Security News > 2023 > August > NoFilter Attack: Sneaky Privilege Escalation Method Bypasses Windows Security
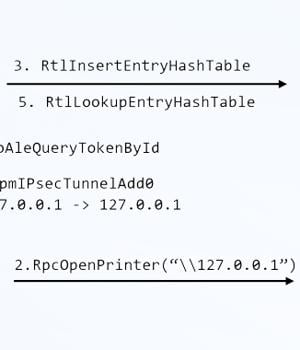
A previously undetected attack method called NoFilter has been found to abuse the Windows Filtering Platform to achieve privilege escalation in the Windows operating system.
"If an attacker has the ability to execute code with admin privilege and the target is to perform LSASS Shtinkering, these privileges are not enough," Ron Ben Yizhak, a security researcher at Deep Instinct, told The Hacker News.
The starting point of the research is an in-house tool called RPC Mapper the cybersecurity company used to map remote procedure call methods, specifically those that invoke WinAPI, leading to the discovery of a method named "BfeRpcOpenToken," which is part of WFP. WFP is a set of API and system services that's used to process network traffic and allow configuring filters that permit or block communications.
"The handle table of another process can be retrieved by calling NtQueryInformationProcess," Ben Yizhak said.
While access tokens serve to identify the user involved when a privileged task is executed, a piece of malware running in user mode can access tokens of other processes using specific functions and then use that token to launch a child process with SYSTEM privileges.
"The takeaway is that new attack vectors can be found by looking into built-in components of the OS, such as the Windows Filtering Platform," Ben Yizhak said, adding the methods "Avoid WinAPI that are monitored by security products."
News URL
https://thehackernews.com/2023/08/nofilter-attack-sneaky-privilege.html
Related news
- AI-Powered SaaS Security: Keeping Pace with an Expanding Attack Surface (source)
- EncryptHub linked to MMC zero-day attacks on Windows systems (source)
- WinRAR flaw bypasses Windows Mark of the Web security alerts (source)
- New TCESB Malware Found in Active Attacks Exploiting ESET Security Scanner (source)
- Microsoft: Windows 'inetpub' folder created by security fix, don’t delete (source)
- Don't delete that mystery empty folder. Windows put it there as a security fix (source)
- Windows NTLM vulnerability exploited in multiple attack campaigns (CVE-2025-24054) (source)
- Windows NTLM hash leak flaw exploited in phishing attacks on governments (source)
- Linux 'io_uring' security blindspot allows stealthy rootkit attacks (source)
- Windows "inetpub" security fix can be abused to block future updates (source)