Security News > 2024 > May > China-Linked Hackers Adopt Two-Stage Infection Tactic to Deploy Deuterbear RAT
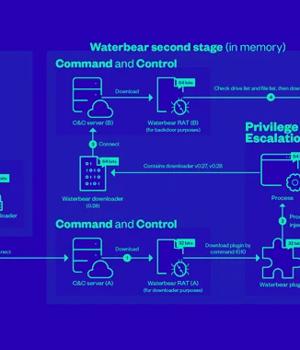
Interestingly, the RAT module is fetched twice from the attacker-controlled infrastructure, the first of which is just used to load the Waterbear plugin that subsequently launches a different version of the Waterbear downloader to retrieve the RAT module from another C&C server.
Put differently, the first Waterbear RAT serves as a downloader while the second Waterbear RAT functions as a backdoor, harvesting sensitive information from the compromised host through a set of 60 commands.
The infection pathway for Deuterbear is a lot similar to that of Waterbear in that it also implements two stages to install the RAT backdoor component, but also tweaks it to some extent.
The first stage, in this case, employs the loader to launch a downloader, which connects to the C&C server to fetch Deuterbear RAT in order to establish persistence by means of a second-stage loader via DLL side-loading.
Deuterbear RAT is also a more streamlined version of its predecessor, retaining only a subset of the commands in favor of a plugin-based approach to incorporate more functionality.
"SugarGh0st RAT is a remote access trojan, and is a customized variant of Gh0st RAT, an older commodity trojan typically used by Chinese-speaking threat actors," the company said.
News URL
https://thehackernews.com/2024/05/china-linked-hackers-adopt-two-stage.html
Related news
- Pakistan-Linked Hackers Expand Targets in India with CurlBack RAT and Spark RAT (source)
- Chinese hackers target Russian govt with upgraded RAT malware (source)
- Czech Republic Blames China-Linked APT31 Hackers for 2022 Cyberattack (source)
- China-Linked Hackers Exploit SAP and SQL Server Flaws in Attacks Across Asia and Brazil (source)