Security News > 2024 > July > 'Konfety' Ad Fraud Uses 250+ Google Play Decoy Apps to Hide Malicious Twins
Details have emerged about a "Massive ad fraud operation" that leverages hundreds of apps on the Google Play Store to perform a host of nefarious activities.
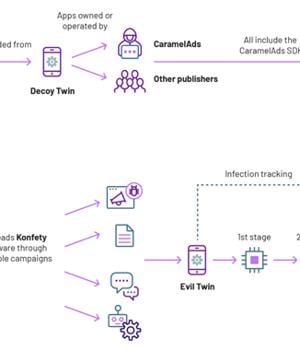
"Konfety represents a new form of fraud and obfuscation, in which threat actors operate 'evil twin' versions of 'decoy twin' apps available on major marketplaces," HUMAN's Satori Threat Intelligence Team said in a technical report shared with The Hacker News.
While the decoy apps, totaling more than 250 in number, are harmless and distributed via the Google Play Store, their respective "Evil twins" are disseminated through a malvertising campaign designed to facilitate ad fraud, monitor web searches, install browser extensions, and sideload APK files code onto users' devices.
The Konfety evil twin apps are said to be propagated via a malvertising campaign promoting APK mods and other software like Letasoft Sound Booster, with the booby-trapped URLs hosted on attacker-controlled domains, compromised WordPress sites, and other platforms that allow content uploads, including Docker Hub, Facebook, Google Sites, and OpenSea.
"These apps mimic their corresponding decoy twin apps by copying their app ID/package names and publisher IDs from the decoy twin apps."
"The network traffic derived from the evil twin applications is functionally identical to network traffic derived from the decoy twin applications; the ad impressions rendered by the evil twins use the package name of the decoy twins in the request."
News URL
https://thehackernews.com/2024/07/konfety-ad-fraud-uses-250-google-play.html