or using an existing group member.
"VMware ESXi hypervisors joined to an Active Directory domain consider any member of a domain group named 'ESX Admins' to have full administrative access by default," researchers Danielle Kuznets Nohi, Edan Zwick, Meitar Pinto, Charles-Edouard Bettan, and Vaibhav Deshmukh said.
"This group is not a built-in group in Active Directory and does not exist by default. ESXi hypervisors do not validate that such a group exists when the server is joined to a domain and still treats any members of a group with this name with full administrative access, even if the group did not originally exist."
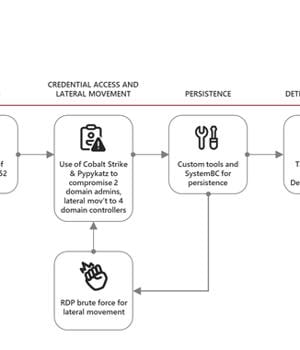
Subsequently, phases entailed the deployment of Cobalt Strike and Pypykatz, a Python version of Mimikatz, to steal domain administrator credentials and move laterally across the network, followed by dropping the SystemBC implant for persistence and abusing the ESXi admin access to deploy Black Basta.
News URL
https://thehackernews.com/2024/07/vmware-esxi-flaw-exploited-by.html