Security News > 2024 > May > GHOSTENGINE Exploits Vulnerable Drivers to Disable EDRs in Cryptojacking Attack
2024-05-22 08:57
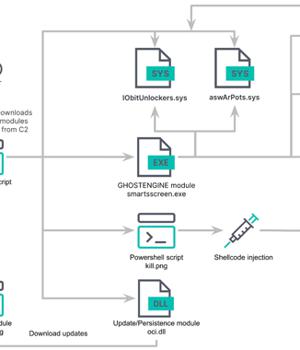
Cybersecurity researchers have discovered a new cryptojacking campaign that employs vulnerable drivers to disable known security solutions (EDRs) and thwart detection in what's called a Bring Your Own Vulnerable Driver (BYOVD) attack. Elastic Security Labs is tracking the campaign under the name REF4578 and the primary payload as GHOSTENGINE. Previous research from Chinese
News URL
https://thehackernews.com/2024/05/ghostengine-exploits-vulnerable-drivers.html
Related news
- PoisonSeed Exploits CRM Accounts to Launch Cryptocurrency Seed Phrase Poisoning Attacks (source)
- Craft CMS RCE exploit chain used in zero-day attacks to steal data (source)
- New "Bring Your Own Installer" EDR bypass used in ransomware attack (source)
- How cybercriminals exploit psychological triggers in social engineering attacks (source)
- Chinese Hackers Exploit Ivanti EPMM Bugs in Global Enterprise Network Attacks (source)