Security News > 2024 > July > CRYSTALRAY Hackers Infect Over 1,500 Victims Using Network Mapping Tool
A threat actor that was previously observed using an open-source network mapping tool has greatly expanded their operations to infect over 1,500 victims.
Sysdig, which is tracking the cluster under the name CRYSTALRAY, said the activities have witnessed a 10x surge, adding it includes "Mass scanning, exploiting multiple vulnerabilities, and placing backdoors using multiple security tools."
It has been described as a tool to carry out automatic network traversal using SSH private keys discovered on systems.
The abuse of the software by CRYSTALRAY was documented by the cybersecurity company earlier this February, with the tool deployed for lateral movement following the exploitation of known security flaws in public-facing Apache ActiveMQ and Atlassian Confluence instances.
Joshua Rogers, the developer behind SSH-Snake told The Hacker News at the time that the tool only automates what would have been otherwise manual steps, and called on companies to "Discover the attack paths that exist - and fix them."
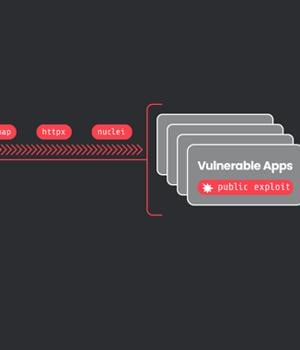
Some of the other tools employed by the attackers include asn, zmap, httpx, and nuclei in order to check if a domain is active and launch scans for vulnerable services such as Apache ActiveMQ, Apache RocketMQ, Atlassian Confluence, Laravel, Metabase, Openfire, Oracle WebLogic Server, and Solr.
News URL
https://thehackernews.com/2024/07/crystalray-hackers-infect-over-1500.html