Security News > 2024 > April > Palo Alto Networks Discloses More Details on Critical PAN-OS Flaw Under Attack
2024-04-20 05:53
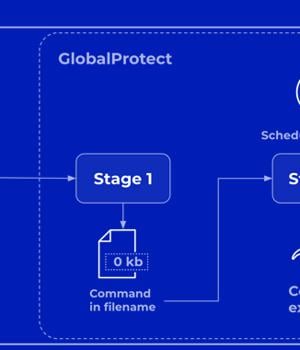
Palo Alto Networks has shared more details of a critical security flaw impacting PAN-OS that has come under active exploitation in the wild by malicious actors. The company described the vulnerability, tracked as CVE-2024-3400 (CVSS score: 10.0), as "intricate" and a combination of two bugs in versions PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 of the software. "In
News URL
https://thehackernews.com/2024/04/palo-alto-networks-discloses-more.html
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2024-04-12 | CVE-2024-3400 | Command Injection vulnerability in Paloaltonetworks Pan-Os A command injection as a result of arbitrary file creation vulnerability in the GlobalProtect feature of Palo Alto Networks PAN-OS software for specific PAN-OS versions and distinct feature configurations may enable an unauthenticated attacker to execute arbitrary code with root privileges on the firewall. Cloud NGFW, Panorama appliances, and Prisma Access are not impacted by this vulnerability. | 10.0 |