Security News > 2023 > July > Azure AD Token Forging Technique in Microsoft Attack Extends Beyond Outlook, Wiz Reports
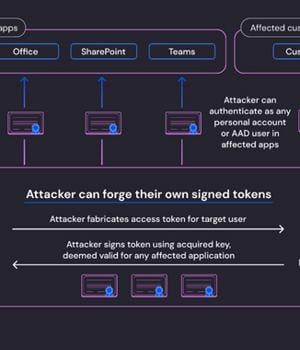
According to cloud security company Wiz, the inactive Microsoft account consumer signing key used to forge Azure Active Directory tokens to gain illicit access to Outlook Web Access and Outlook.com could also have allowed the adversary to forge access tokens for various types of Azure AD applications.
Wiz's analysis fills in some of the blanks, with the company discovering that "All Azure personal account v2.0 applications depend on a list of 8 public keys, and all Azure multi-tenant v2.0 applications with Microsoft account enabled depend on a list of 7 public keys."
"This led us to believe that although the compromised key acquired by Storm-0558 was a private key designed for Microsoft's MSA tenant in Azure, it was also able to sign OpenID v2.0 tokens for multiple types of Azure Active Directory applications," Wiz said.
"Storm-0558 seemingly managed to obtain access to one of several keys that were intended for signing and verifying AAD access tokens. The compromised key was trusted to sign any OpenID v2.0 access token for personal accounts and mixed-audience AAD applications."
Even worse, the acquired private key could have been weaponized to forge tokens to authenticate as any user to an affected application that trusts Microsoft OpenID v2.0 mixed audience and personal-accounts certificates.
"Identity provider's signing keys are probably the most powerful secrets in the modern world," Wiz security researcher Shir Tamari said.
News URL
https://thehackernews.com/2023/07/azure-ad-token-forging-technique-in.html
Related news
- Botnet targets Basic Auth in Microsoft 365 password spray attacks (source)
- CrowdStrike Security Report: Generative AI Powers Social Engineering Attacks (source)
- Microsoft fixes Outlook drag-and-drop broken by Windows updates (source)
- Microsoft names alleged credential-snatching 'Azure Abuse Enterprise' operators (source)
- Microsoft Exposes LLMjacking Cybercriminals Behind Azure AI Abuse Scheme (source)
- New ClickFix attack deploys Havoc C2 via Microsoft Sharepoint (source)
- Microsoft says button to restore classic Outlook is broken (source)
- Microsoft wouldn't look at a bug report without a video. Researcher maliciously complied (source)
- Microsoft Exchange Online outage affects Outlook web users (source)
- Hidden Threats: How Microsoft 365 Backups Store Risks for Future Attacks (source)