Security News > 2024 > July > Hackers Exploiting Jenkins Script Console for Cryptocurrency Mining Attacks
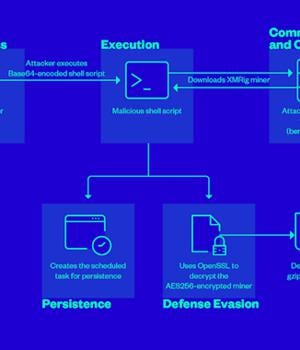
Cybersecurity researchers have found that it's possible for attackers to weaponize improperly configured Jenkins Script Console instances to further criminal activities such as cryptocurrency mining.
Jenkins, a popular continuous integration and continuous delivery platform, features a Groovy script console that allows users to run arbitrary Groovy scripts within the Jenkins controller runtime.
The console "Offers no administrative controls to stop a user once they are able to execute the Script Console from affecting all parts of the Jenkins infrastructure," reads the documentation.
"Granting a normal Jenkins user Script Console Access is essentially the same as giving them Administrator rights within Jenkins."
While access to Script Console is typically limited only to authenticated users with administrative permissions, misconfigured Jenkins instances could inadvertently make the "/script" endpoint accessible over the internet, making it ripe for exploitation by attackers looking to run dangerous commands.
Trend Micro said it found instances of threat actors exploiting the Jenkins Groovy plugin misconfiguration to execute a Base64-encoded string containing a malicious script that's designed to mine cryptocurrency on the compromised server by deploying a miner payload hosted on berrystore[.
News URL
https://thehackernews.com/2024/07/hackers-exploiting-jenkins-script.html
Related news
- Hackers Repurpose RansomHub's EDRKillShifter in Medusa, BianLian, and Play Attacks (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- North Korean hackers adopt ClickFix attacks to target crypto firms (source)
- Over 1,500 PostgreSQL Servers Compromised in Fileless Cryptocurrency Mining Campaign (source)
- PoisonSeed Exploits CRM Accounts to Launch Cryptocurrency Seed Phrase Poisoning Attacks (source)
- Russian hackers attack Western military mission using malicious drive (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Hackers abuse Zoom remote control feature for crypto-theft attacks (source)
- DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack (source)
- Lazarus hackers breach six companies in watering hole attacks (source)